The discovery of the CVE-2021-42321 vulnerability in the Microsoft Exchange Server has raised significant concerns surrounding system security and data integrity. Exploiting this vulnerability allows authenticated threat actors to remotely execute code on vulnerable servers, potentially leading to unauthorized control over the affected systems.
In this article, we’ll delve into the details of CVE-2021-42321, outlining its potential risks and emphasizing the importance of promptly patching affected systems. To simplify the Patch Management process, InvGate Asset Management offers a valuable solution.
Continue reading to learn more about the CVE-2021-42321 vulnerability and how to safeguard your devices.
About CVE-2021-42321
CVE-2021-42321 is a remote code execution (RCE) vulnerability in Microsoft Exchange Server that affects on-premises servers running Microsoft Exchange 2016 and 2019, including those using Exchange Hybrid mode. This exploit enables authenticated threat actors to execute code remotely on vulnerable servers and launch an attack.
How does CVE-2021-42321 work?
The vulnerability is caused by a flaw in the way that Exchange handles user configuration data. An attacker can exploit this flaw by sending a specially crafted request to an Exchange server. This request can then be used to execute arbitrary code on the server.
What are CVE-2021-42321 risks?
An attacker who successfully exploits this vulnerability could gain full control of an Exchange server, allowing them to steal data, install malware, or disrupt email service.
Is CVE-2021-42321 fixed?
Yes, Microsoft has released a patch for CVE-2021-42321. Administrators should apply it as soon as possible to protect their servers from attack. The latest version of the software that includes the patch is:
- Microsoft Exchange Server 2016: CU23
- Microsoft Exchange Server 2019: CU12
How to find devices exposed to CVE-2021-42321
With InvGate Asset Management, you can quickly pinpoint devices impacted by the CVE-2021-42321 vulnerability. The following instructions outline the necessary actions to take>
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Microsoft Exchange Server” to filter all devices with this software.
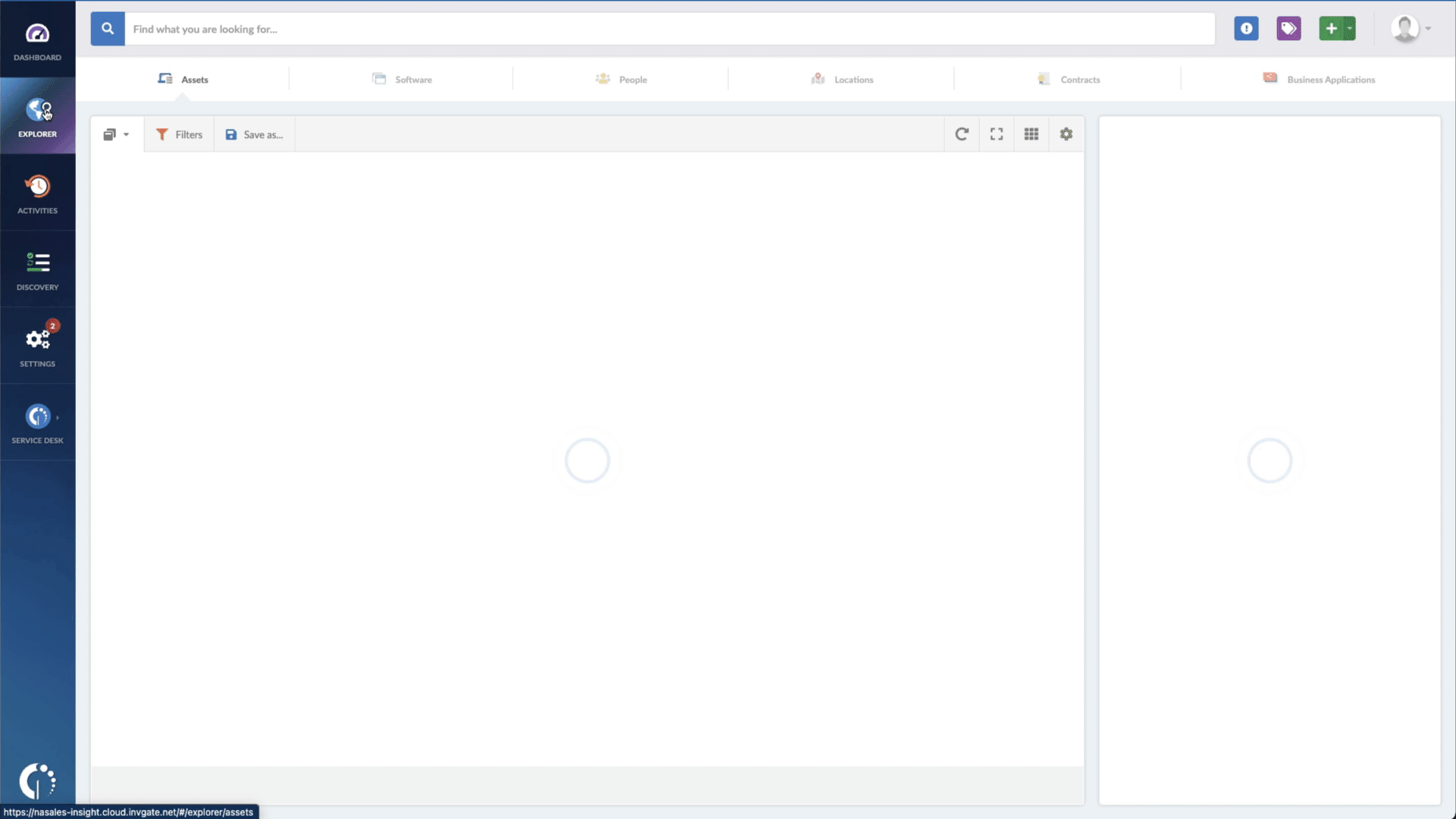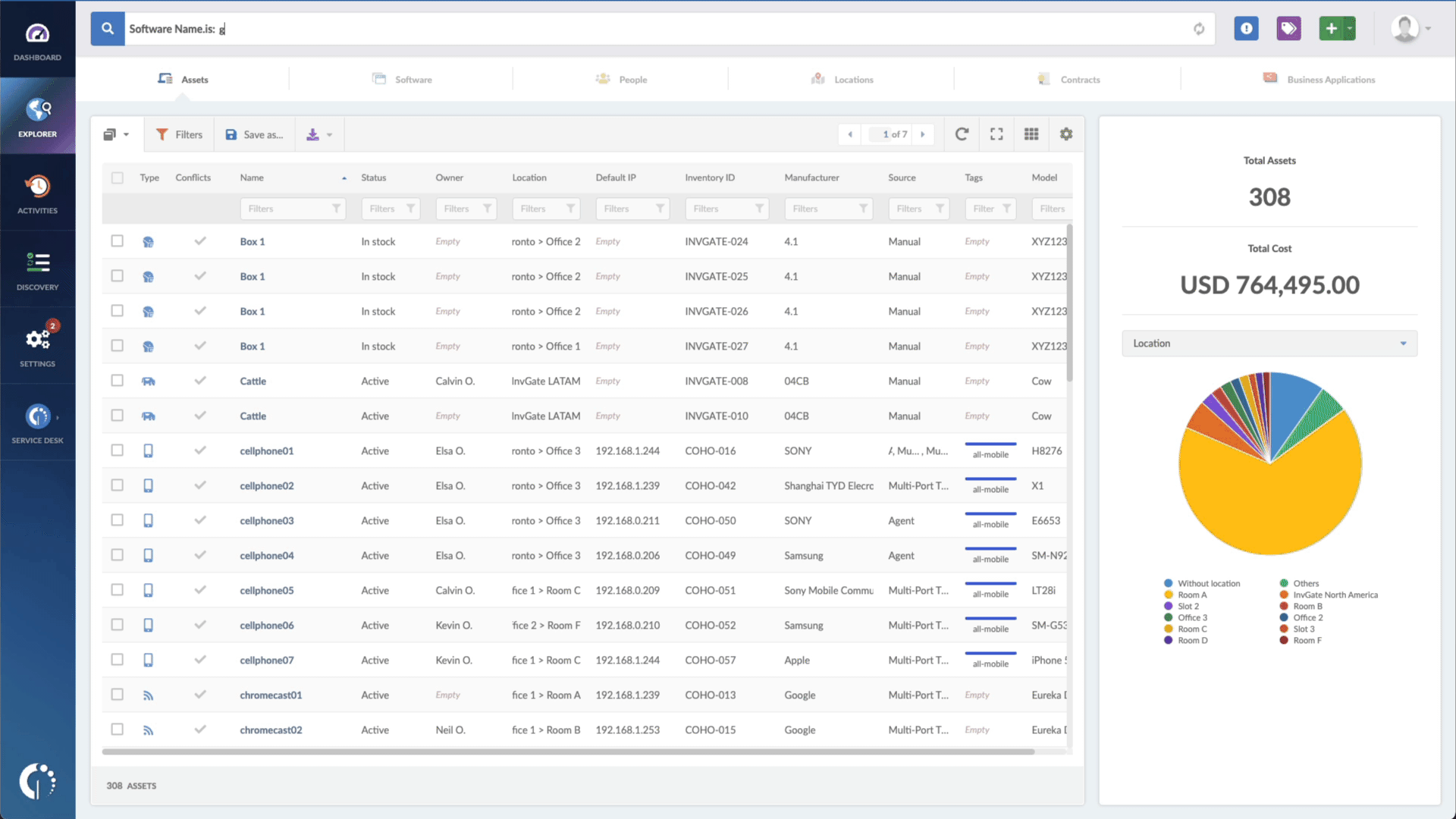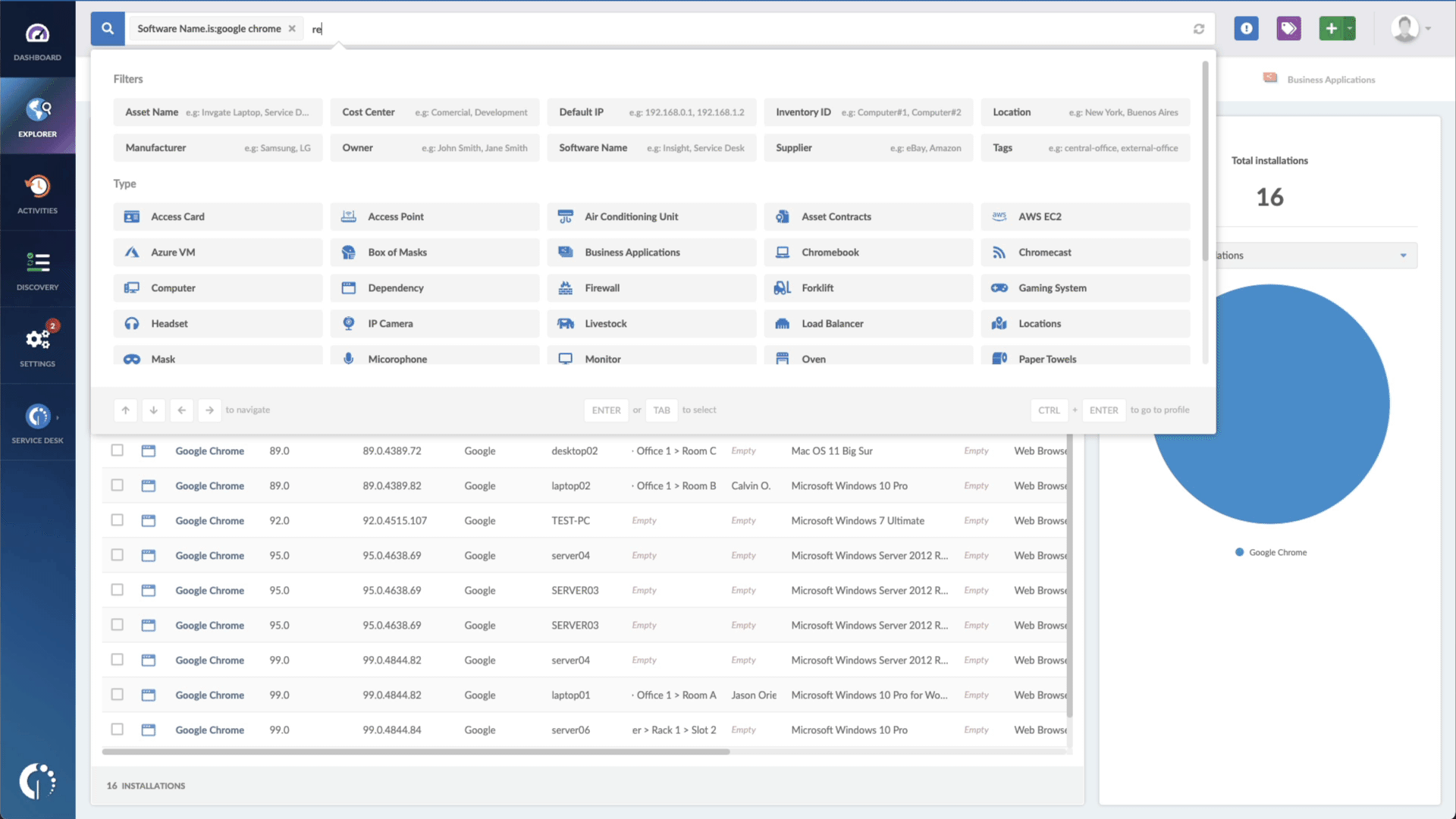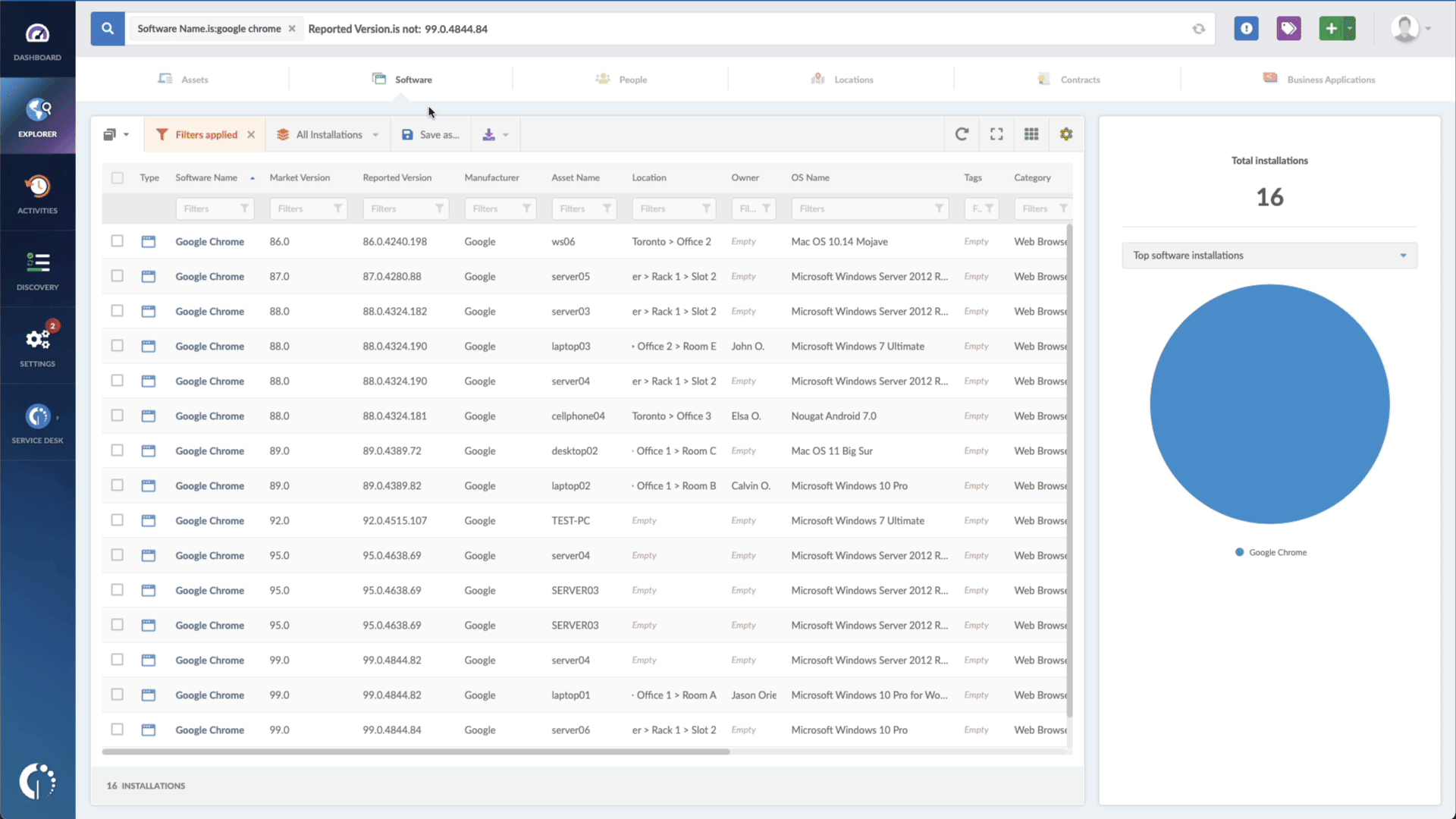
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (for Microsoft Exchange Server 2016, CU23. For Microsoft Exchange Server 2019, CU12).
The bottom line
The CVE-2021-42321 vulnerability is a remote code execution (RCE) flaw in Microsoft Exchange Server. Exploiting this vulnerability allows authenticated attackers to execute code remotely and launch attacks, potentially leading to data theft, malware installation, or email service disruption.
However, Microsoft has released a patch to address this issue, and administrators should promptly apply it to safeguard their servers.
InvGate Asset Management is a powerful solution to assist in identifying devices exposed to CVE-2021-42321 and simplifies Patch Management. To experience the benefits of InvGate Asset Management, request a 30-day free trial and start searching for vulnerable devices in your network today.