Discovering and promptly addressing vulnerabilities in network security, like the CVE-2020-3580, is crucial for organizations to safeguard their sensitive data and protect against potential breaches.
In this blog post, we’ll delve into the details of the critical vulnerability in Cisco ASA and FTD software, how it works, its risks, and the capabilities of InvGate Asset Management in simplifying Patch Management.
Don't miss out on vital information that can help you protect your organization against CVE-2020-3580 vulnerability. Read on to learn more.
About CVE-2020-3580
CVE-2020-3580 is a cross-site scripting (XSS) vulnerability in the web services interface of Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software.
XSS vulnerabilities allow attackers to inject malicious code into a web page that is then executed by the victim's browser, potentially leading to stealing cookies, session tokens, and other sensitive information.
How does CVE-2020-3580 work?
The CVE-2020-3580 vulnerability is caused by insufficient validation of user-supplied input by the web services interface. An attacker could exploit this vulnerability by persuading an interface user to click a crafted link. Once the link is clicked, the attacker's malicious code is executed in the victim's browser.
What are CVE-2020-3580 risks?
An attacker who successfully exploits this vulnerability could gain access to sensitive information, such as cookies, session tokens, and passwords, allowing it to take control of the victim's account or network.
Is CVE-2020-3580 fixed?
Yes, Cisco has released software updates that address CVE-2020-3580. There are no workarounds that address this vulnerability. Users are urged to apply the security updates as soon as possible.
The latest versions of the software that include the patch are as follows:
- Cisco Adaptive Security Appliance Software: 9.15.1
- Cisco Firepower Threat Defense Software: 6.6.1
How to find devices exposed to CVE-2020-3580
By utilizing InvGate Asset Management, you can promptly detect devices impacted by the CVE-2020-3580 vulnerability. To facilitate this process, these are the steps to follow:
- Open InvGate Asset Management and go to the Explorer tab.
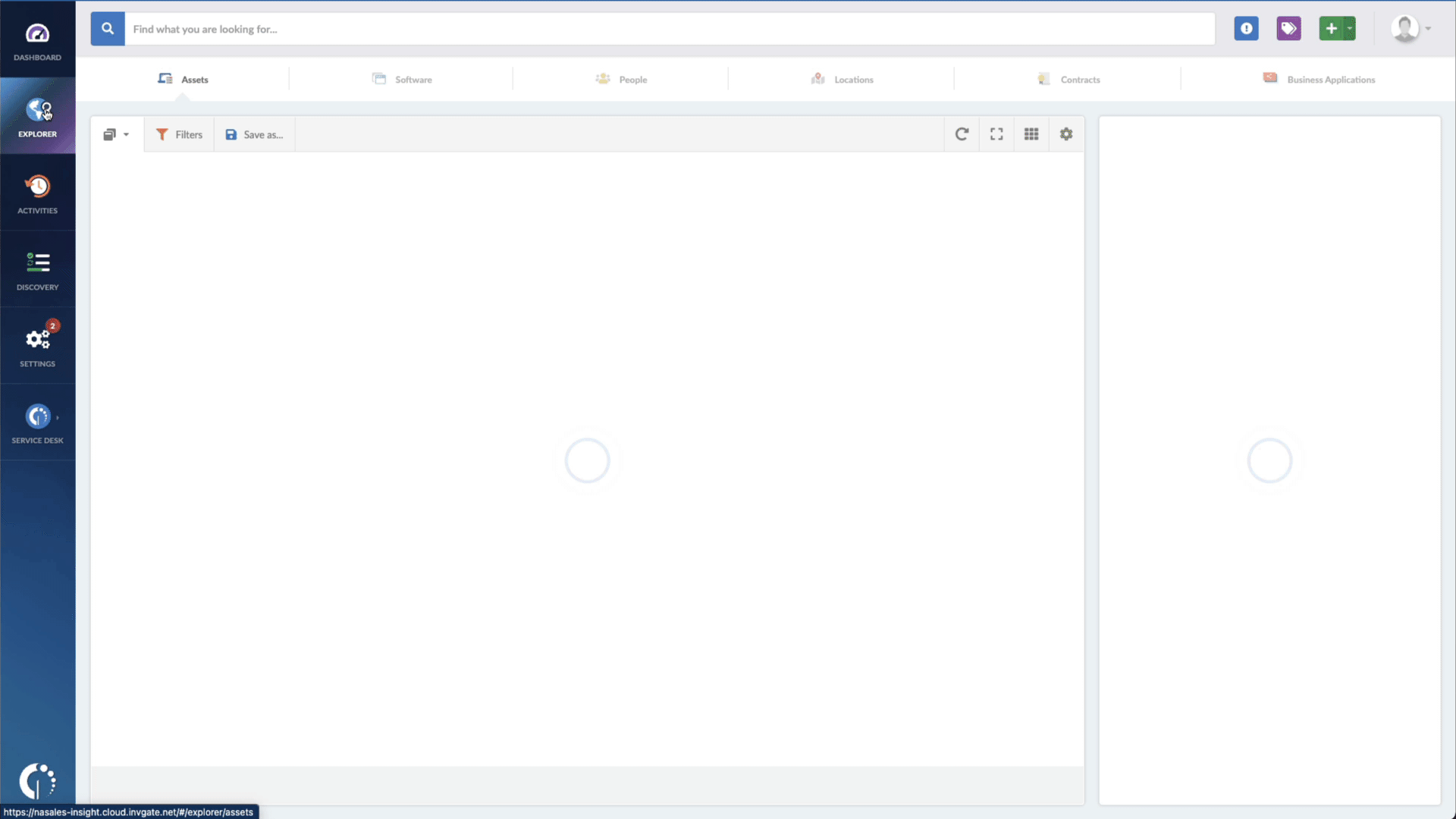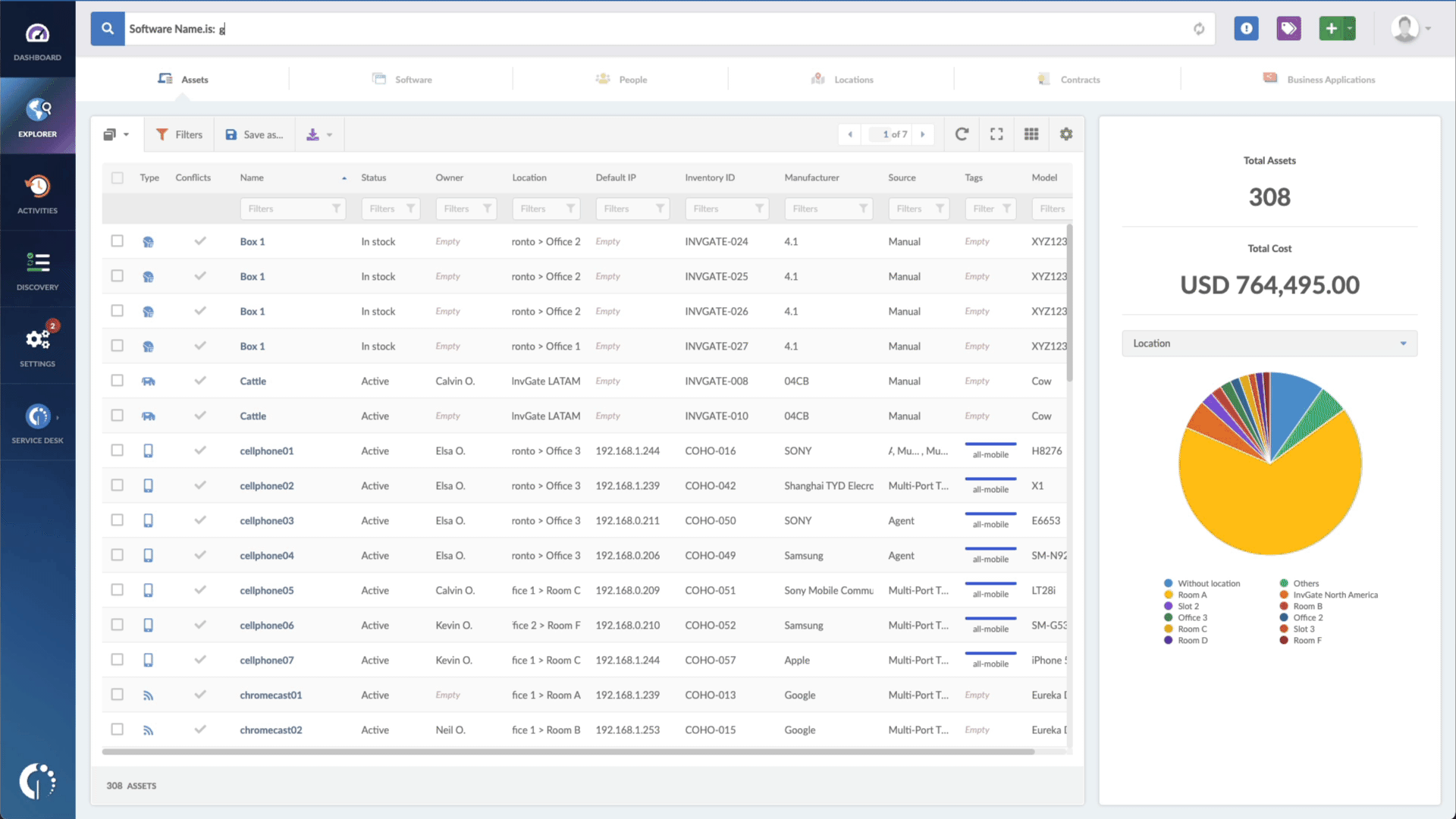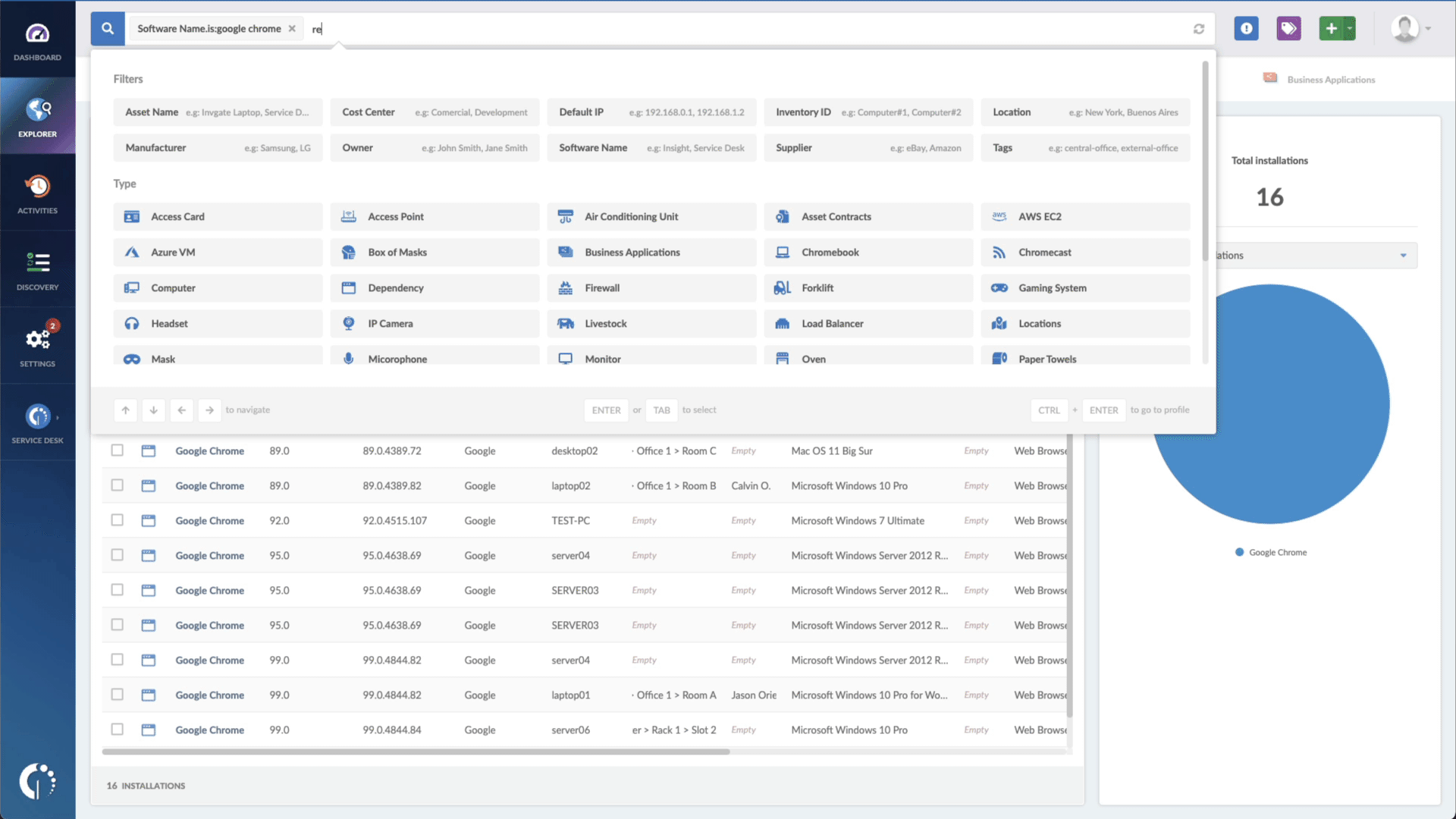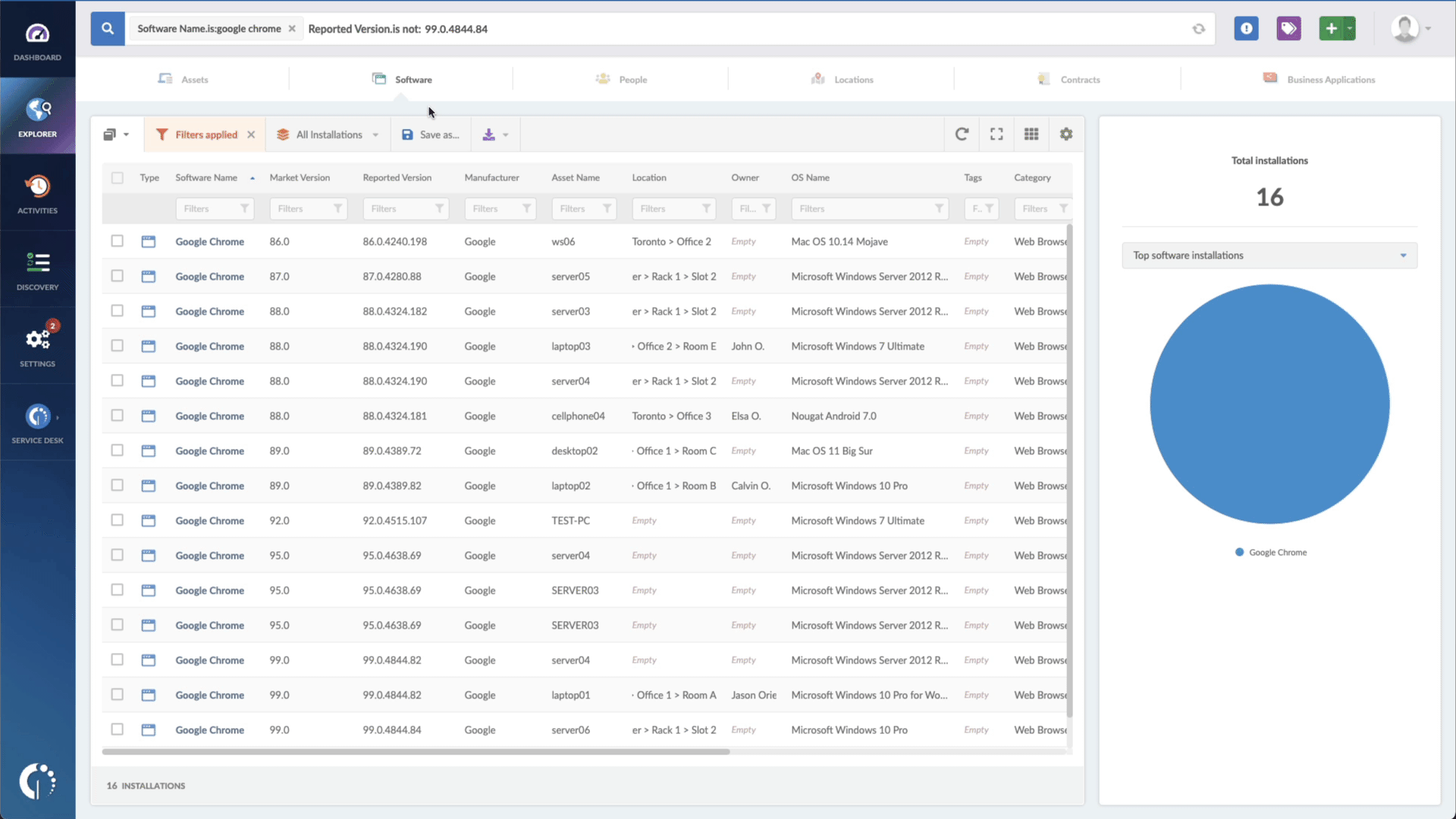
- Type in the Search bar “Software name, is:Cisco Adaptive Security Appliance” or “Software name, is:Cisco Firepower Threat Defense” to filter all devices with the software.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Cisco’s patched version (9.15.1 or 6.6.1).
The bottom line
In summary, the CVE-2020-3580 vulnerability in Cisco ASA and FTD software poses a significant security risk, potentially leading to stealing cookies, session tokens, and other sensitive information. To mitigate these risks, organizations must promptly patch their affected Cisco ASA and FTD devices.
With InvGate Asset Management, the process of identifying devices affected by the CVE-2020-3580 vulnerability becomes streamlined and efficient. By leveraging InvGate Asset Management's capabilities, organizations can swiftly detect vulnerable devices within their network.
Experience firsthand how InvGate Asset Management simplifies Patch Management and assists in securing your network infrastructure. Request a 30-day free trial today!