A critical Windows vulnerability known as CVE-2021-36934 came to light, exposing a significant security risk for users of various Windows 10 versions. This exploit allows attackers to gain SYSTEM privileges by exploiting flaws in the handling of symbolic links.
In response to this alarming revelation, Microsoft has released an official statement addressing the issue and providing crucial information for users to safeguard their systems.
In this article, we’ll delve into the details surrounding CVE-2021-36934, offering an in-depth understanding of its implications and exploring how InvGate Asset Management streamlines the Patch Management process.
Continue reading to safeguard your network and prevent critical vulnerabilities.
About CVE-2021-36934
CVE-2021-36934 is a critical vulnerability that affects various Windows 10 versions. It allows an attacker to gain SYSTEM privileges on the target system by exploiting a flaw in the way that Windows handles symbolic links. The vulnerability has a CVSS score of 10.0, which is the highest possible score.
The vulnerability has been exploited in the wild. In July 2021, a group of threat actors known as Hafnium exploited the vulnerability to target organizations in the United States and Europe. The attackers were able to gain SYSTEM privileges on the target systems and install malware.
How does CVE-2021-36934 work?
CVE-2021-36934 arises from inadequate validation of symbolic links during their creation process. This flaw enables an attacker to generate a symbolic link that directs to a system file that can be modified by the user account executing the application responsible for creating the symbolic link. By exploiting this vulnerability, the attacker can manipulate the symbolic link to force the application to access the system file with incorrect permissions. Consequently, the attacker gains the ability to inject arbitrary data into the system file, ultimately leading to the acquisition of SYSTEM privileges.
What are CVE-2021-36934 risks?
An attacker who exploits this vulnerability can gain SYSTEM privileges on the target system, causing significant damage. This allows the attacker to do anything that a user with SYSTEM privileges can do, including:
- Read or write any file on the system.
- Install or uninstall software.
- Modify system settings.
- Access network resources.
- Execute arbitrary code.
- Steal data.
- Install malware.
- Disrupt operations.
Is CVE-2021-36934 fixed?
Yes, Microsoft has released patches for the vulnerability. Users should install them as soon as possible to protect themselves from this vulnerability.
How to find devices exposed to CVE-2021-36934
In this section, please provide an explanation on what InvGate Asset Management can do, and a step by step to create a report with the exposed devices.
To use InvGate Asset Management to find devices that are exposed to the [number] vulnerability, follow these steps:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is: Microsoft Windows” to filter all Windows devices.
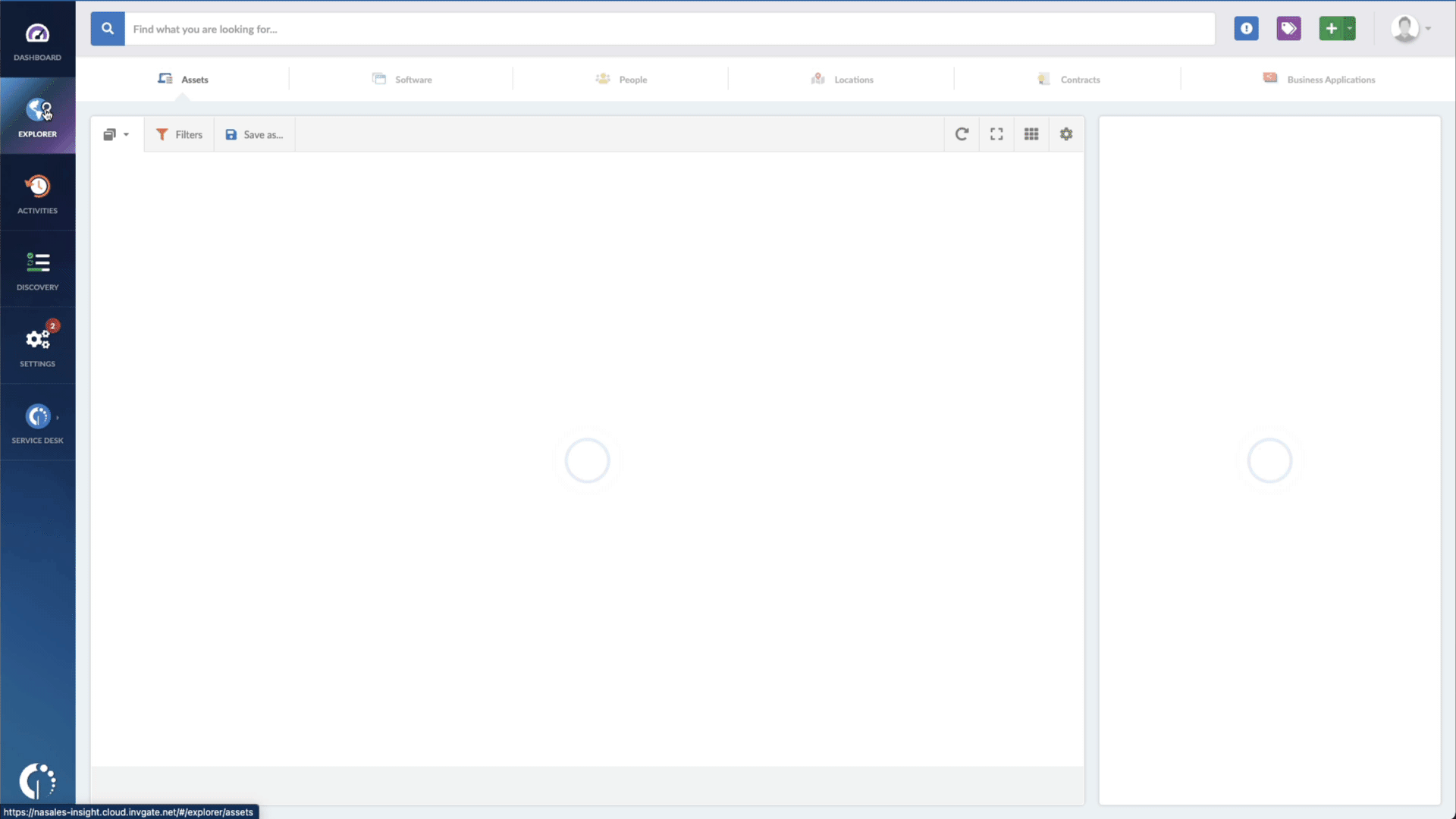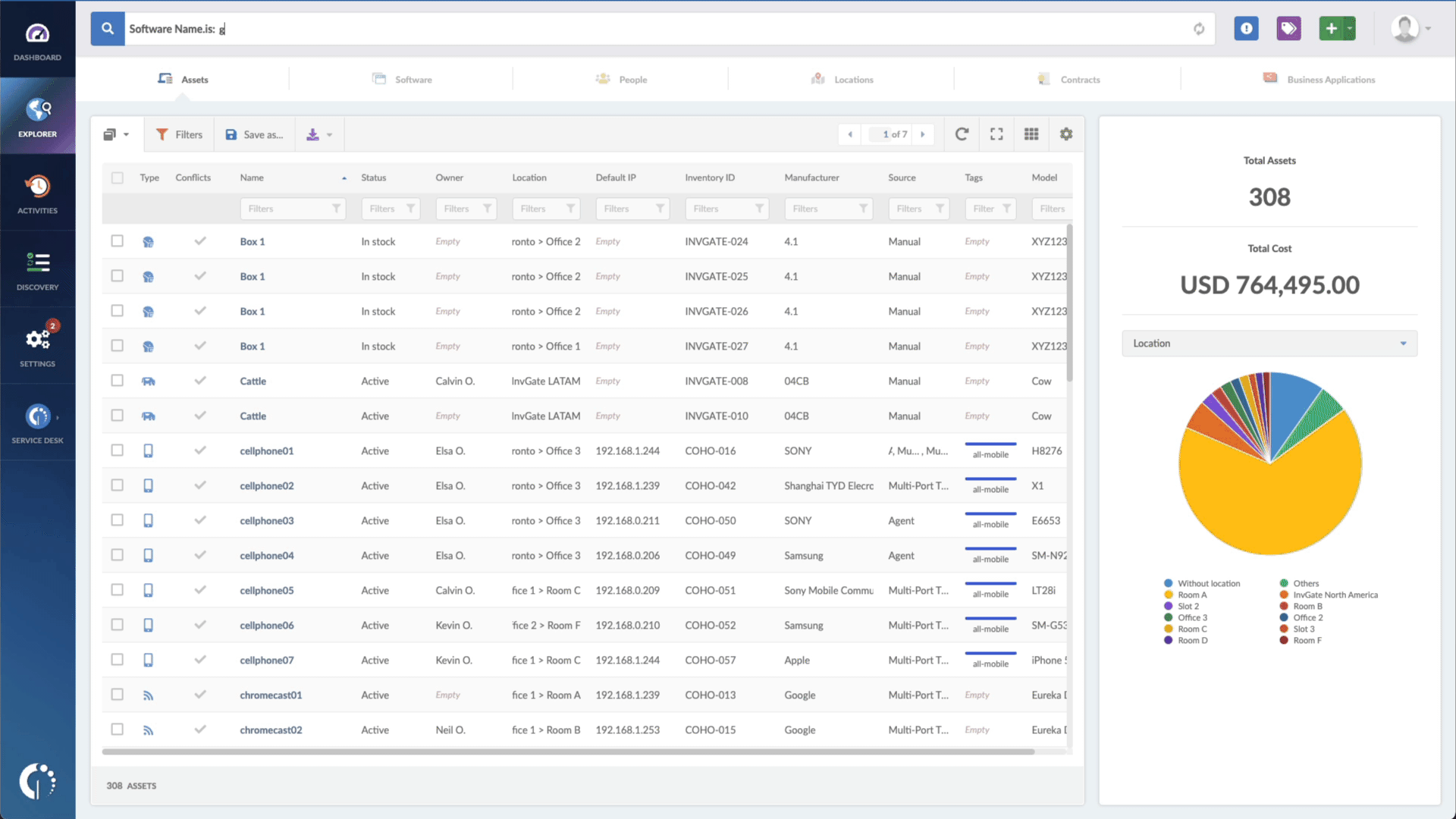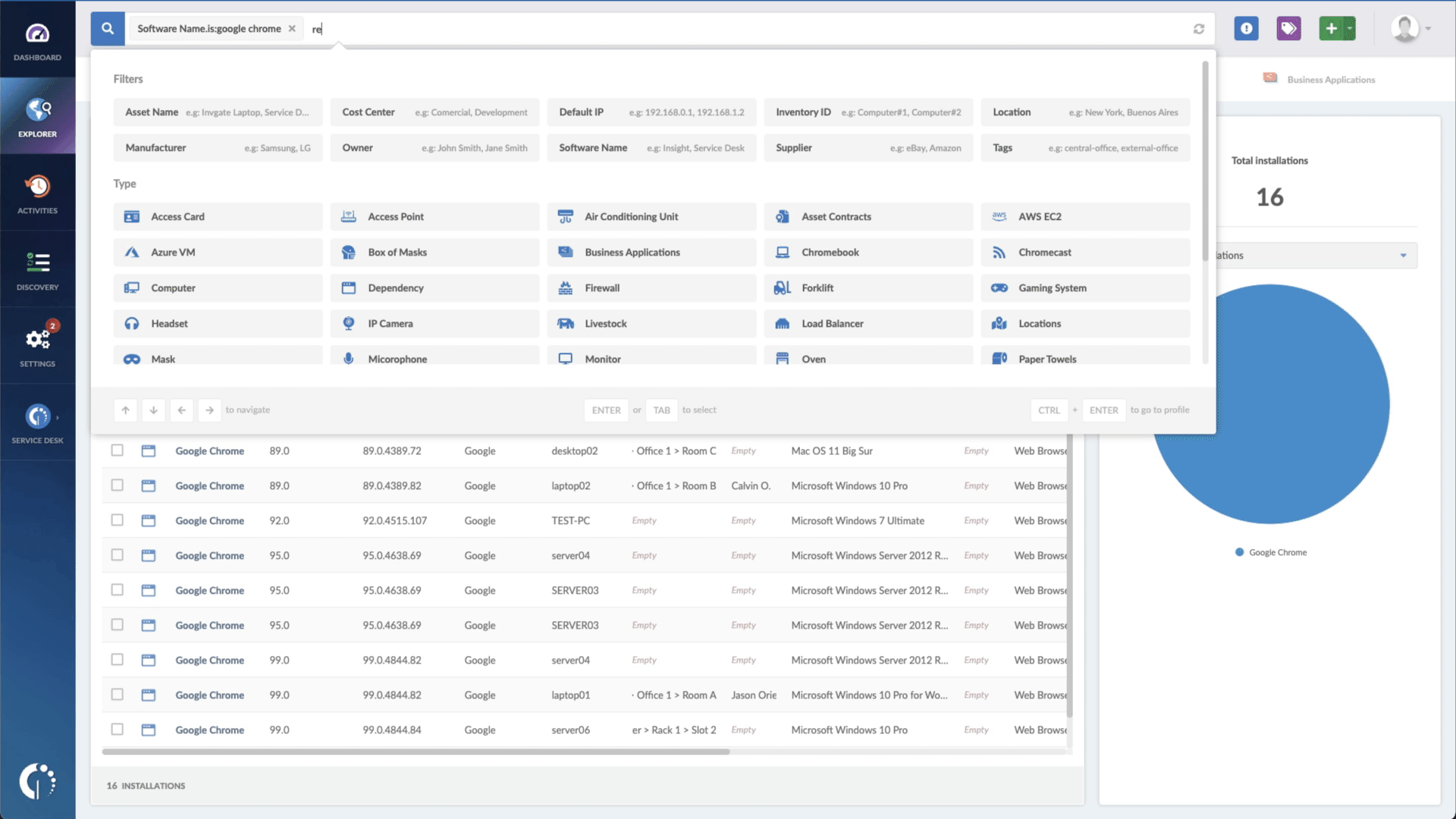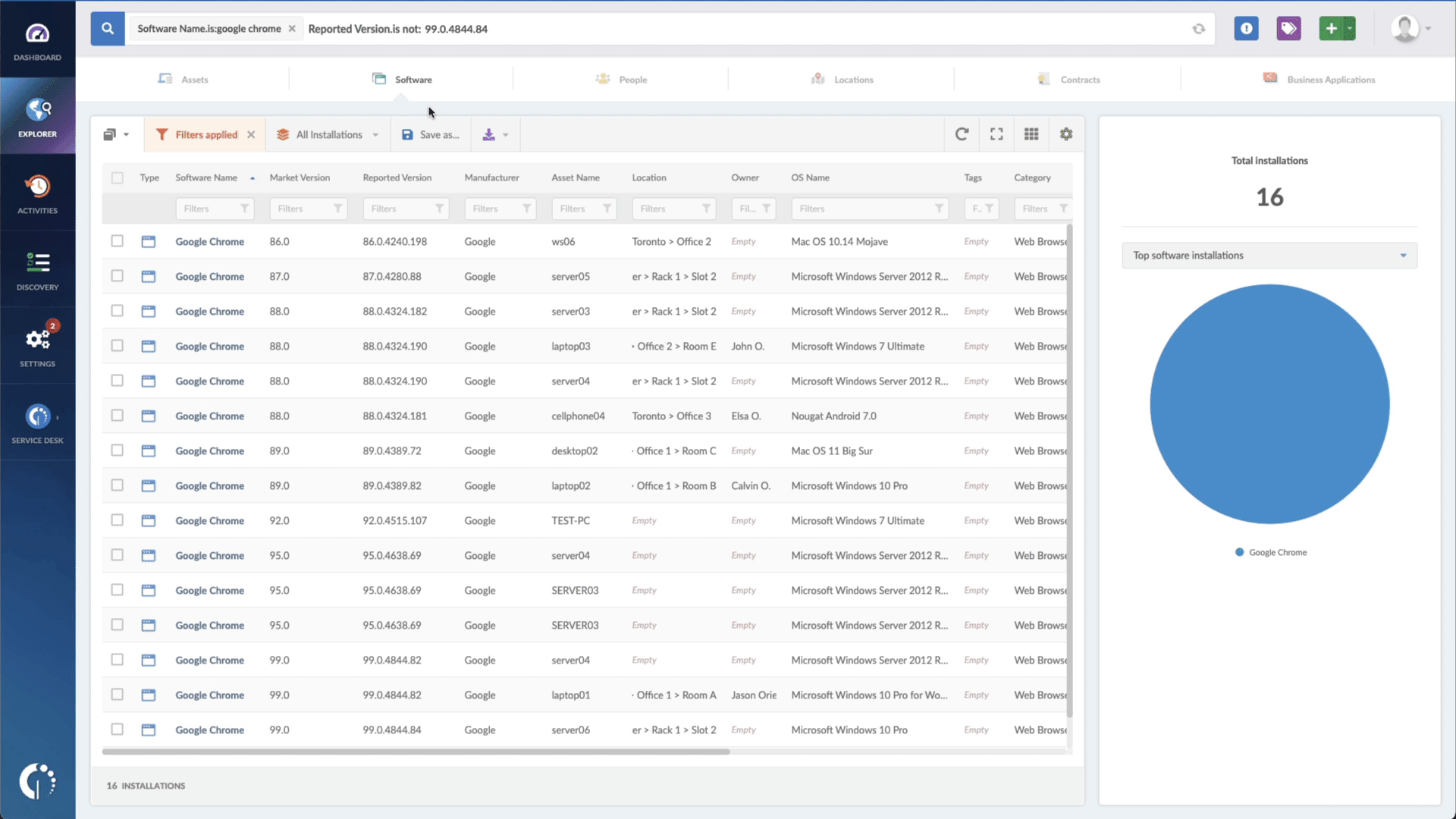
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your product, you’ll find the security update number on Microsoft’s webpage. For example, for Windows 10 Version 20H2 for 32-bit Systems, it's KB5005033).
The bottom line
CVE-2021-36934 poses a critical risk to Windows 10 users, allowing attackers to gain SYSTEM privileges and execute various malicious actions. It is crucial to promptly update systems with the provided patches.
InvGate Asset Management streamlines the Patch Management process by identifying exposed devices, enabling organizations to take immediate action. Request your 30-day free trial today and proactively safeguard your network against this vulnerability.