Informed on April 2021, CVE-2021-22205 is a critical vulnerability that has sent shockwaves through the GitLab community. GitLab issued an official statement highlighting the severity of this security flaw and urging users to take immediate action.
In this article, we’ll provide a comprehensive overview of CVE-2021-22205, its risks, and how InvGate Asset Management simplifies Patch Management.
Ready to dive deeper into CVE-2021-22205 and protect your infrastructure? Continue reading to learn more about this security flaw's risks and mitigation strategies.
About CVE-2021-22205
CVE-2021-22205 is a critical severity vulnerability that affects all versions of GitLab. It is caused by a failure in GitLab's image processing pipeline to properly validate image files before passing them to a third-party file parser called ExifTool. This failure can allow an attacker to upload a specially crafted image file that can execute arbitrary commands on the GitLab server.
It affects the following versions:
- 11.9.x - 13.8.7
- 13.9.0 - 13.9.5
- 13.10.0 - 13.10.2
How does CVE-2021-22205 work?
An attacker can create a specially crafted image file that contains malicious code and upload it to a GitLab repository affected by the vulnerability. When the file is processed by GitLab, the malicious code is executed on the server. This code could be used to steal sensitive data, install malware, or take control of the server.
What are CVE-2021-22205 risks?
An attacker who is able to exploit this vulnerability could gain full control of a GitLab server, allowing them to:
- Steal data, such as passwords, credit card numbers, or intellectual property.
- Install malware that could be used to gain access to other systems on the network.
- Disrupt service, leading to lost productivity, revenue, and reputational damage.
Is CVE-2021-22205 fixed?
Yes, this issue was remediated and patched in the GitLab 13.10.3, 13.9.6, and 13.8.8 release from April 14, 2021. Users should update it as soon as possible.
How to find devices exposed to CVE-2021-22205
With InvGate Asset Management, you can quickly detect devices that are impacted by the CVE-2021-22205 vulnerability. The following instructions outline the necessary steps to follow;
- Open InvGate Asset Management and go to the Explorer tab.
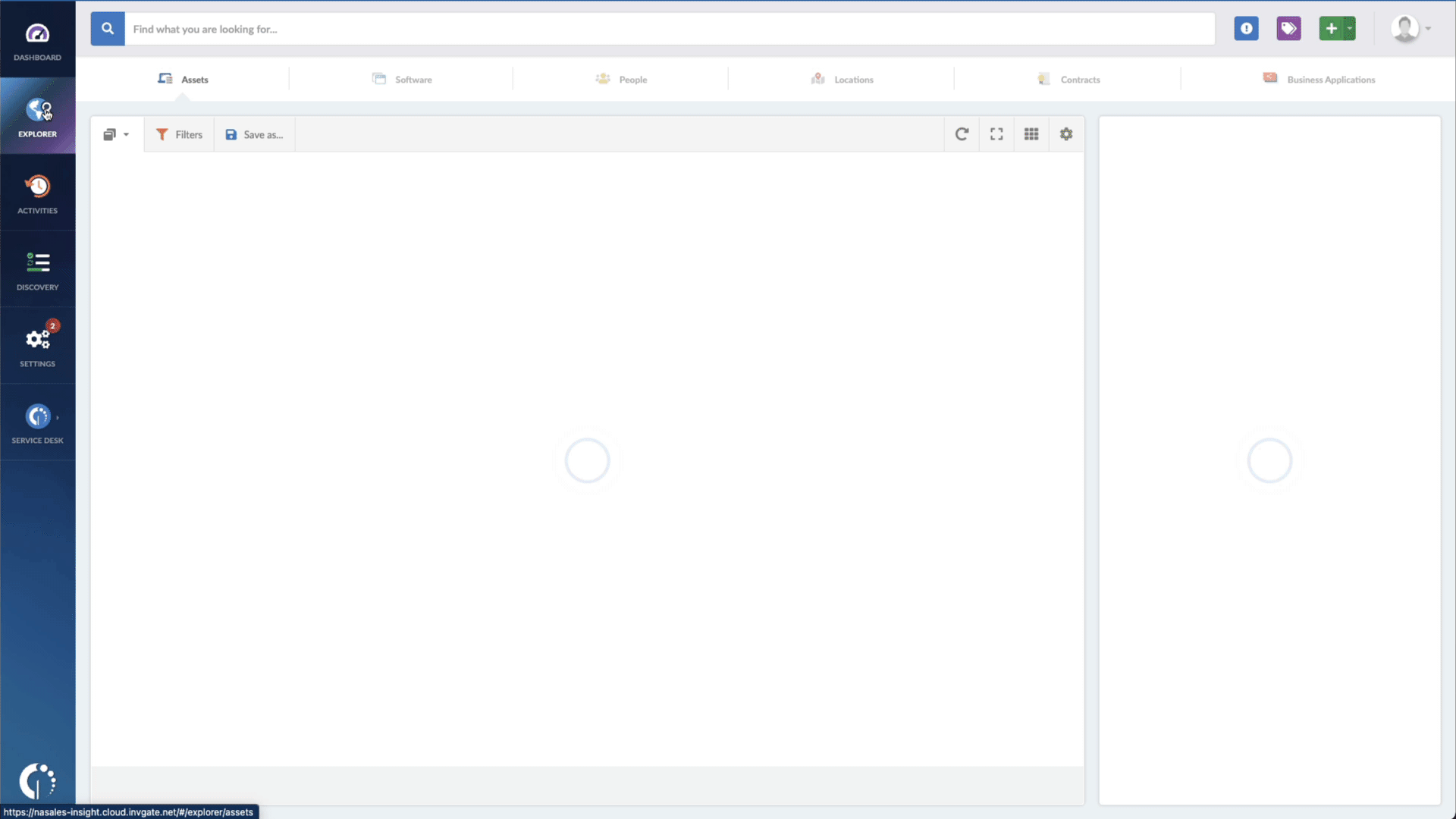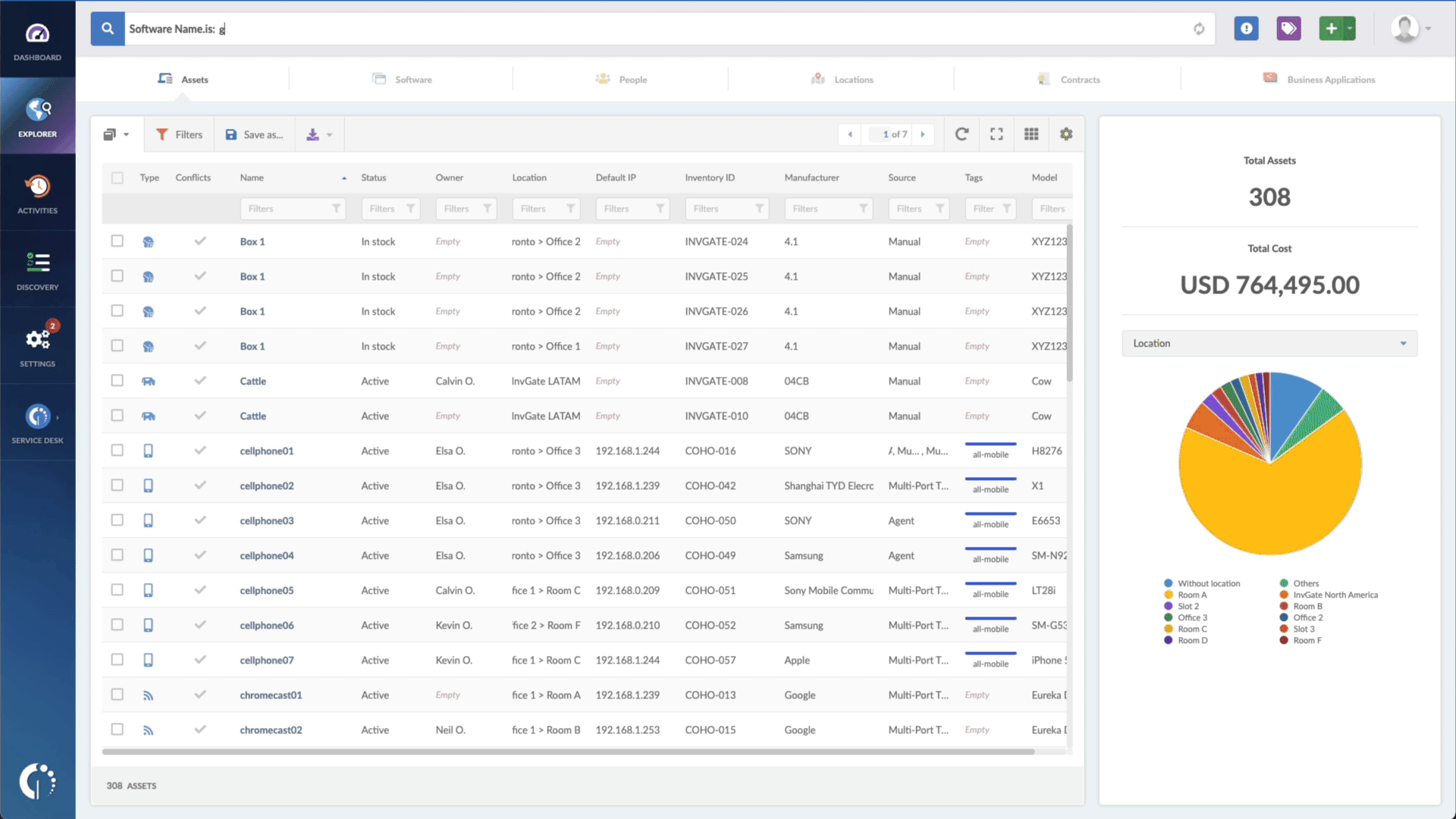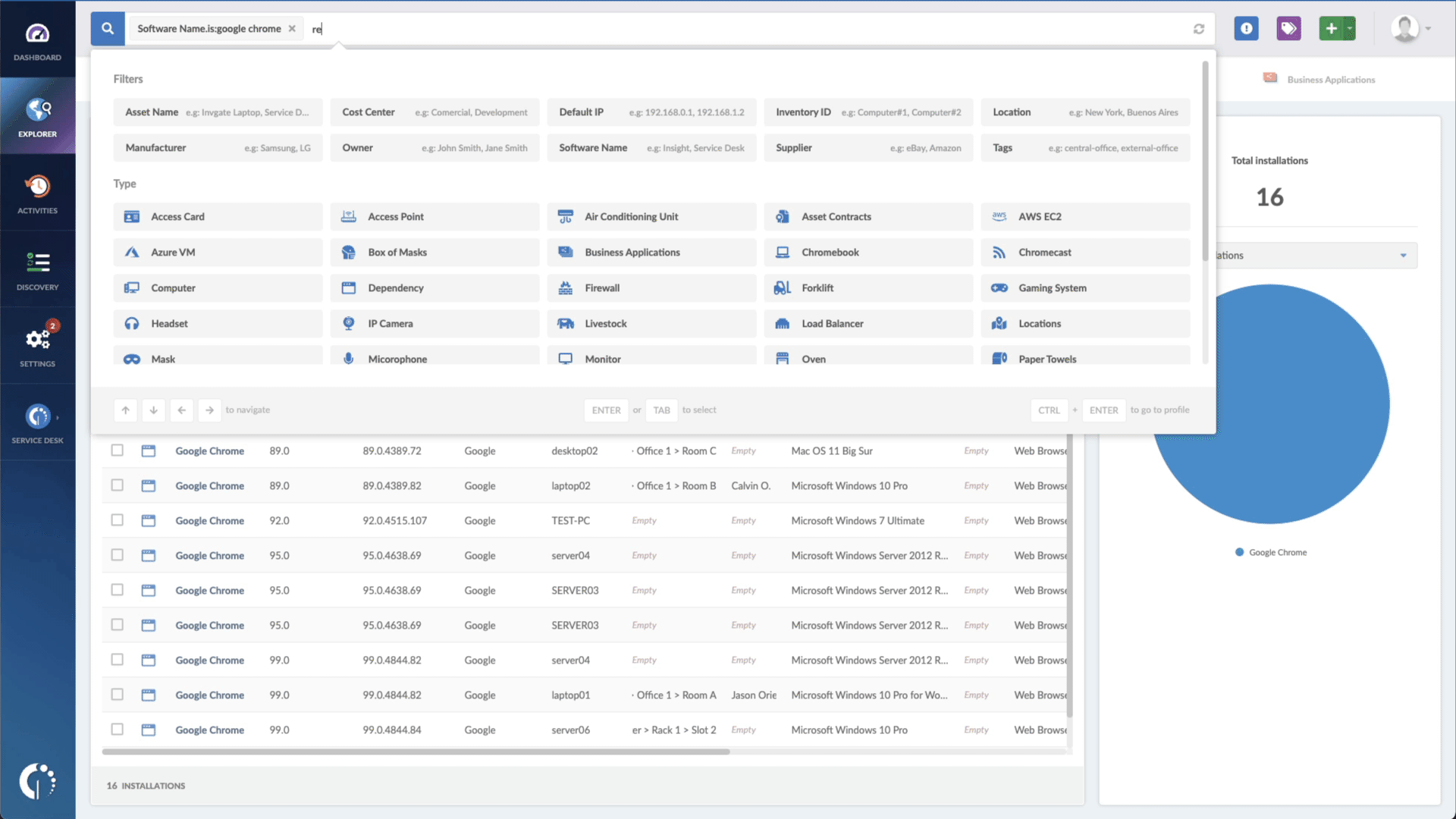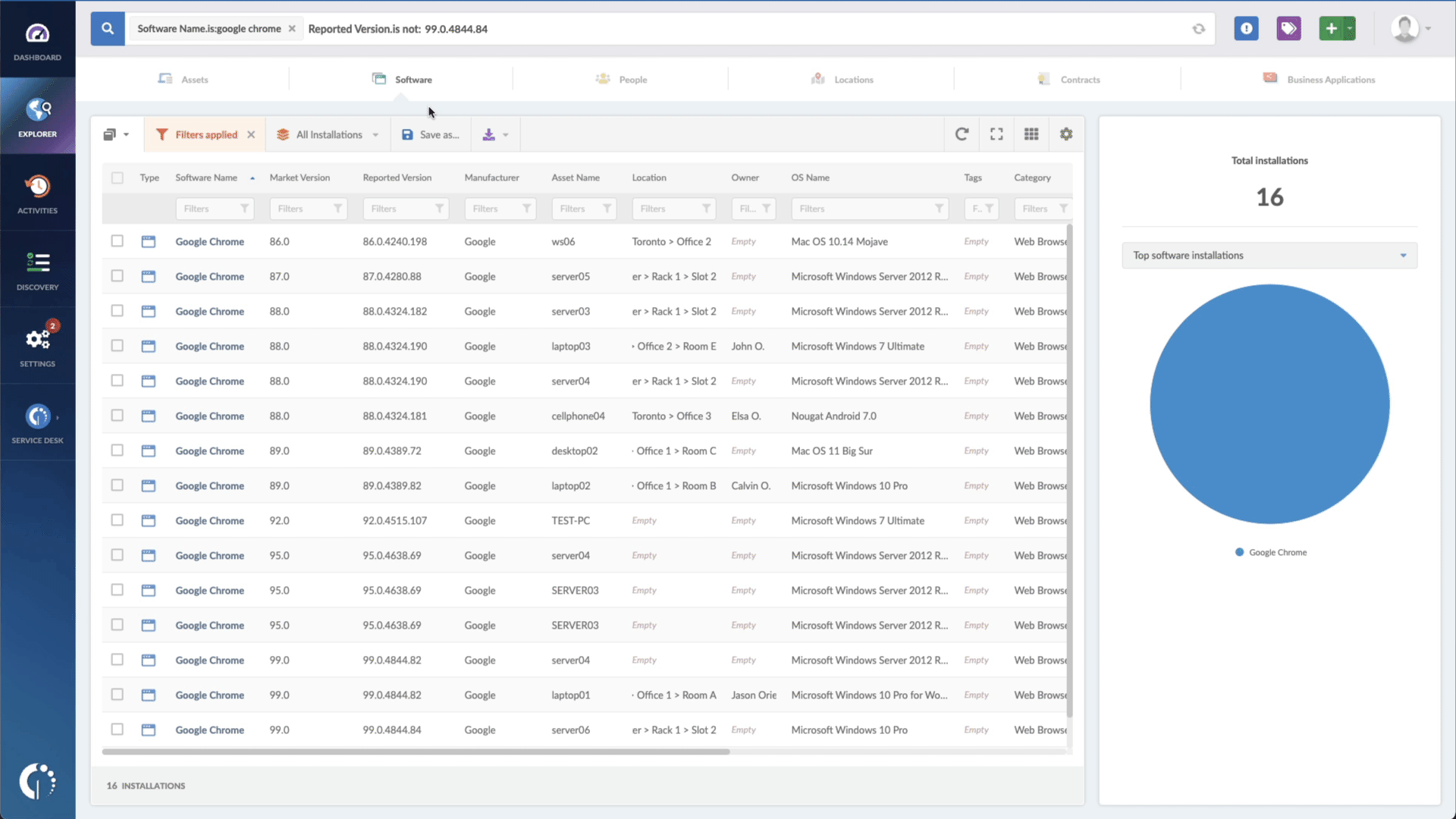
- Type in the Search bar “Software name, is:GitLab” to filter all devices with this software.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste the patched version (13.10.3, 13.9.6, and 13.8.8).
The bottom line
CVE-2021-22205 is a critical vulnerability affecting all versions of GitLab. If left unpatched, it poses significant risks, such as data theft, malware installation, and service disruption.
To address this issue, GitLab released patches, and users must update their software. To simplify Patch Management, InvGate Asset Management offers a solution for identifying devices exposed to CVE-2021-22205 efficiently. Request a 30-day free trial today and protect against potential security threats.
















