As the number of cyber attacks continues to rise, organizations need to keep their networks and data secure by staying informed about the latest vulnerabilities and patches. Recently, a significant vulnerability was discovered in the Cisco Identity Services Engine (ISE) software, known as CVE-2022-20822, which can allow attackers to gain access to restricted files on a device.
In this blog post, we'll take a closer look at this vulnerability and how InvGate Asset Management can help simplify the Patch Management process by identifying devices that are vulnerable and need to be updated.
If you're concerned about your device's security and want to learn more about CVE-2022-20822, keep reading!
About CVE-2022-20822
CVE-2022-20822 is a path traversal vulnerability in the web-based management interface of the Cisco Identity Services Engine (ISE) that could be exploited by an authenticated, remote attacker. ISE is a NAC solution that manages endpoint, user, and device access to network resources within a zero-trust architecture.
Path traversal vulnerabilities allow attackers to read and possibly write restricted files by inputting path traversal sequences like “…/” into the file or directory paths. This vulnerability could allow an authenticated attacker to list, download, and delete files on an affected device.
CVE-2022-20822 can be exploited by an attacker who sends a crafted HTTP request containing specific character sequences to a system that is susceptible to the vulnerability. Once successfully exploited, the attacker could gain access to specific files on the device, which would typically be inaccessible at their configured administrative level, and either read or delete them.
Cisco has released a patch to address the CVE-2022-20822 vulnerability. The patch is included in Cisco Identity Services Engine (ISE) software versions 3.1.4 and later. Cisco recommends that all users of the affected software upgrade to the latest version as soon as possible to protect against this vulnerability.
How to find devices exposed to CVE-2022-20822
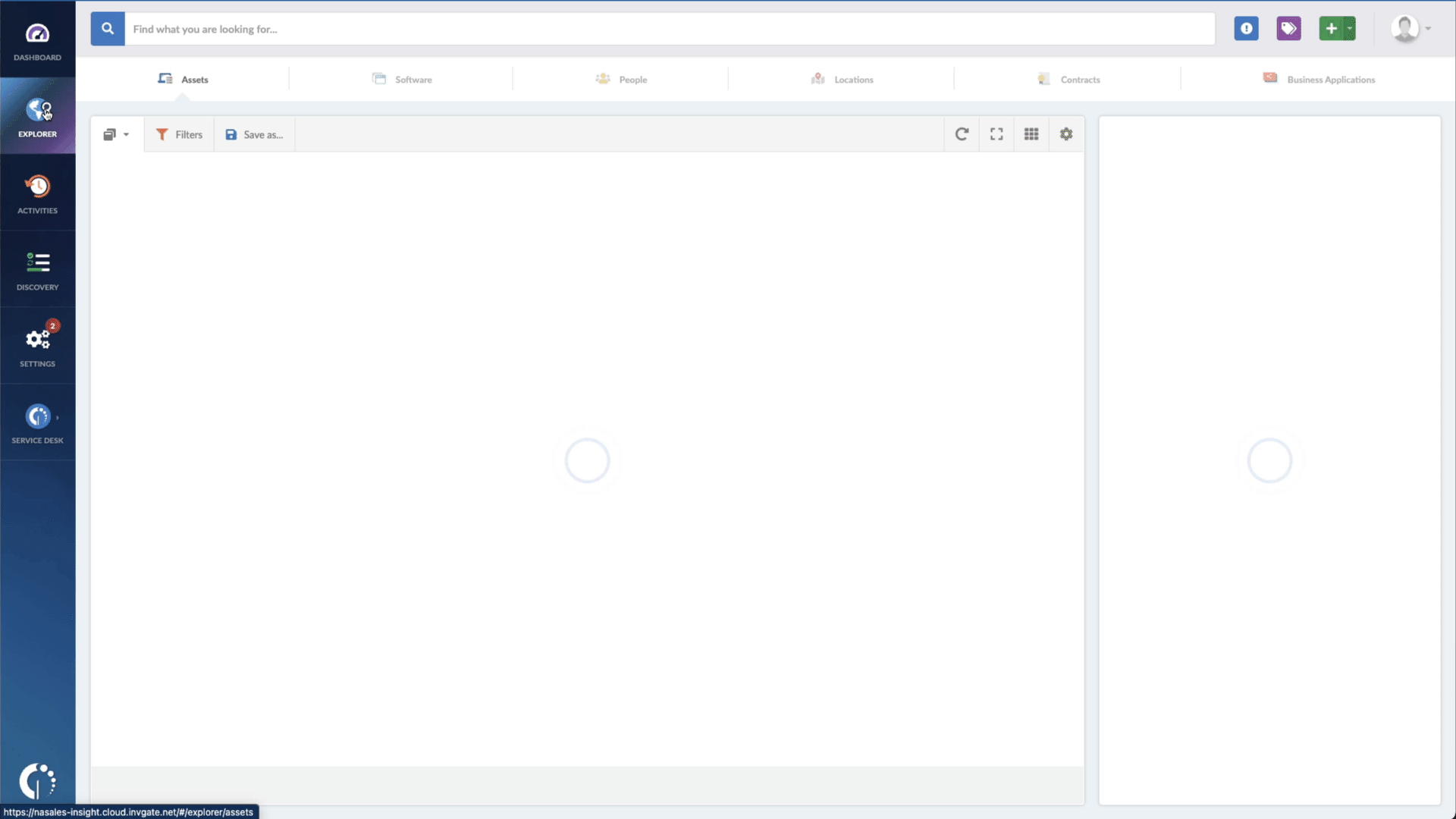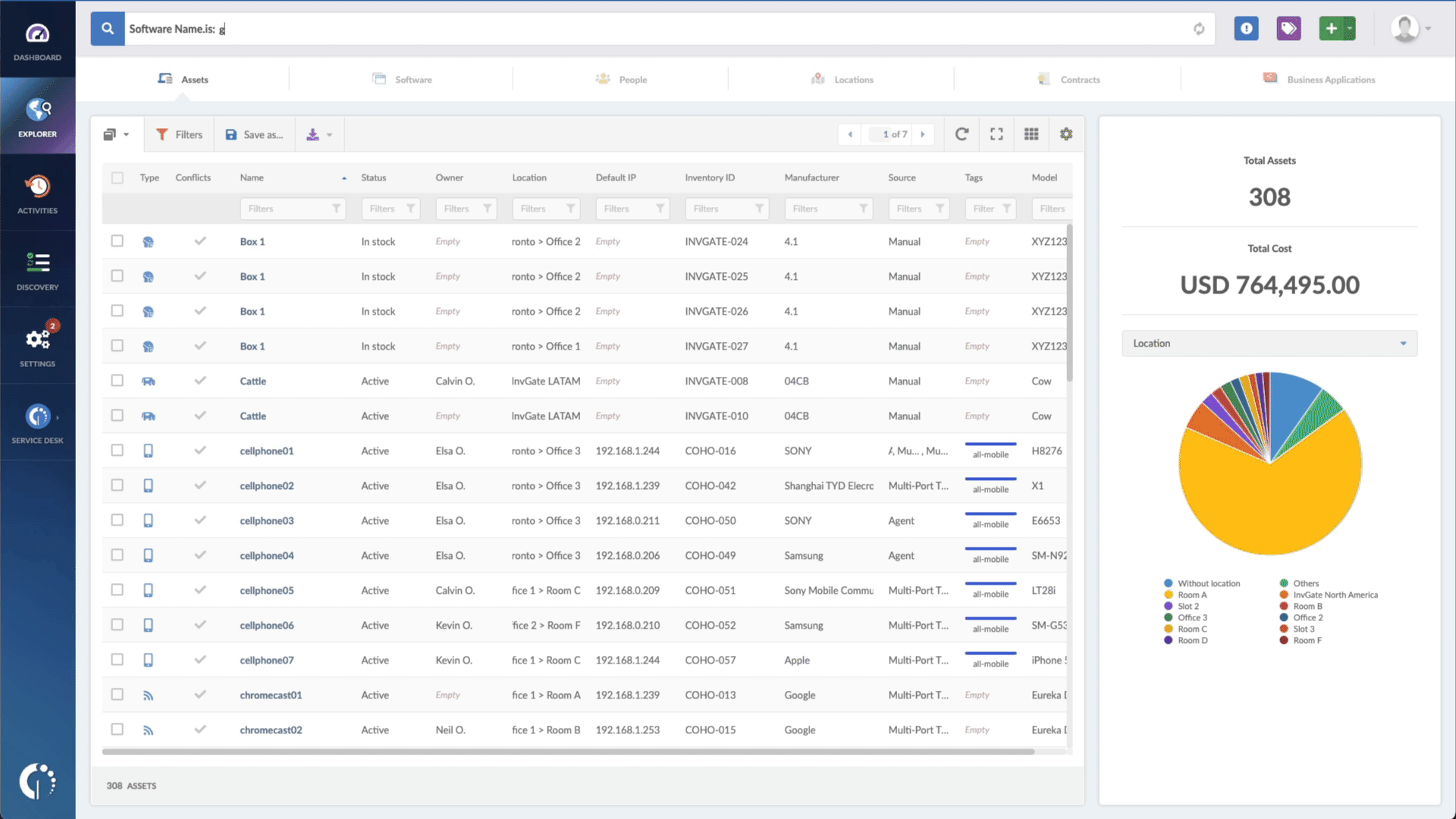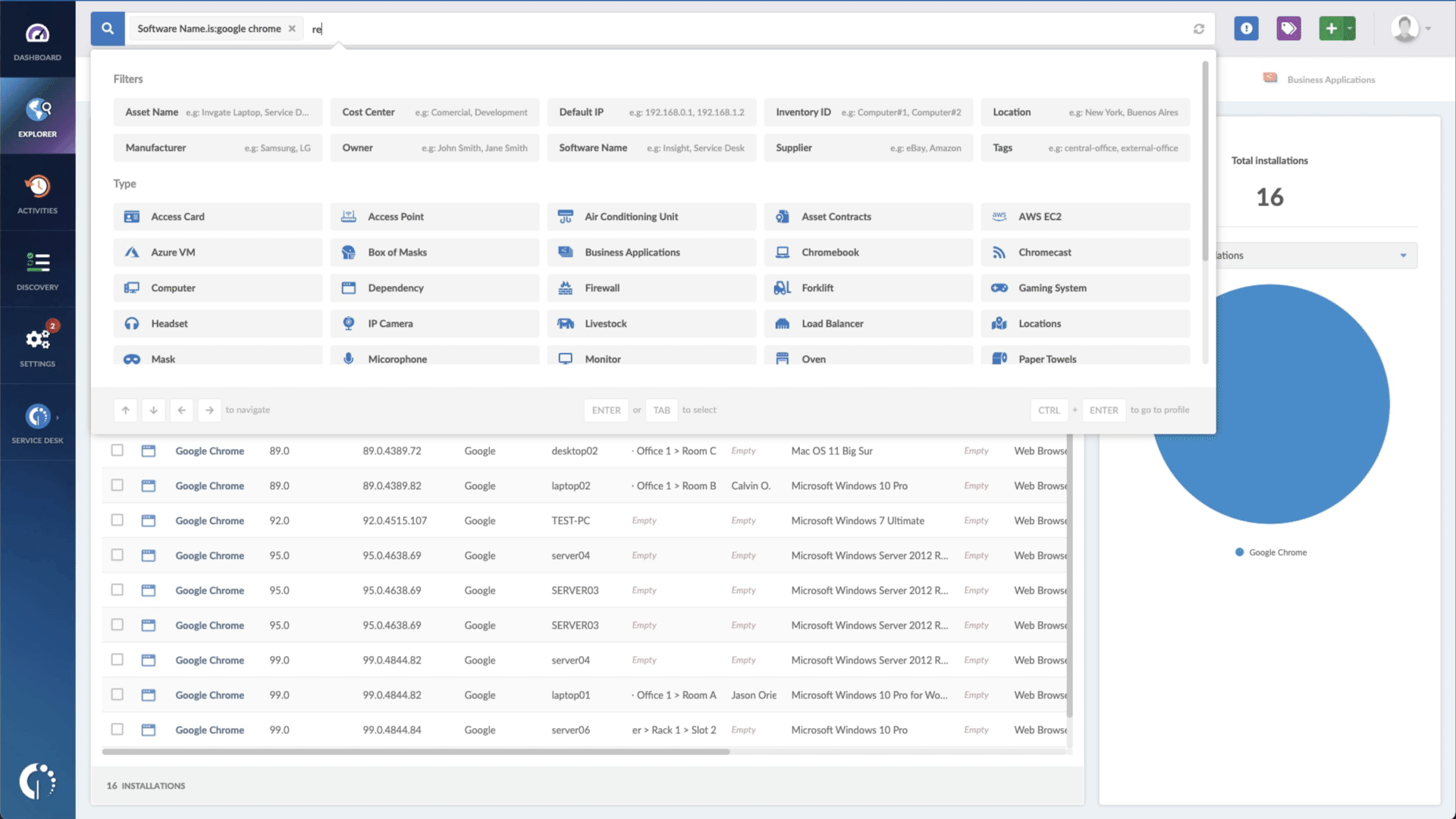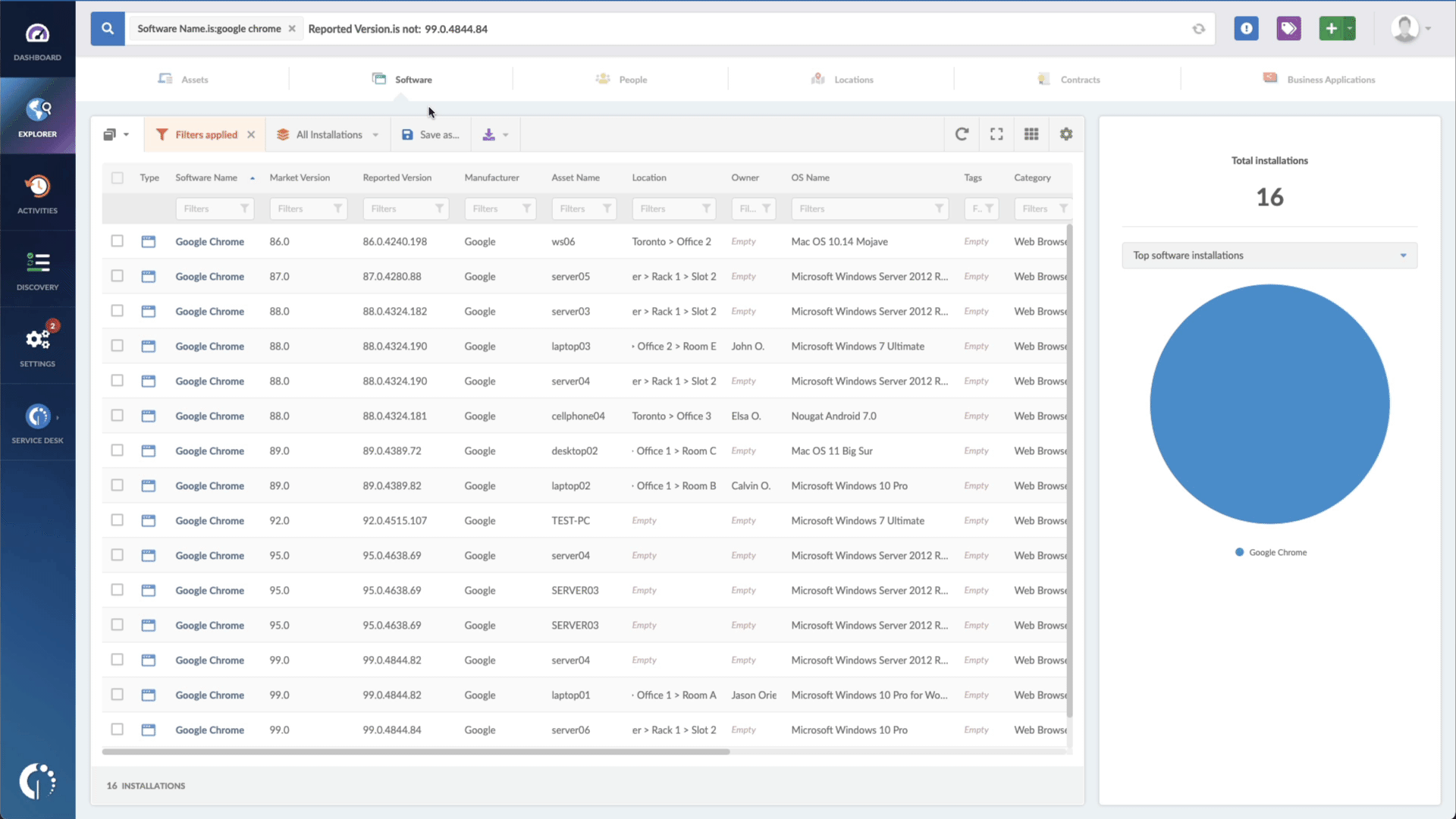
You can use InvGate Asset Management to find devices that are exposed to the CVE-2022-20822 vulnerability. The steps are as follows:
- Open InvGate Asset Management and go to the Explorer tab.
- In the Search bar, type “Software name, is:Cisco Identity Services Engine” to filter all devices that have this software installed.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Cisco’s patched version (3.1.4 and later).
Another vulnerability to note
In addition to the CVE-2022-20822 vulnerability, Cisco ISE is also affected by another vulnerability that organizations should be aware of. CVE-2022-20959 is a cross-site scripting (XSS) vulnerability that exists in the External RESTful Services (ERS) API of Cisco ISE.
The CVE-2022-20959 vulnerability can be exploited by an attacker who tricks an authenticated administrator of the web-based management interface into clicking a malicious link. Once clicked, the attacker can execute arbitrary script code in the context of the affected interface, potentially gaining access to sensitive information or performing unauthorized actions.
Cisco has released a patch to address this vulnerability in Cisco ISE software version 3.1.6 and later. To mitigate the risk posed by CVE-2022-20959, organizations should ensure they are using the latest version of Cisco ISE and apply the patch as soon as possible.
The bottom line
CVE-2022-20822 is a path traversal vulnerability that could allow an attacker to read or delete specific files on an affected device. It affects all versions of Cisco ISE software before version 3.1.4. Cisco has released a patch to address the vulnerability, and it is recommended that all users of the affected software upgrade to version 3.1.4 or later.
You can use InvGate Asset Management to simplify Patch Management and identify devices that are vulnerable to CVE-2022-20822. With InvGate Asset Management, you can quickly filter all devices that have Cisco ISE software installed and see which devices are missing the security patch. This feature allows IT teams to prioritize their patch management efforts and ensure that all devices are up to date, reducing the risk of a successful attack.
Request for free a 30-day trial and ensure that all devices in your network are up to date and secure against known vulnerabilities.