When transferring data between systems, it's extremely important to preserve integrity and confidentiality. There are protocols and procedures to do so. One of them is the Secure Copy Protocol (SCP); which is a method designed to securely pass on digital information.
The SCP protocol helps transferring files from a local to a remote host or between two remote hosts. It is a combination of the Remote Copy Protocol (RCP), which is used for transferring files, and the Secure Shell (SSH) protocol which provides encryption and authentication. The Secure Copy Protocol, therefore, is a way of transferring files preserving authenticity and confidentiality.
SCP is installed in places where users connect to download or upload files. Since it is a popular component, it is available for Linux, Windows servers and Mac OS.
How the SCP protocol works
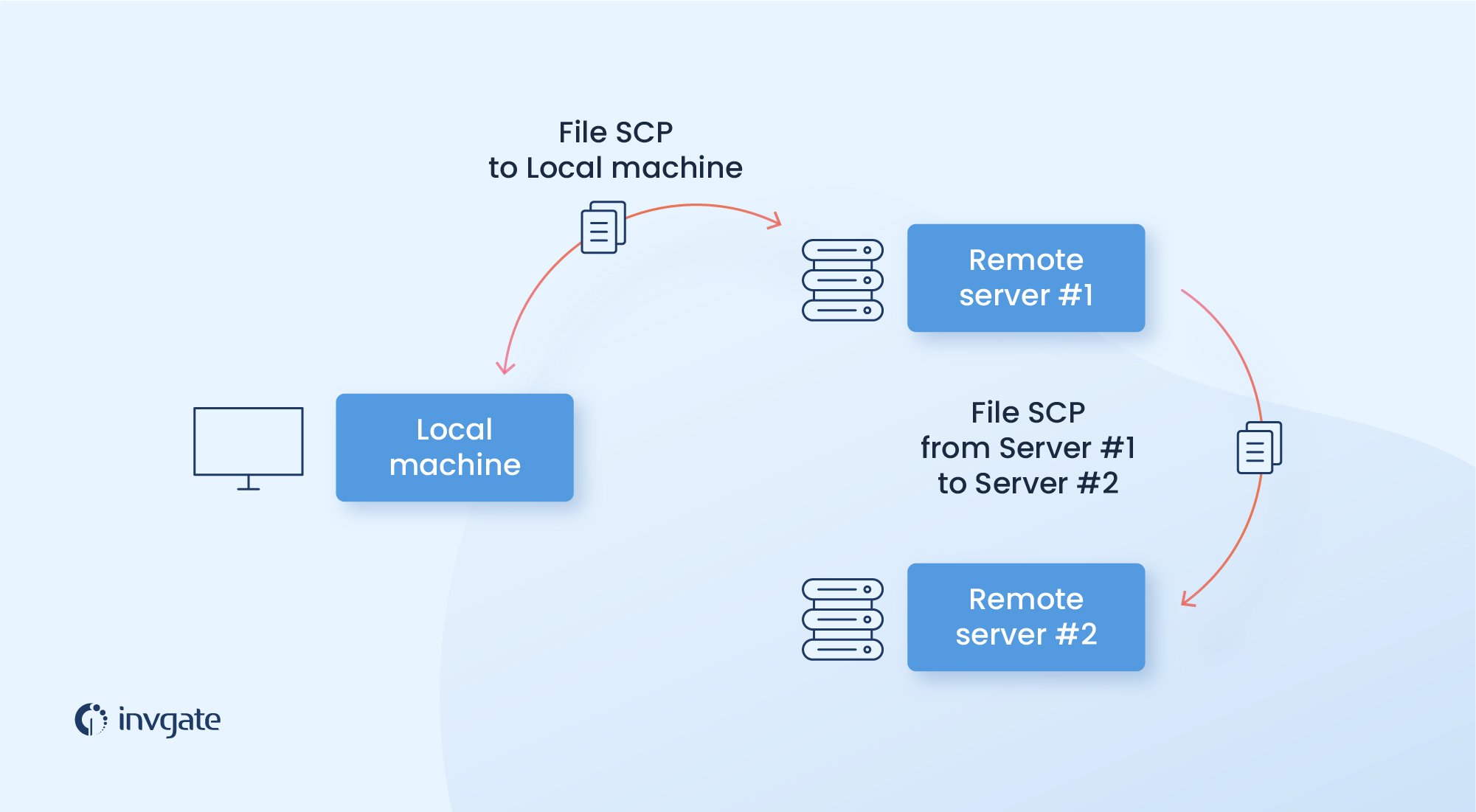
The SCP client can upload files to an SSH server or request files and directories for downloading. Then, the server controls if there are security risks and sends all the files that are available to be downloaded.
It is necessary to set up an SSH connection between the local host and the targeted host before performing the transfer through this protocol. In order to do so, it is required to enter the SSH login information or an authorized key for the public key authentication.
Once the SSH connection between the two hosts is set up, the SCP client will begin a secure copy process with two different available modes: source mode and sink mode. In the source mode, an SCP request in the source mode reads files from the targeted host and sends them back to the client; whereas in the sink mode, the client sends signals to the remote host indicating that there is input data to be written to the remote host.
Benefits and potential drawbacks
The major advantage of the Secure Copy Protocol (SCP) is that it provides security. The file transfer is performed using RCP and the SSH protocol, which offers encryption and authentication. SCP keeps the confidentiality of the data being transferred by blocking packet sniffers from extracting valuable information from the data packets
The major drawback to SCP is that it can only transfer files and is not as complete a process as other protocols. That being said, it should be taken into account that it can transfer files faster than SFTP protocol, which is widely considered the successor of SCP, as it runs on top of SSH as well.
It should also be noted that while the Secure Copy protocol is secure, it's not infallible. If a shell on the remote side prints out anything for non-interactive sessions, the local SCP process will interpret that output as SCP commands. This can lead to errors or even worse: the remote shell startup script could be malicious and send an exploit payload instead of the file expected.
On the other hand, in 2018, Harry Sintonen discovered some vulnerabilities in popular SCP implementations (including OpenSSH); which included the possibility of modifying permissions on a directory to overwrite arbitrary files and injecting terminal escape sequences to hide traces.
SCP use cases
The SCP protocol is a straightforward and powerful command that provides secure file transfer between hosts. It uses port 22 and runs on the session layer.
SCP is a native command in most operating systems, such as MacOS, Windows, or Linux. It can be found by simply writing the SCP command on the terminal. SCP can also be found in common network file transfer applications, such as PuTTy (ExtraPuTTy).
The most widely used SCP client is the SCP Command Prompt, which is built into most SSH implementations. The SCP command is the safe analog of the RCP command. The SCP protocol must be part of all SSH servers that want to provide the SCP service, just as SCP works as an SCP server as well.
The difference between CP and SCP
Both commands need to have a source and destination file-system location to perform a copy operation. But the main difference is that the SCP requires one or both of the locations to be on a remote system.
SFTP and FTPS server tools:
- SolarWinds Serv-U Managed File Transfer Server offers a free trial. It is a Secure FTP server that supports SFTP, FTPS, and FTP, for Windows and Linux.
- Files.com is a cloud-based file platform with a built-in FTP and SFTP server. Being based on a remote server, this service is able to offer many more features than a traditional SFTP server.
- .CrushFTP is a popular secure FTP server and FTPS server tools. It supports SFTP, FTPS, SCP, and HTTPS.
Common mistakes with SCP
A common mistake that users might encounter in Linux is the “SCP permission denied” error. The message pops up when the user is trying to transfer encrypted files from one Linux system to another.
When you run the SCP command, Linux will generate an encrypted copy of a specified file, folder, or directory, and deposit that copy to the specified location.
The SCP or secure copy helps you copy files or folders between two Linux systems, which can be local or remote.
Most Linux users will run into the “SCP permission denied” error at some point, due to very simple errors or missteps during command execution. Here are several common mistakes that might lead to that; with their corresponding solutions:
- You have typed or used an invalid username or password when using the command. To solve this, double check the information included.
- The file could be in a different location than what the one being specified in the SCP command; and The SCP command requires you to know where your target files are located. Otherwise, the command won't be able to find them. That's why it's important to check the files have not been moved to another location.
- The file might have restricted read or write access (or both). To solve this, you can log in to the remote directory and check your Read/Write access. If your user does not have Read/Write access to the directory, then the access should be assigned manually.
- Your user profile does not have ownership over the directory in which you are trying to transfer the file from. This can be solved with the following command: $ sudo chown -R “username”:”username” “path to your remote directory”
Frequently asked questions
What is the relationship between SCP and SSH?
The SCP is a network protocol, based on the RCP protocol, which supports file transfers between hosts on a network. Besides, SCP uses Secure Shell (SSH) for data transfer and uses the same mechanisms for authentication, in order to ensure the authenticity and confidentiality of the data being transferred.
What is the SSH File Transfer Protocol?
The SSH File Transfer Protocol (also Secure File Transfer Protocol, or SFTP) is a network protocol that provides file access, file transfer, and file management over any reliable data stream. It provides a custom interactive prompt for exploring the remote file system and it also allows scripts with a pre-written series of commands.