In the world of cybersecurity, staying informed about the latest vulnerabilities is crucial to safeguarding your systems. One vulnerability that demands attention is CVE-2020-14882, a remote code execution vulnerability in Oracle WebLogic Server.
This exploit has the potential to expose your organization to significant risks, including taking complete control of vulnerable systems.
In this article, we’ll give an overview of the CVE-2020-14882 vulnerability, its associated risks, and how InvGate Asset Management can simplify Patch Management.
Protect your systems and gain valuable insights into the CVE-2020-14882 exploit. Read on to learn more about the risks involved and the proactive steps you can take to ensure the security of your organization.
About CVE-2020-14882
CVE-2020-14882 is a remote code execution vulnerability in Oracle WebLogic Server. This vulnerability, which has been exploited in the wild, has a CVSSv3 base score of 9.8, which is considered to be critical.
The versions of the Oracle WebLogic Server affected by CVE-2020-14882 are the following:
- WebLogic Server 10.3.6.0
- WebLogic Server 12.1.3.0
- WebLogic Server 12.2.1.3
- WebLogic Server 12.2.1.4
- WebLogic Server 14.1.1.0
How does CVE-2020-14882 work?
The vulnerability is due to improper validation of user-supplied data in two classes. As a consequence, an unauthenticated attacker can achieve remote code execution on a vulnerable device by sending a crafted HTTP GET request.
What are CVE-2020-14882 risks?
An attacker who successfully exploits the vulnerability could take complete control of a vulnerable system, allowing them to steal data, install malware, or disrupt operations.
Is CVE-2020-14882 fixed?
Yes, Oracle has released patches for CVE-2020-14882. Organizations that use Oracle WebLogic Server should apply them as soon as possible to protect their systems from attack.
How to find devices exposed to CVE-2020-14882
InvGate Asset Management enables quick identification of devices that are impacted by the CVE-2020-14882 vulnerability. To do it, follow the steps outlined below:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Oracle WebLogic Server” to filter all devices with this software.
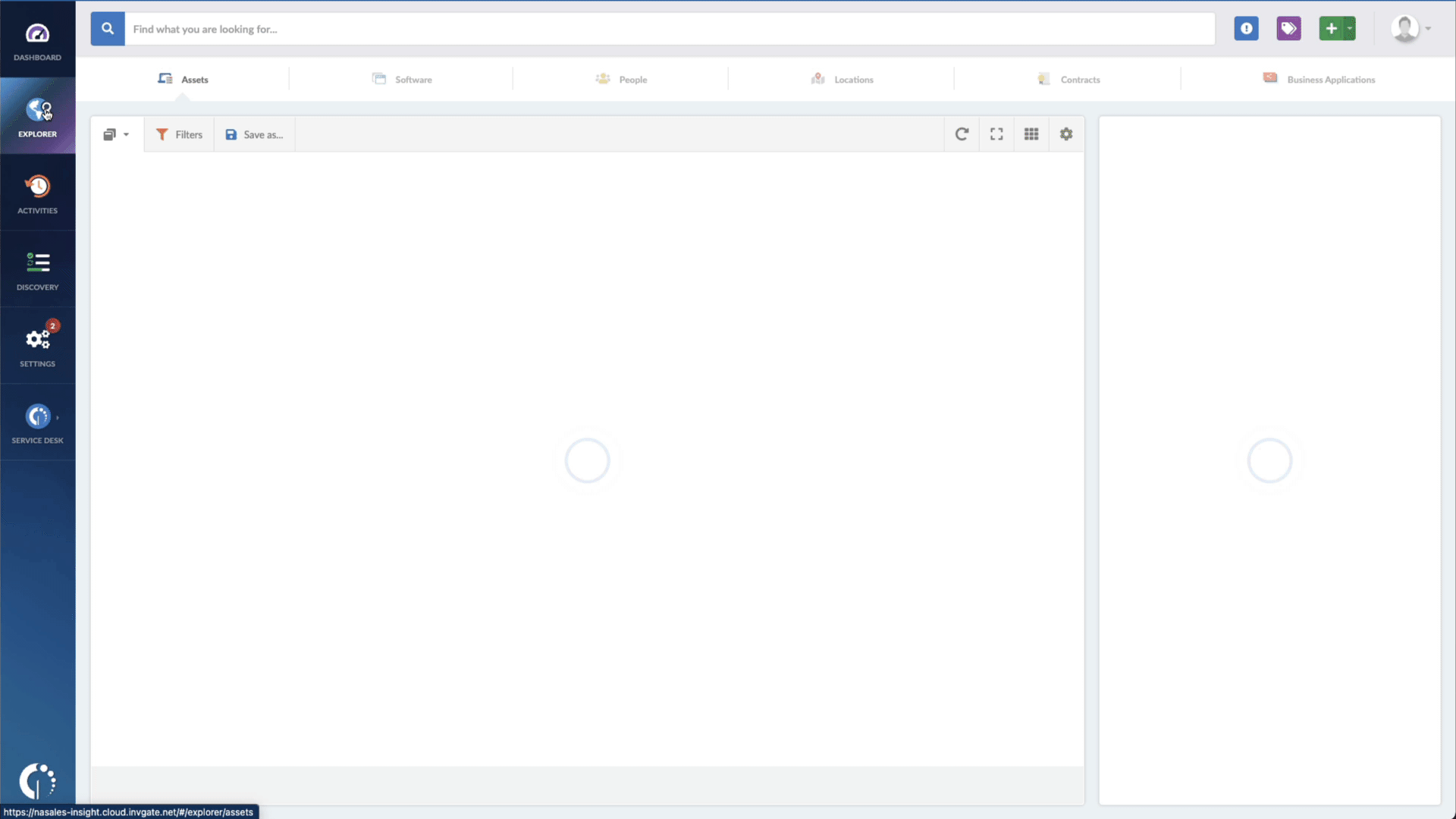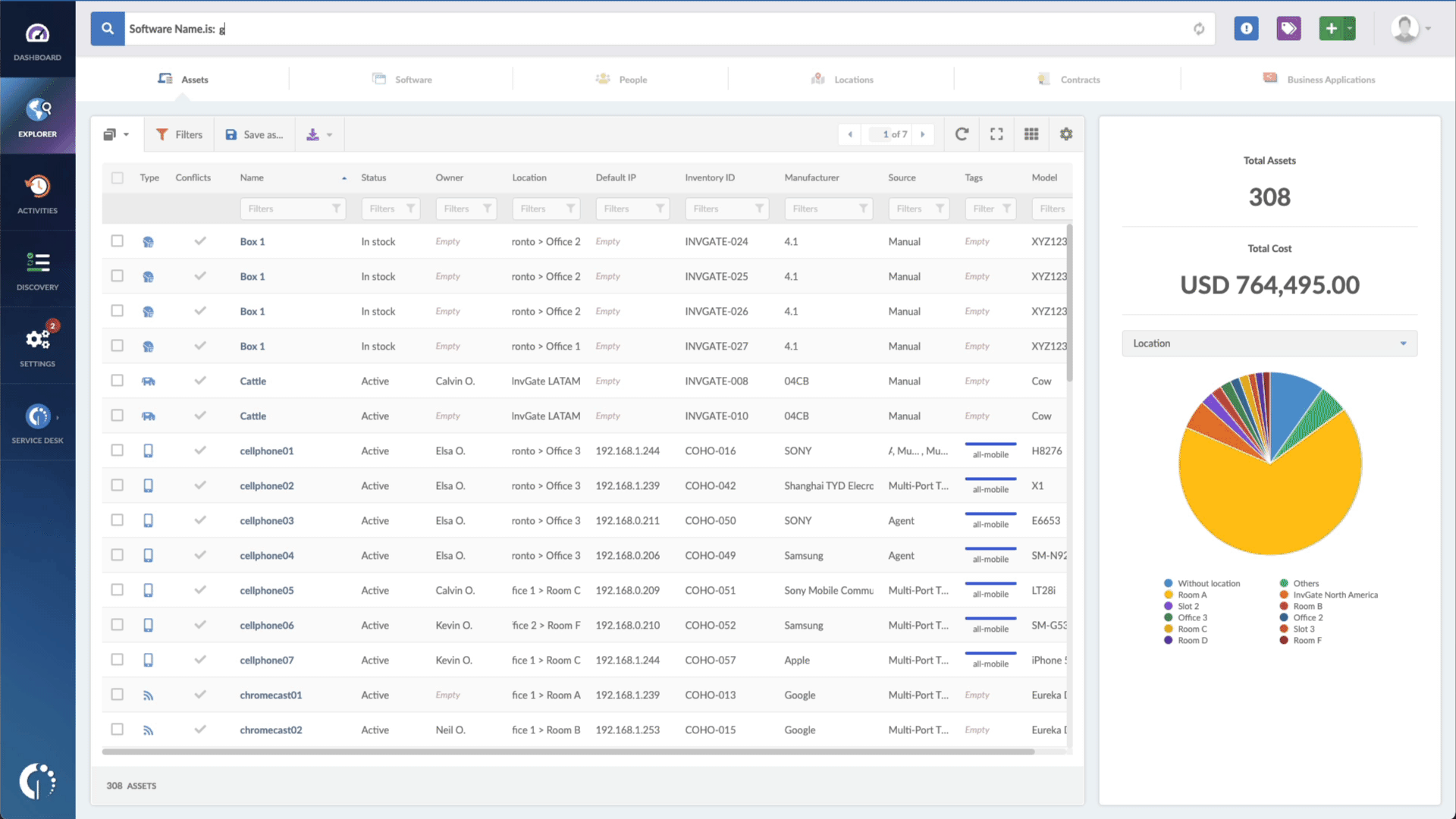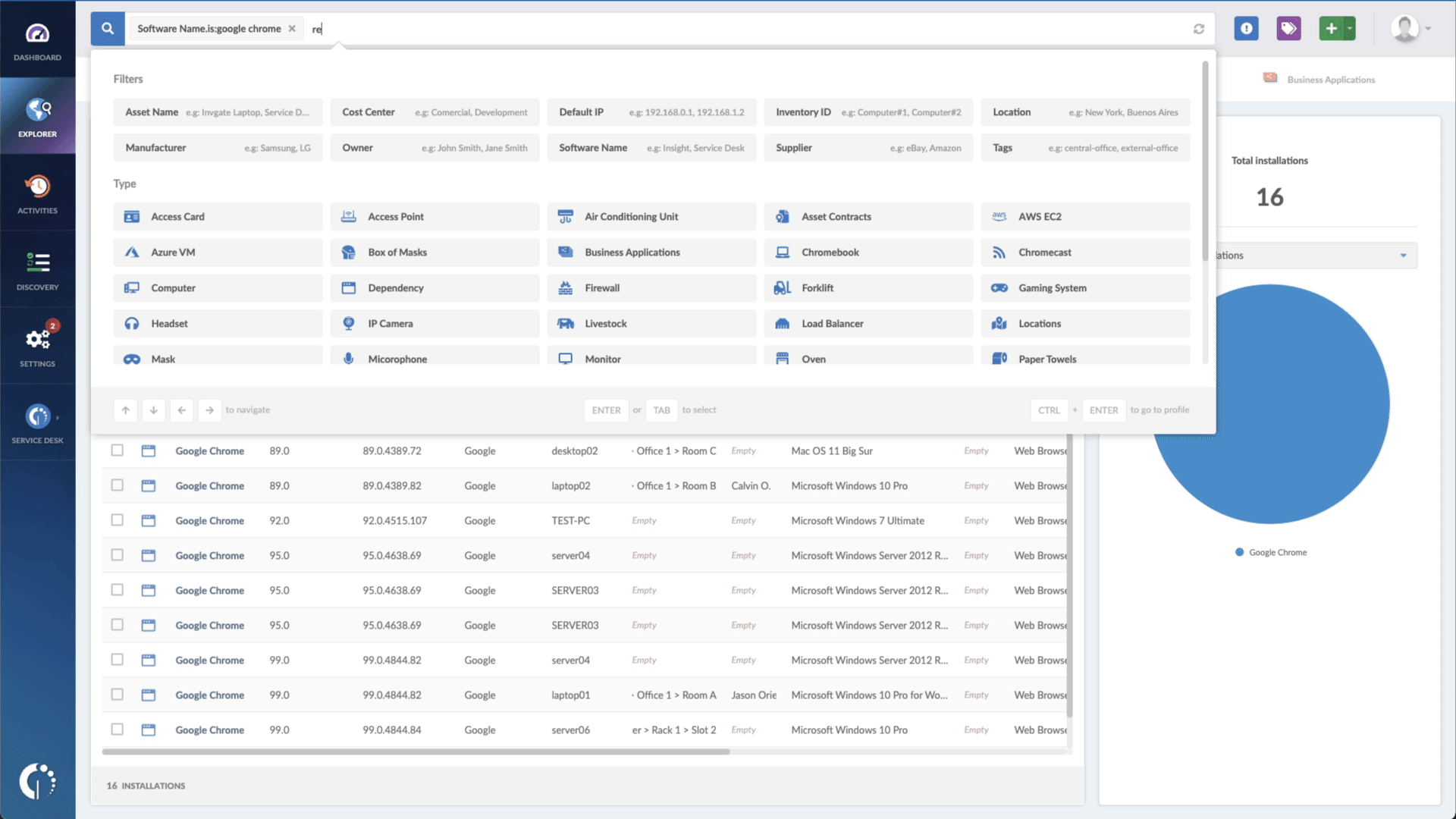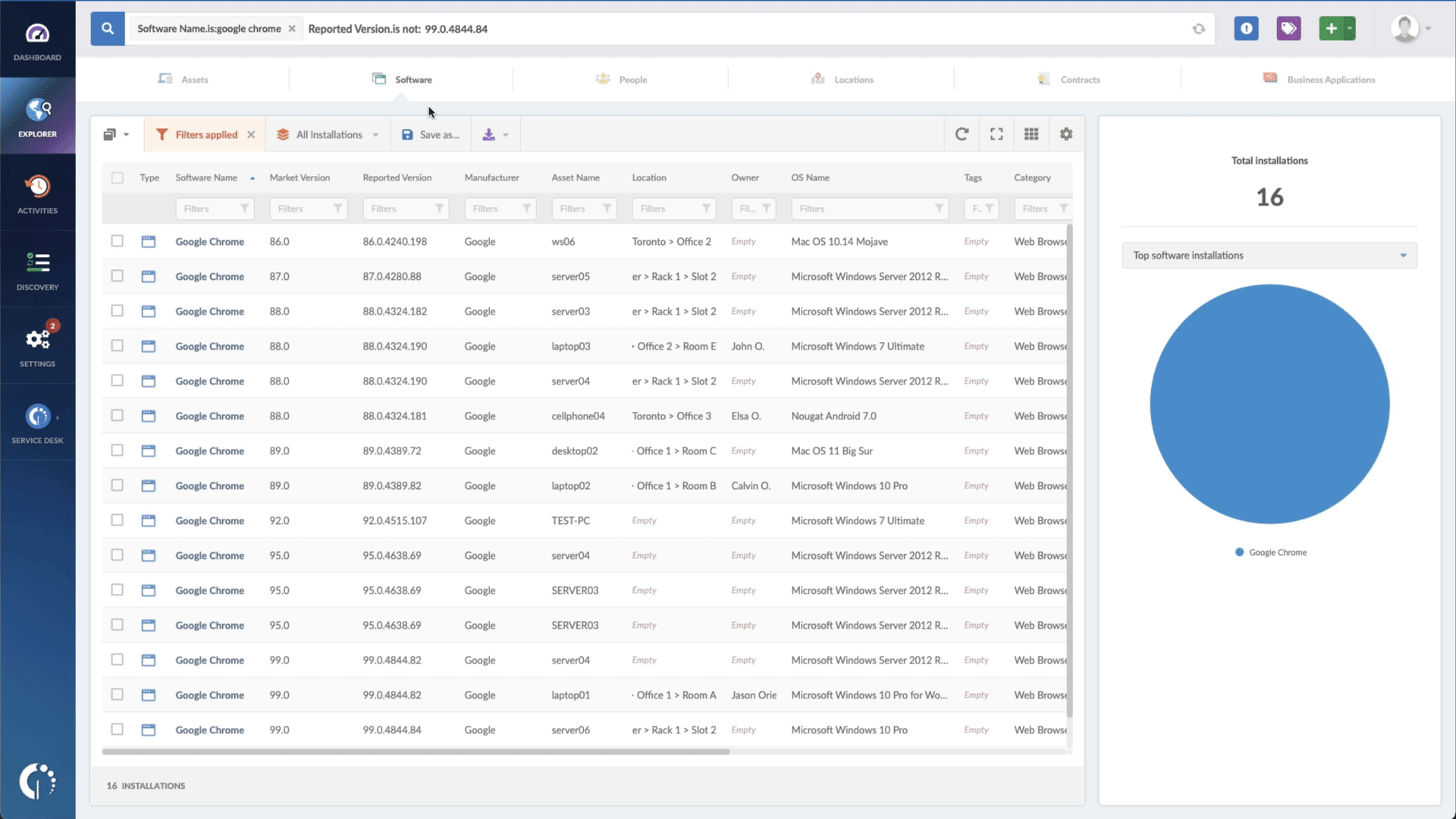
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Oracle’s patched version (depending on your product, you’ll find the security update number on Oracle’s webpage).
The bottom line
CVE-2020-14882 is a critical remote code execution vulnerability in Oracle WebLogic Server. It allows unauthenticated attackers to take full control of vulnerable systems, posing risks such as data theft, malware installation, and operational disruption. However, Oracle has released patches to address this vulnerability.
To identify devices exposed to CVE-2020-14882 and simplify Patch Management, InvGate Asset Management offers an efficient solution. Take action now to secure your systems by leveraging it's powerful features. Request a 30-day free trial and safeguard your organization from the risks associated with CVE-2020-14882 and other vulnerabilities.
















