On January 2021, a critical vulnerability known as CVE-2021-35247 was reported, impacting the Serv-U File Server's web login screen.
In this article, we’ll delve into the specifics of CVE-2021-35247, its risks, and how InvGate Asset Management can help you identify and manage devices exposed to it.
Read on to gain a deeper understanding of this vulnerability and stay one step ahead of potential exploits.
About CVE-2021-35247
CVE-2021-35247 is an input validation vulnerability in the Serv-U File Server’s web login screen. The vulnerability is caused by a failure to properly sanitize user input before it is used to construct LDAP queries. It affects Serv-U versions 15.2.5 and earlier.
How does CVE-2021-35247 work?
An attacker can create a specially crafted URL that, when visited, will cause the Serv-U web login screen to execute arbitrary code. The attacker can then use this code to gain access to the affected system.
What are CVE-2021-35247 risks?
An attacker who successfully exploits this vulnerability can gain complete control of the affected system, allowing them to steal data, install malware, or disrupt operations.
Is CVE-2021-35247 fixed?
Yes, SolarWinds released a patch for the vulnerability in Serv-U 15.3. Users are advised to update to the latest version as soon as possible to protect their systems.
Moreover, it is recommended that you:
- Use a web application firewall (WAF) to block malicious traffic.
- Implement strong security controls, such as user authentication and access control.
- Monitor your systems for signs of compromise.
How to find devices exposed to CVE-2021-35247
With InvGate Asset Management, you can promptly detect devices that have been impacted by the CVE-2021-35247 vulnerability. The following instructions outline the process to be followed:
- Open InvGate Asset Management and go to the Explorer tab.
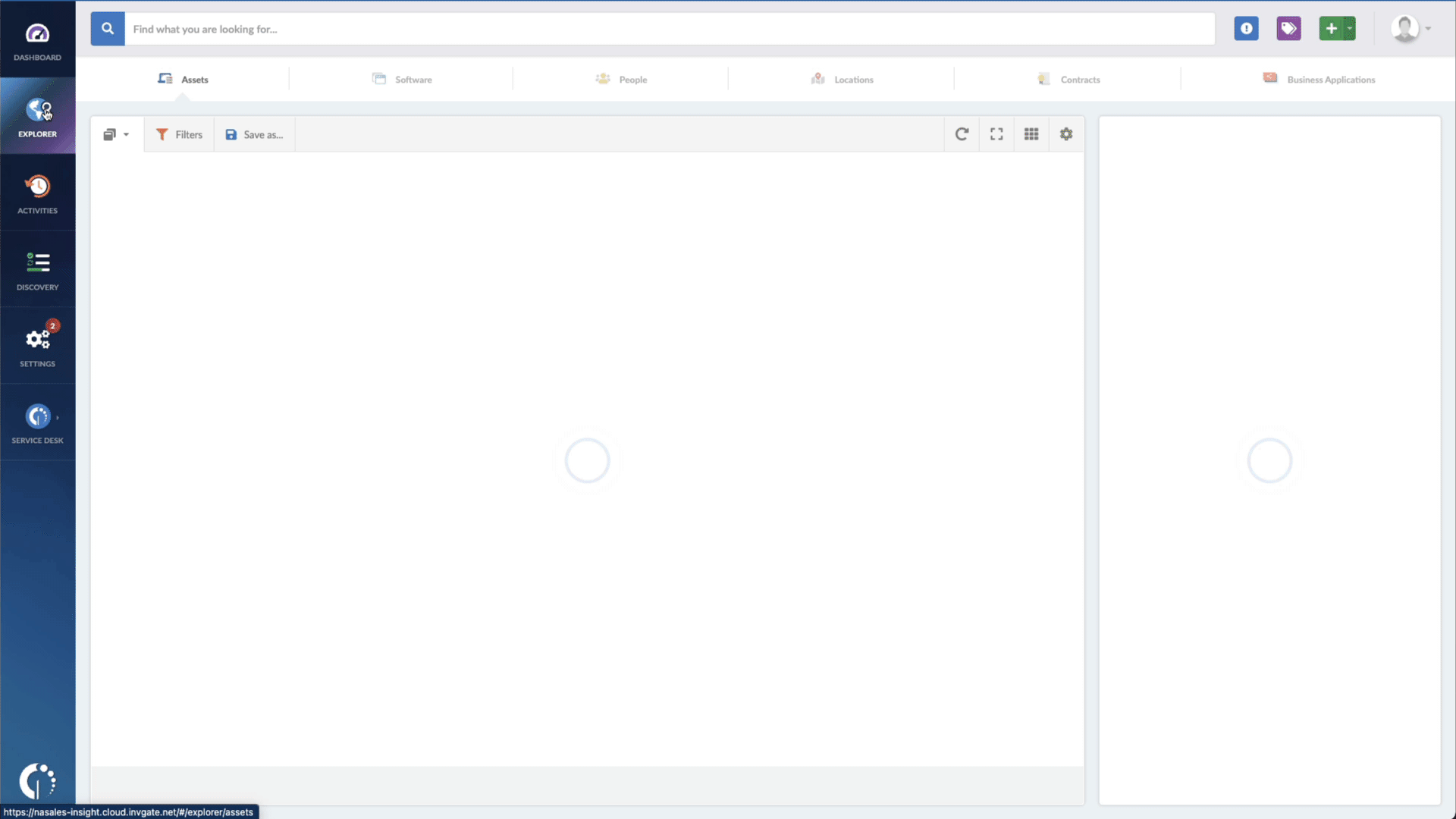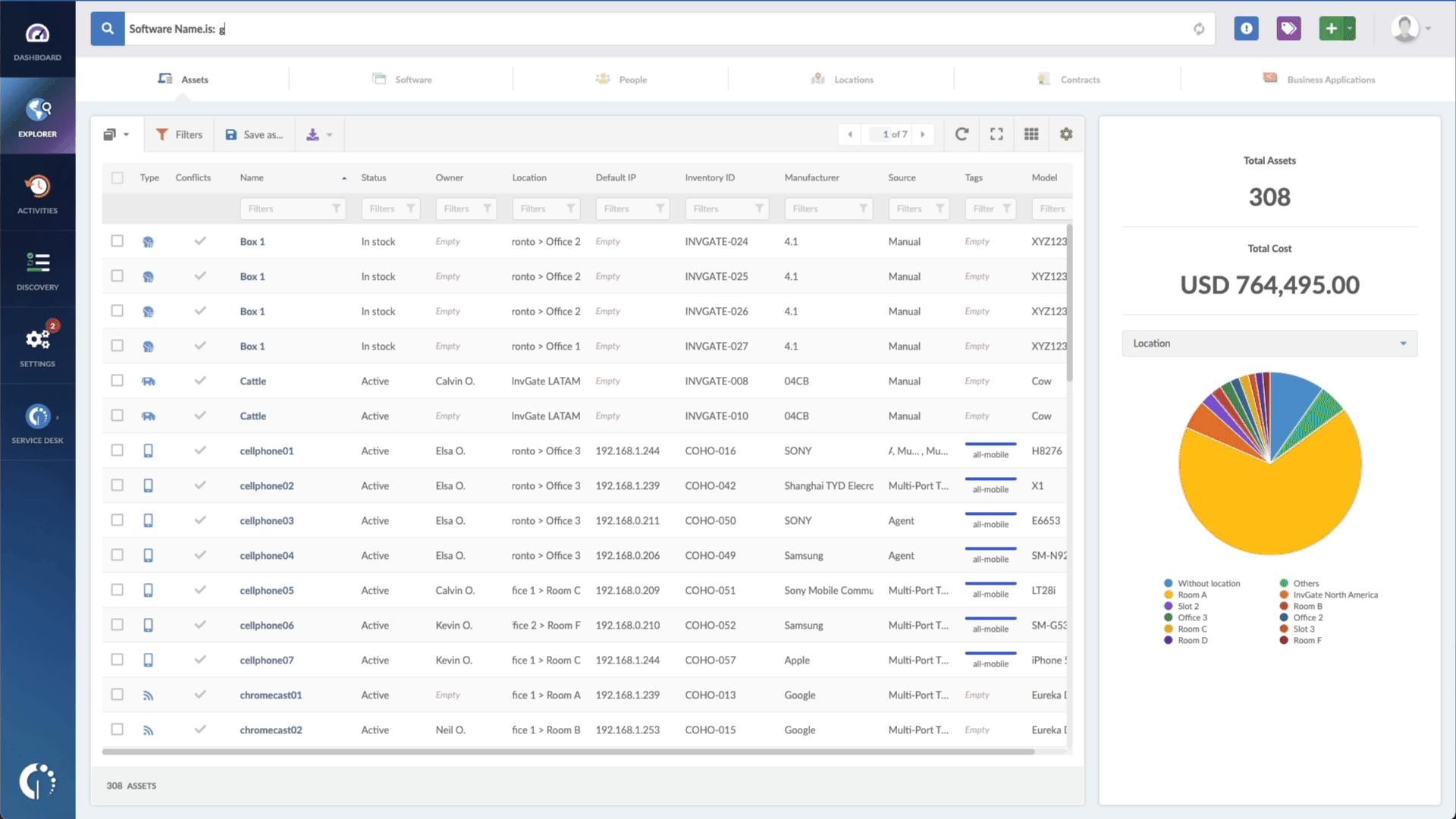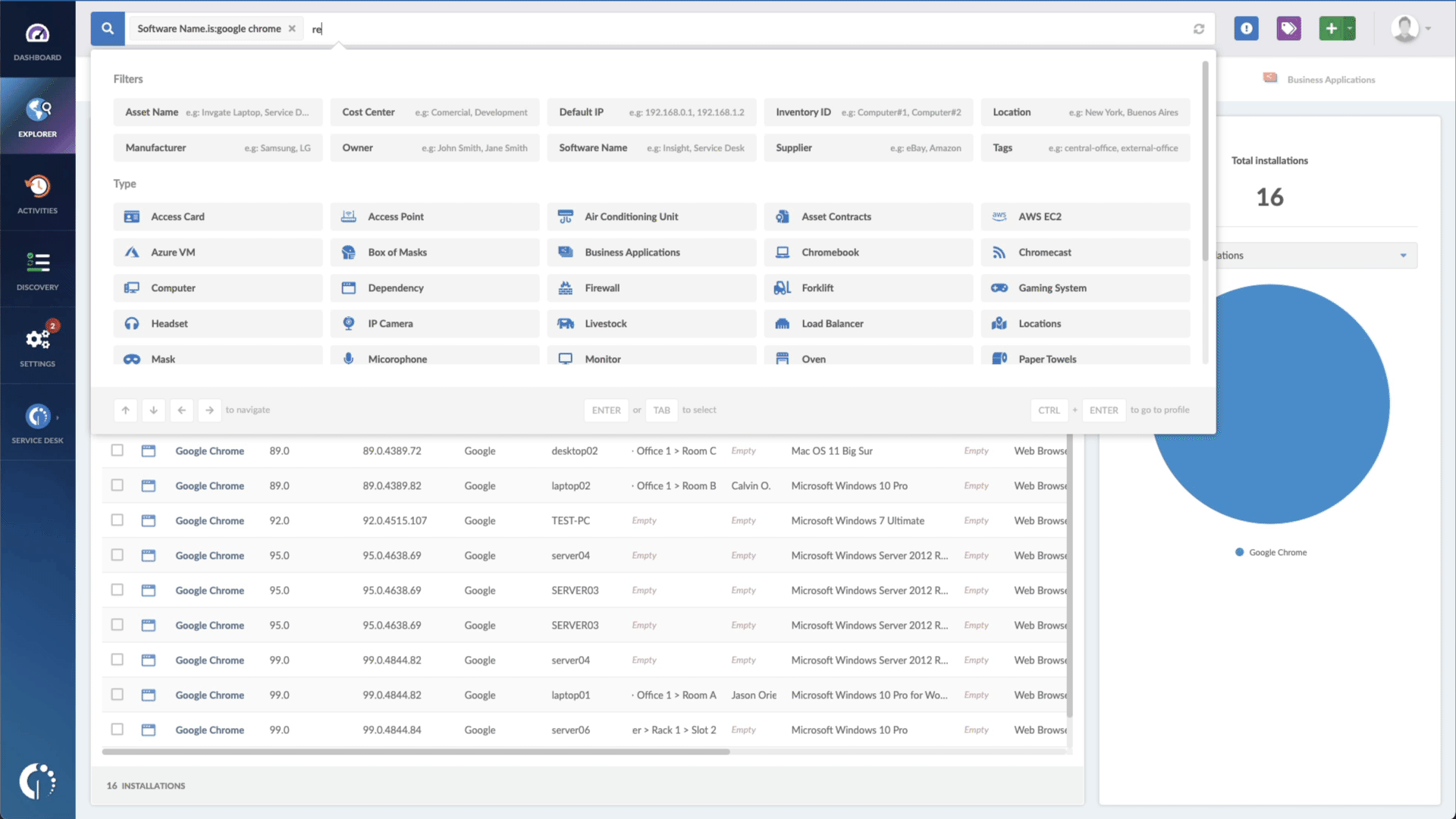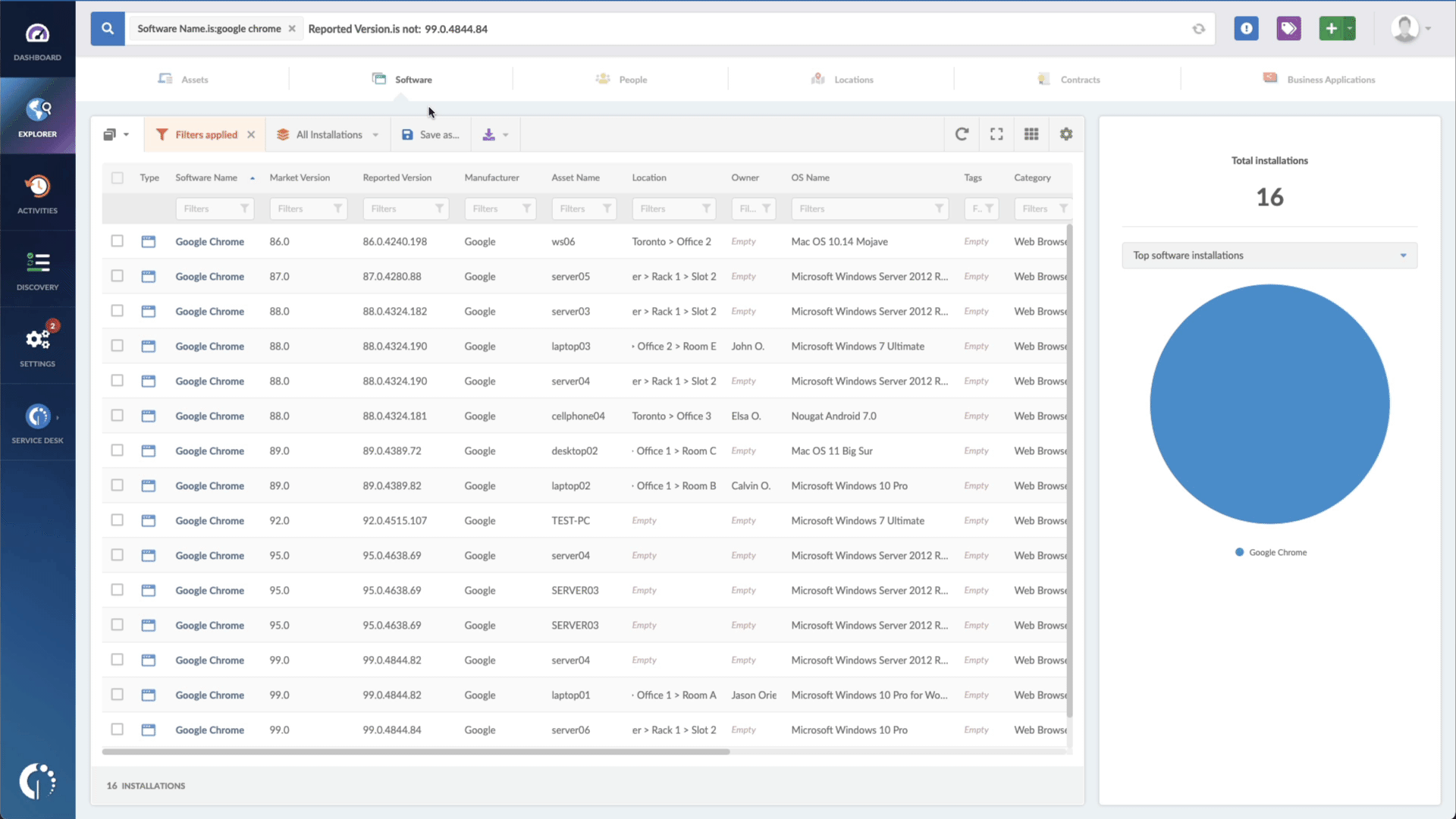
- Type in the Search bar “Software name, is:Serv-U” to filter all devices with this software.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Solarwinds’ patched version (15.3).
The bottom line
The CVE-2021-35247 vulnerability is an input validation flaw in Serv-U File Server's web login screen, impacting versions 15.2.5 and earlier.
Fortunately, SolarWinds released a patch in version 15.3 to address the vulnerability, and users are strongly advised to update promptly.
To identify devices exposed to CVE-2021-35247, InvGate Asset Management offers a powerful solution. This capability, combined with additional security measures like implementing strong controls and monitoring systems for compromise, helps safeguard against potential exploits.
Request a 30-day free trial to streamline your Patch Management process and ensure the security of your network.
















