If you're using the .NET Framework, SharePoint, or Visual Studio, it's crucial to stay informed about the latest security vulnerabilities and take proactive measures to protect your systems. One such vulnerability that requires immediate attention is CVE-2020-1147, a Remote Code Execution (RCE) exploit.
In this article, we’ll delve into the details of CVE-2020-1147, its potential risks, and how tools like InvGate Asset Management can simplify your Patch Management process.
Ready to secure your systems? Dive deeper into the details and learn how to safeguard your software from CVE-2020-1147.
About CVE-2020-1147
CVE-2020-1147 is a remote code execution vulnerability in the .NET Framework, Microsoft SharePoint, and Visual Studio.
The vulnerability exists when the software fails to check the source markup of XML file input. An attacker could exploit this vulnerability by sending a specially crafted XML file to a vulnerable system. The attacker could then execute arbitrary code on the system with user privileges.
The risks of not patching the CVE-2020-1147 vulnerability are significant. An attacker could exploit this vulnerability to gain control of a vulnerable system or steal data. This could have a devastating impact on an organization, including financial losses, data breaches, and reputational damage.
Is CVE-2020-1147 fixed?
Yes, Microsoft released patches for the CVE-2020-1147 vulnerability, and users are encouraged to install them as soon as possible.
The latest version of the software that includes the patch for CVE-2020-1147 is as follows:
- .NET Framework: 4.7.2
- Microsoft SharePoint: 2016
- Visual Studio: 2019
How to find devices exposed to CVE-2020-1147
You can efficiently detect devices that are impacted by the CVE-2020-1147 vulnerability using InvGate Asset Management. The following guidelines outline the steps to follow in order to accomplish this:
- Open InvGate Asset Management and go to the Explorer tab.
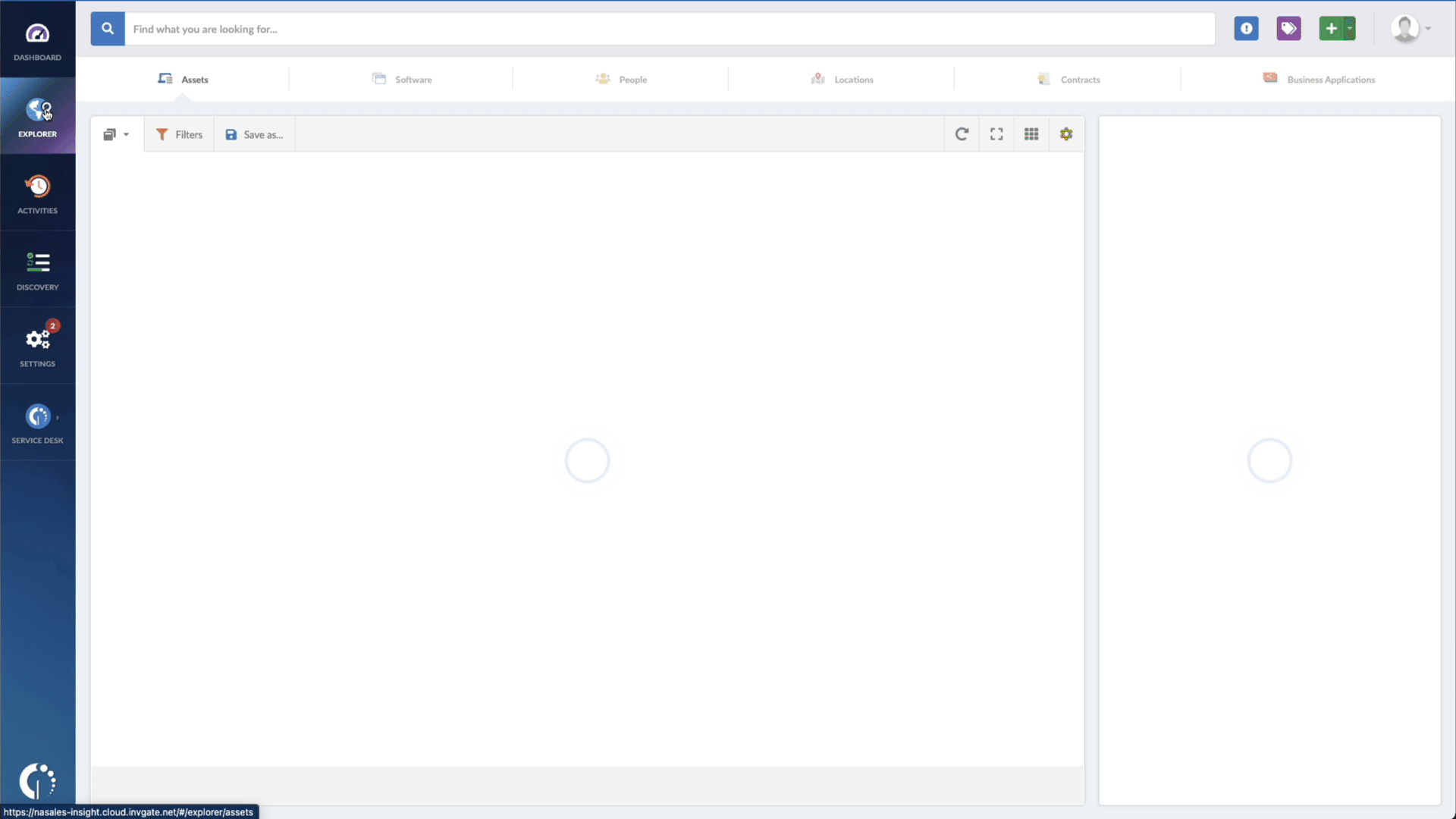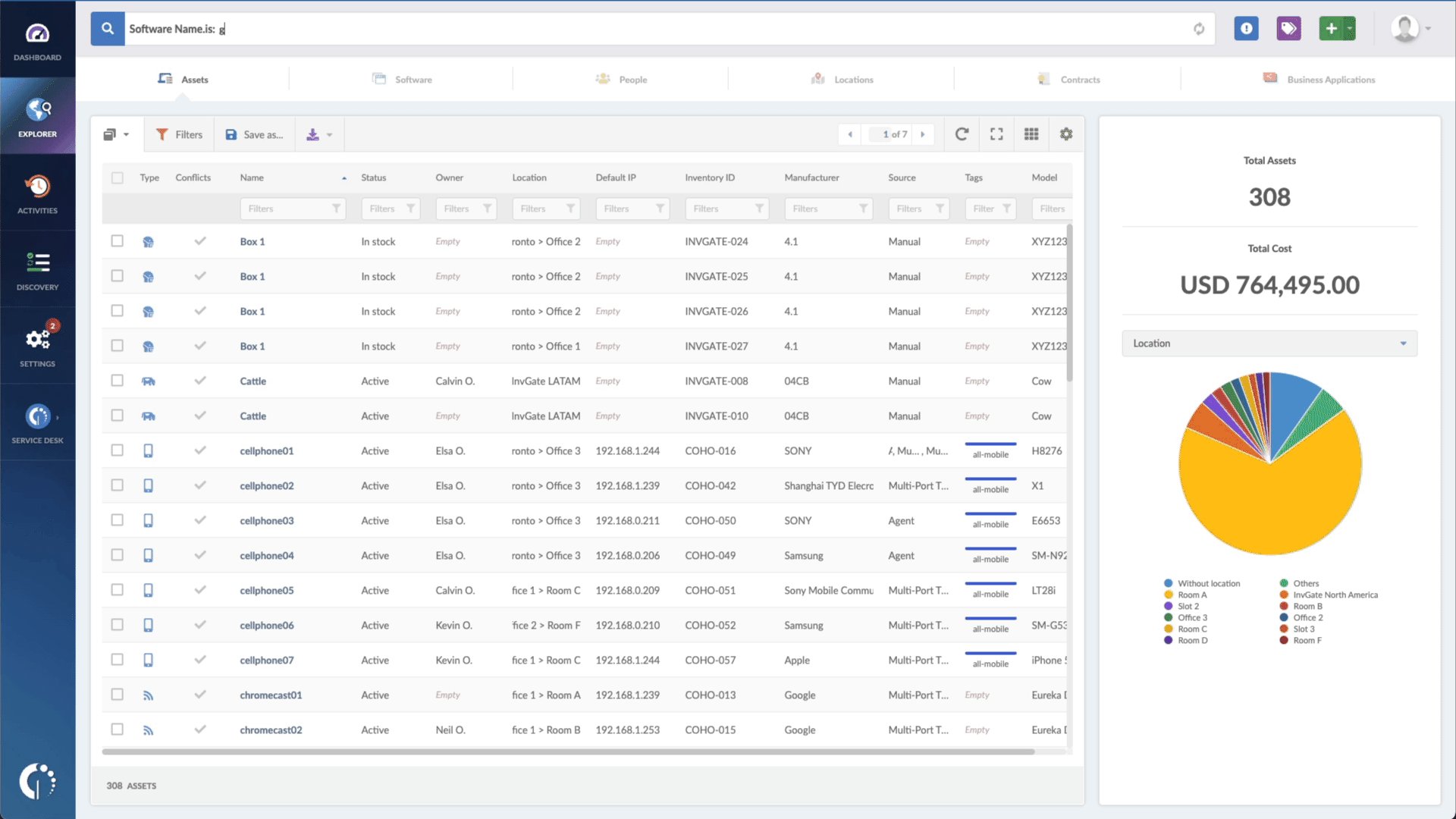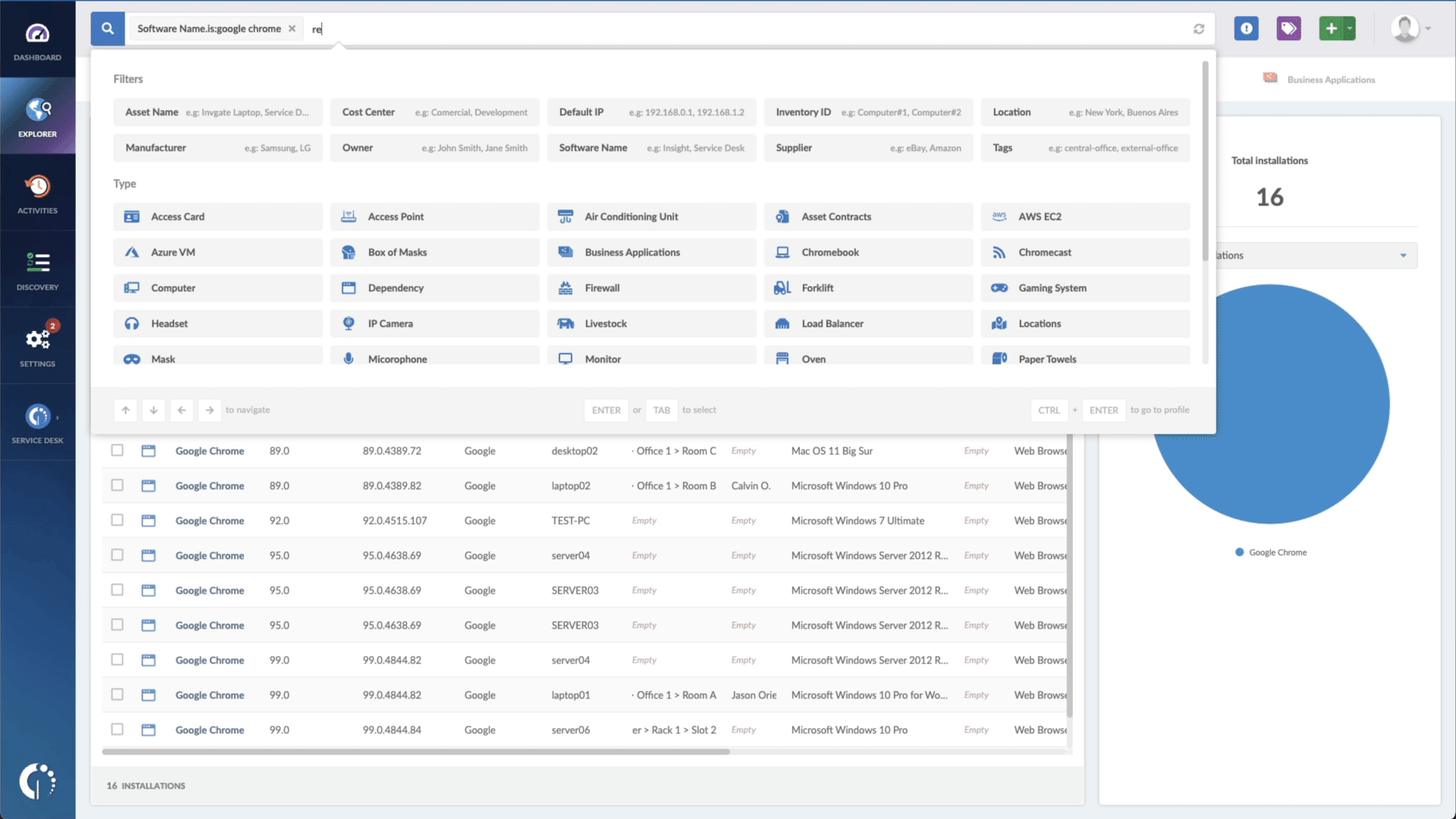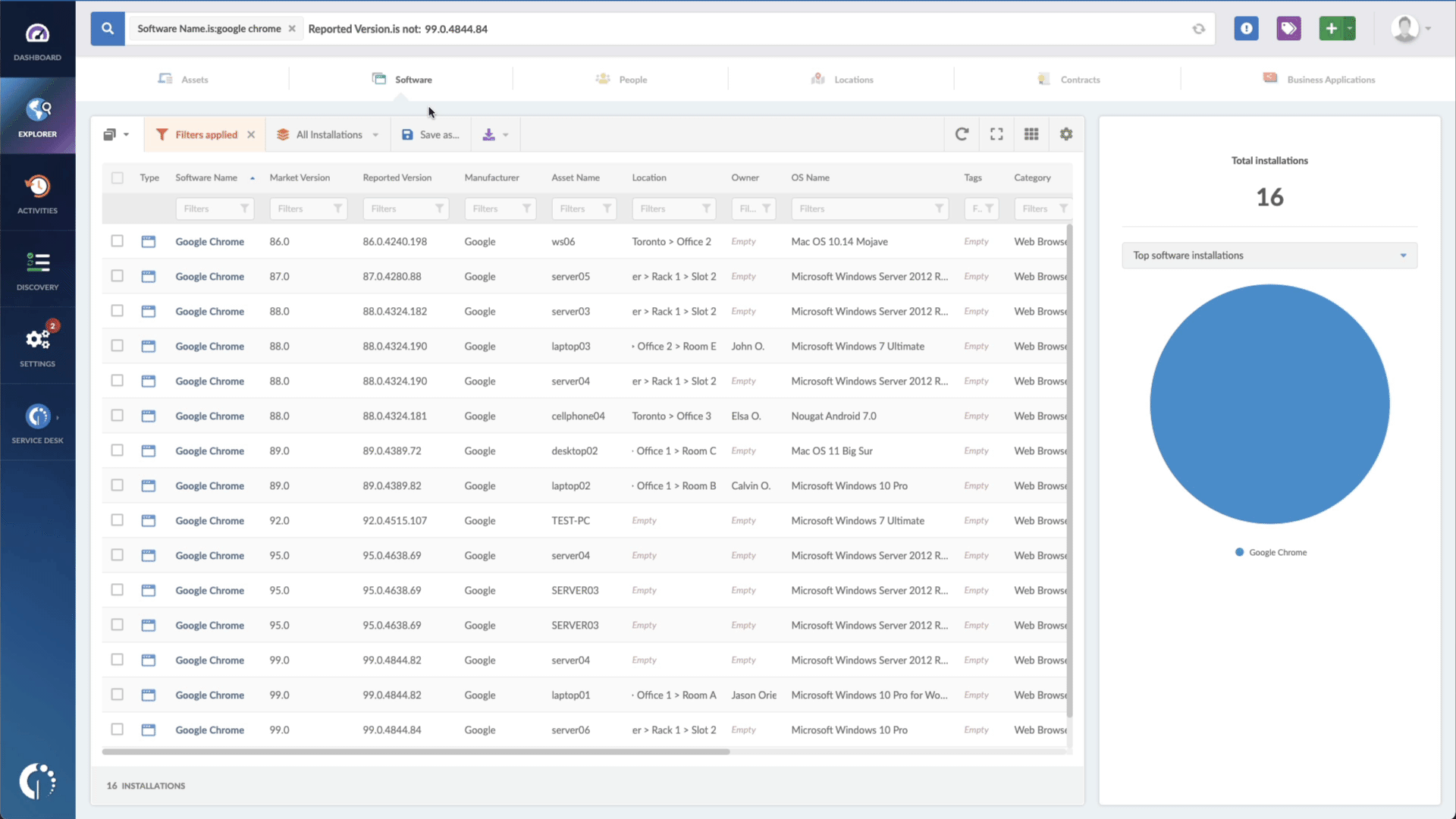
- Type in the Search bar “Software name, is:.NET Framework” (or Microsoft SharePoint or Visual Studio) to filter all the devices with the mentioned software.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (for .NET Framework, 4.7.2, for Microsoft SharePoint, 2016, and for Visual Studio, 2019).
The bottom line
CVE-2020-1147 is a critical Remote Code Execution vulnerability that affects the .NET Framework, SharePoint, and Visual Studio. Failing to patch this vulnerability exposes organizations and individuals to significant risks, including unauthorized code execution, privilege escalation, and data compromise.
Managing software patches can be a complex task, especially when dealing with large networks and numerous devices. InvGate Asset Management provides a streamlined solution by offering the capability to identify devices affected by the CVE-2020-1147 vulnerability swiftly.
To experience the simplified patch management capabilities of InvGate Asset Management, request a 30-day free trial. Make patch management a seamless part of your cybersecurity practices!
















