In November 2020, a critical remote code execution vulnerability known as CVE-2020-1472 sent shockwaves through the Windows Server and Windows client operating systems. This exploit, which affects the Netlogon service, has the potential to grant attackers full control over vulnerable systems, leading to severe consequences.
In this article, we’ll give a comprehensive understanding of the CVE-2020-1472 vulnerability, its implications, and how InvGate Asset Management simplifies Patch Management.
Read on to gain a comprehensive understanding of CVE-2020-1472 and stay proactive in safeguarding your organization's network.
About CVE-2020-1472
CVE-2020-1472 is a critical remote code execution vulnerability in the Netlogon service of Windows Server and Windows client operating systems. The exploit was first disclosed in November 2020 and has been exploited in the wild.
How does CVE-2020-1472 work?
The vulnerability is caused by a flaw in the way that the Netlogon service handles certain types of authentication requests. The flaw allows an attacker to bypass the normal authentication process and execute arbitrary code on the vulnerable system.
What are CVE-2020-1472 risks?
An attacker who successfully exploits the vulnerability can gain full control of a vulnerable system, allowing them to steal data, install malware, or disrupt operations.
In addition, the vulnerability could be used to launch a denial-of-service attack against a vulnerable system, which could make the system unavailable to legitimate users.
Is CVE-2020-1472 fixed?
Yes, Microsoft has released patches for the vulnerability for all supported versions of Windows. They are available for download from the Microsoft Security Update Catalog.
In addition to installing the patches, users should also take the following steps to protect their systems:
- Use strong passwords and enable multi-factor authentication.
- Keep all software up to date.
- Use a firewall to block unauthorized access to your systems.
- Monitor your systems for suspicious activity.
How to find devices exposed to CVE-2020-1472
With InvGate Asset Management you can promptly find devices that have been impacted by the CVE-2020-1472 vulnerability. Follow these steps:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Windows” to filter all Microsoft Windows devices.
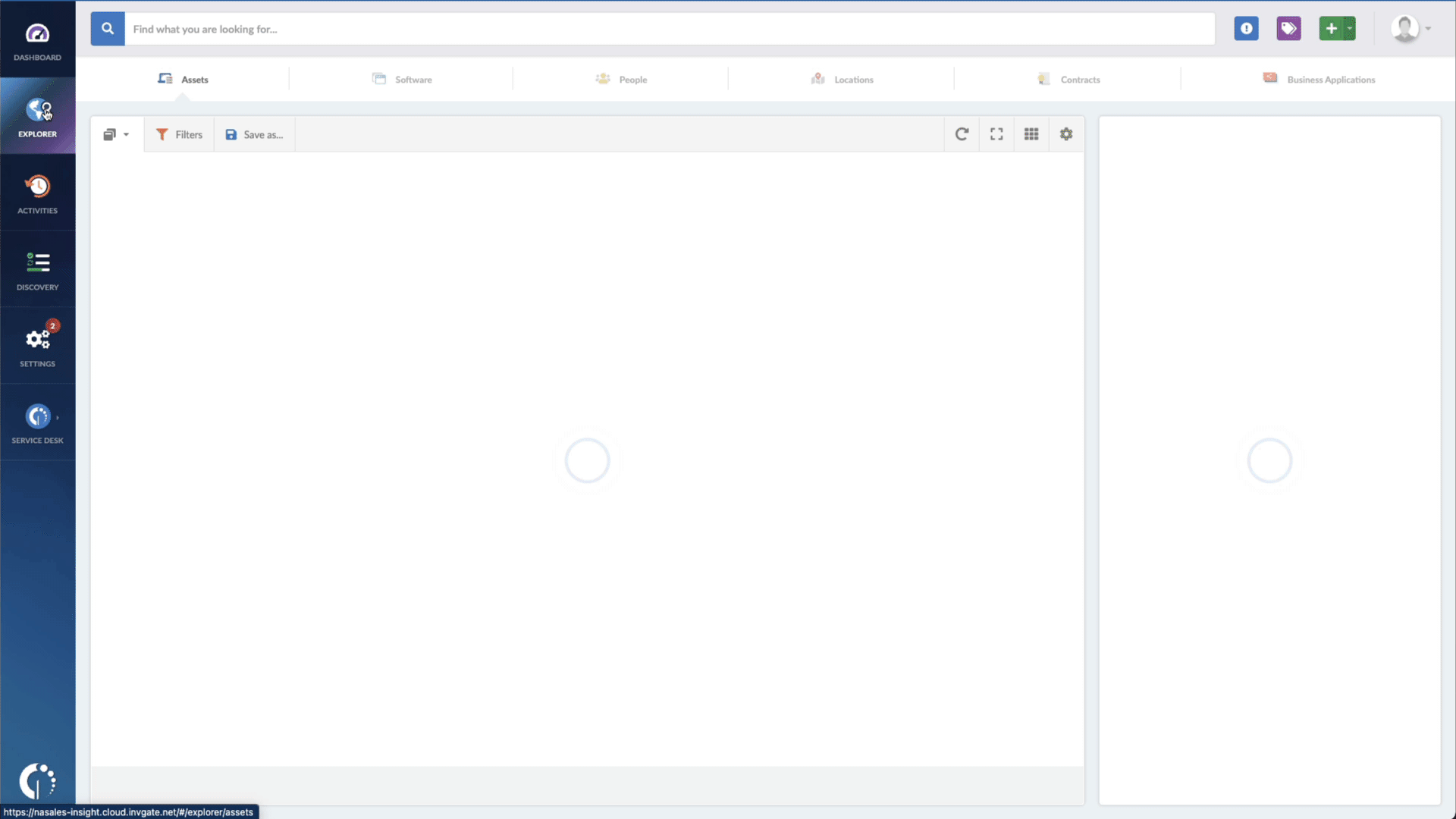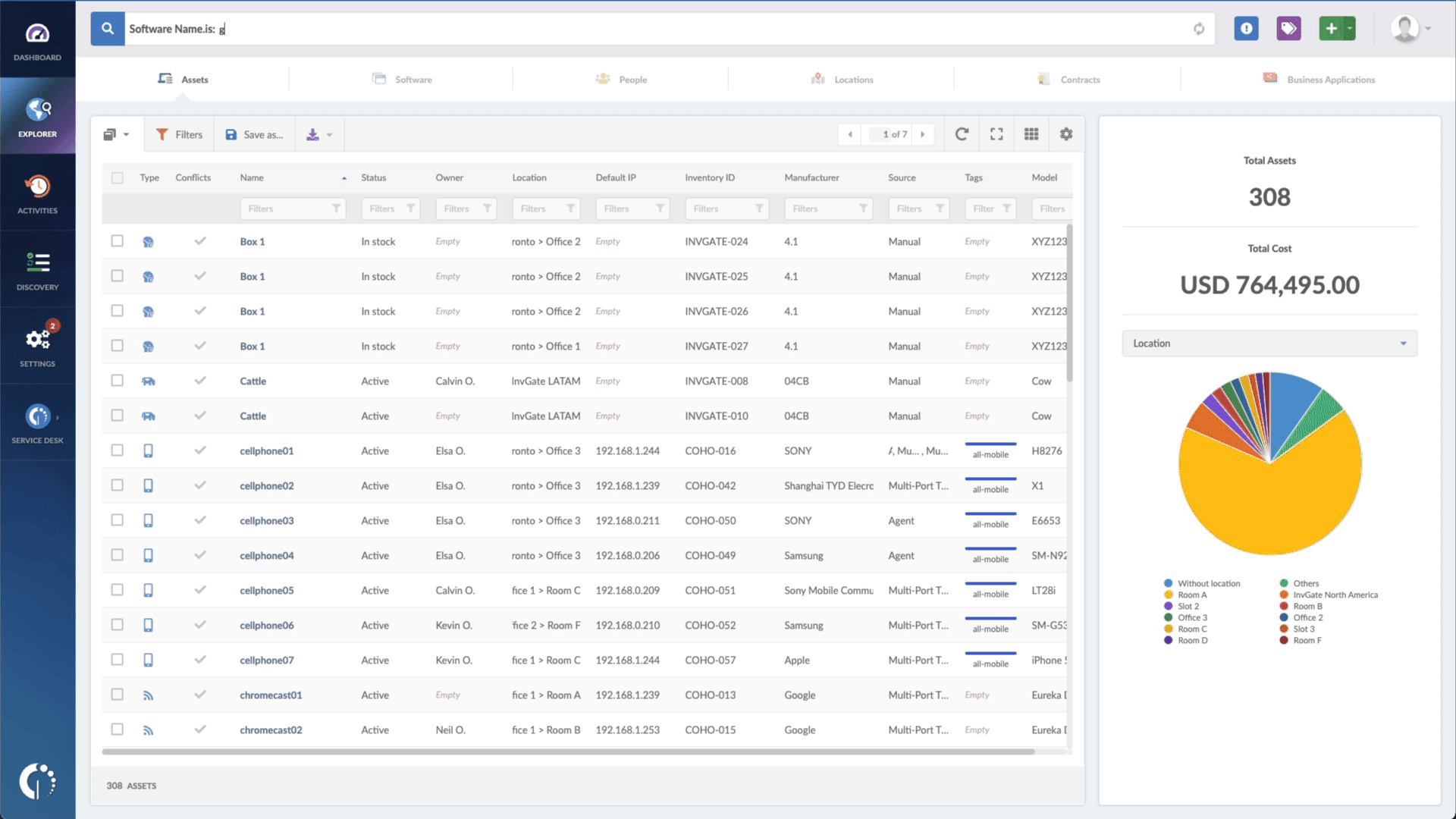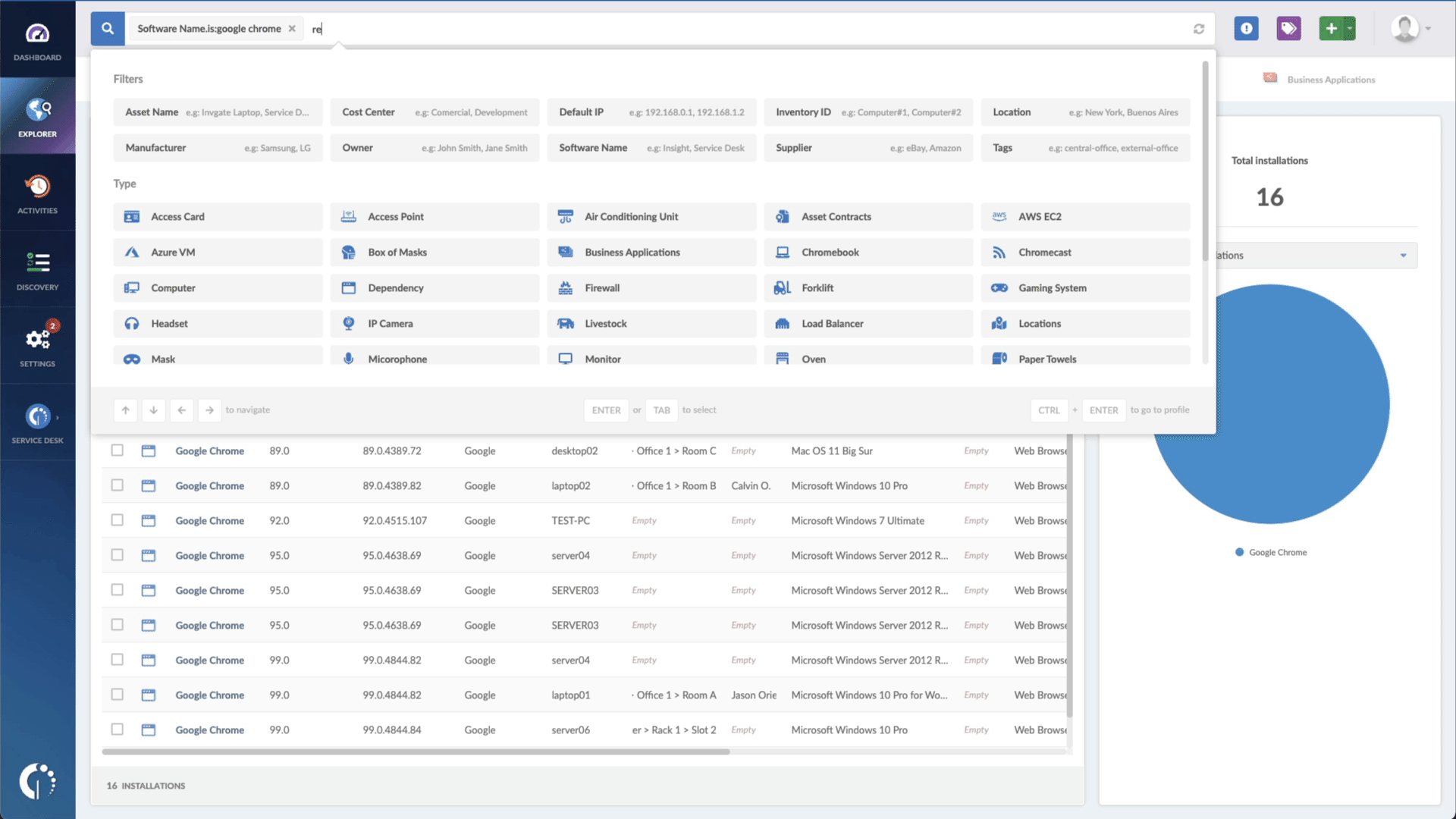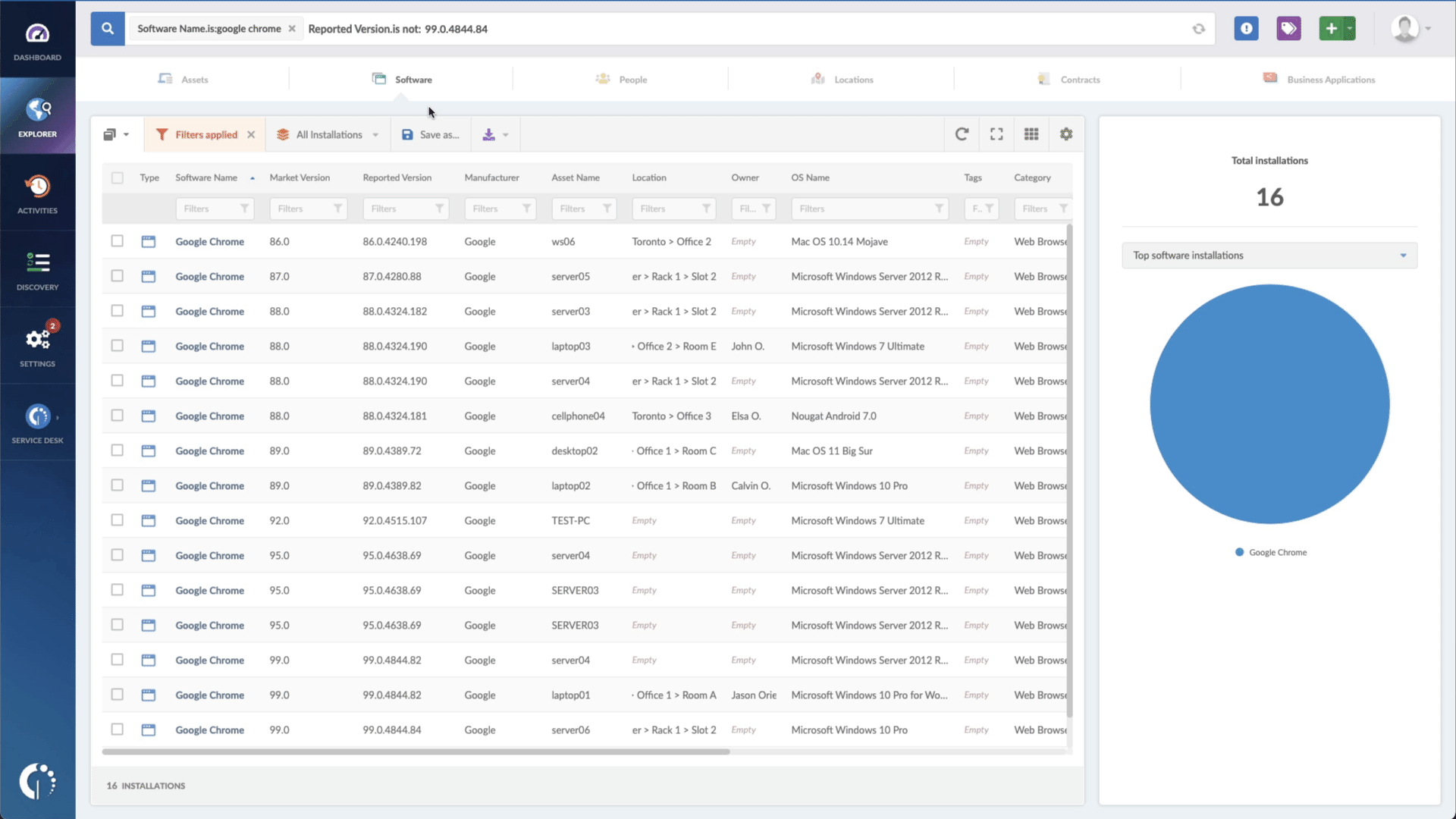
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your product, you’ll find the security update number on Microsoft’s webpage).
The bottom line
CVE-2020-1472 is a critical remote code execution vulnerability in the Netlogon service of Windows Server and Windows client operating systems. Exploiting this vulnerability allows attackers to gain full control over vulnerable systems, potentially leading to data theft, malware installation, or disruption of operations. However, Microsoft has released patches to fix this vulnerability for all supported Windows versions.
With InvGate Asset Management, the processes of identifying devices affected by CVE-2020-1472 and Patch Management are made easier. Request a 30-day free trial now and experience the benefits of InvGate Asset Management's capabilities.