Apple has recently released a set of security updates for its operating systems, including macOS, iOS, iPadOS, and watchOS. Among the fixes is a patch for a zero-day vulnerability in the WebKit component that could potentially be exploited for remote code execution on older iPhones and iPads running iOS v12.
About CVE-2022-42856
The vulnerability, known as CVE-2022-42856, is a type confusion flaw in WebKit that was flagged by Clément Lecigne of Google’s Threat Analysis Group. According to Apple, the vulnerability could be exploited by a remote attacker to execute arbitrary code. The company has patched the vulnerability in November and December 2022 in the iOS 16 and 15 branches, respectively.
However, Apple has also warned that this issue may have been actively exploited against versions of iOS released before iOS 15.1. This means that users of older iPhones and iPads running iOS v12 should update to the latest available version of iOS to protect against this vulnerability.
Apple has not shared any details of the attacks leveraging this vulnerability, but it is a good reminder of the importance of keeping software up-to-date and applying security patches as soon as they become available.
In addition to the CVE-2022-42856 vulnerability, the security updates for macOS, iOS, iPadOS, and watchOS include a number of other fixes and improvements. The security update for the most recent macOS version (v13, or Ventura) is more hefty than those for Monterey (v12) and Big Sur (v11), but many of the fixes overlap. Likewise, iOS and iPadOS v16.3 deliver more fixes than v15.7.3 for those two OSes.
Security updates on macOS 13
One notable feature of the macOS Ventura update is the inclusion of two new security features: Advanced Data Protection for iCloud and Security Keys for Apple ID. These features were announced and partially rolled out for testing by Apple late last year, and are now available for all users of macOS Ventura.
Advanced Data Protection for iCloud expands end-to-end encryption to more data categories in iCloud, including iCloud Backup, Notes, and Photos. This means that all of these categories of data are now protected by strong encryption, ensuring that they can only be accessed by the user and those they choose to share them with.
Security Keys for Apple ID adds the necessary support so users can use physical security keys as their second authentication factor. This means that users can now use a physical security key, such as a USB key or a Bluetooth device, in addition to their password or Face ID to sign in to their Apple ID account. This provides an additional layer of security that can protect against phishing attacks and other forms of account takeover.
How to find devices with Apple devices exposed to CVE-2022-42856
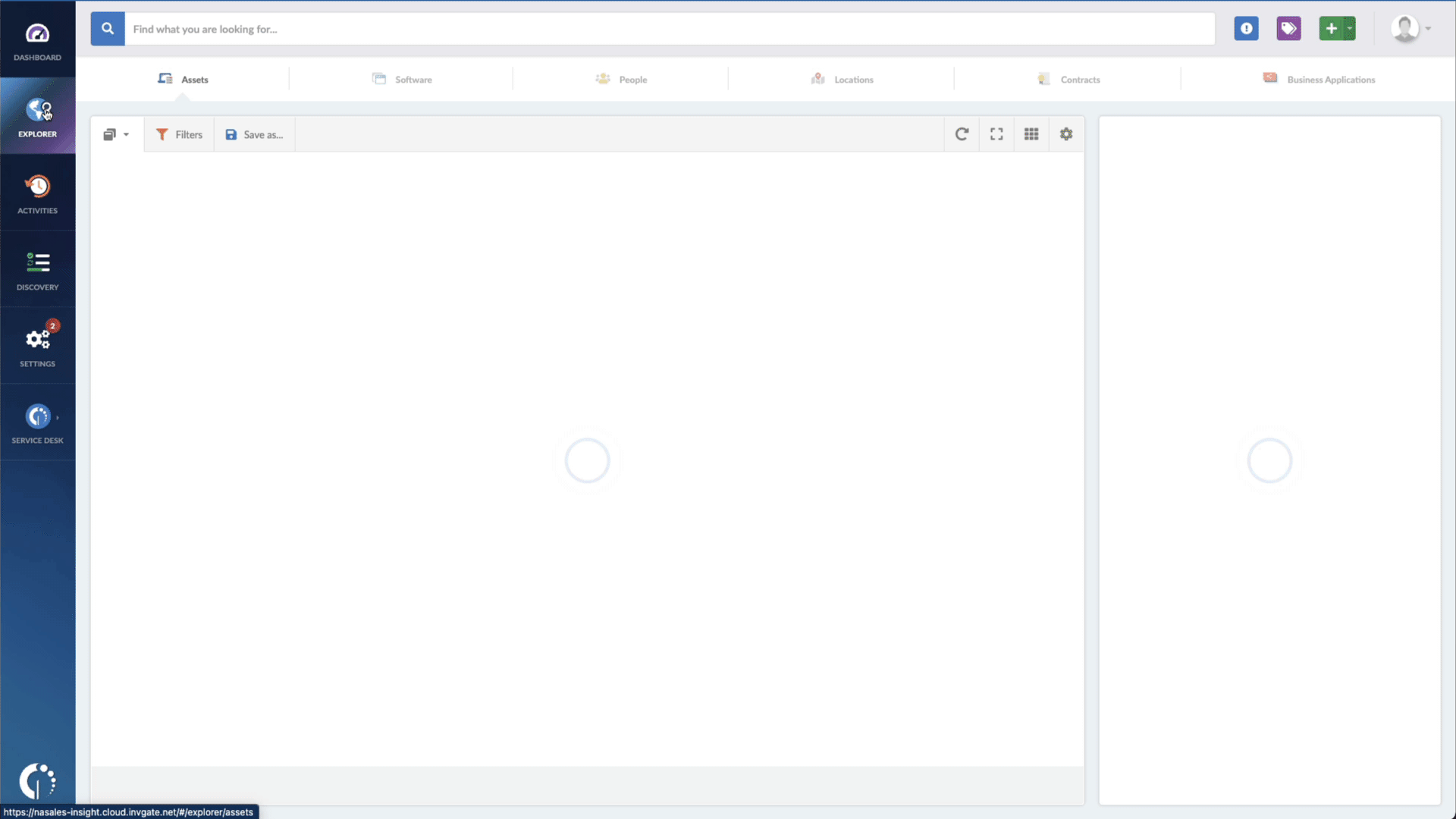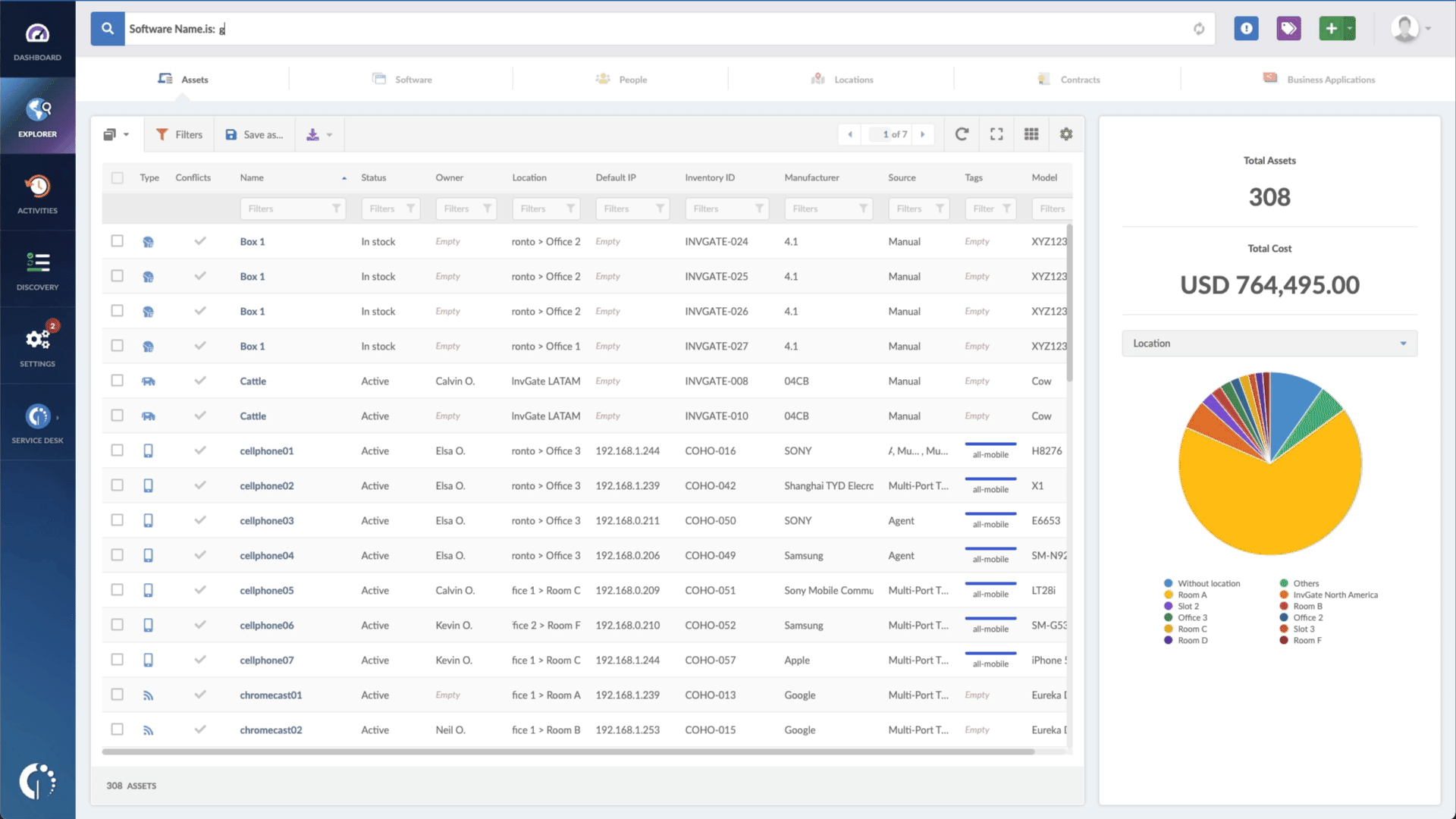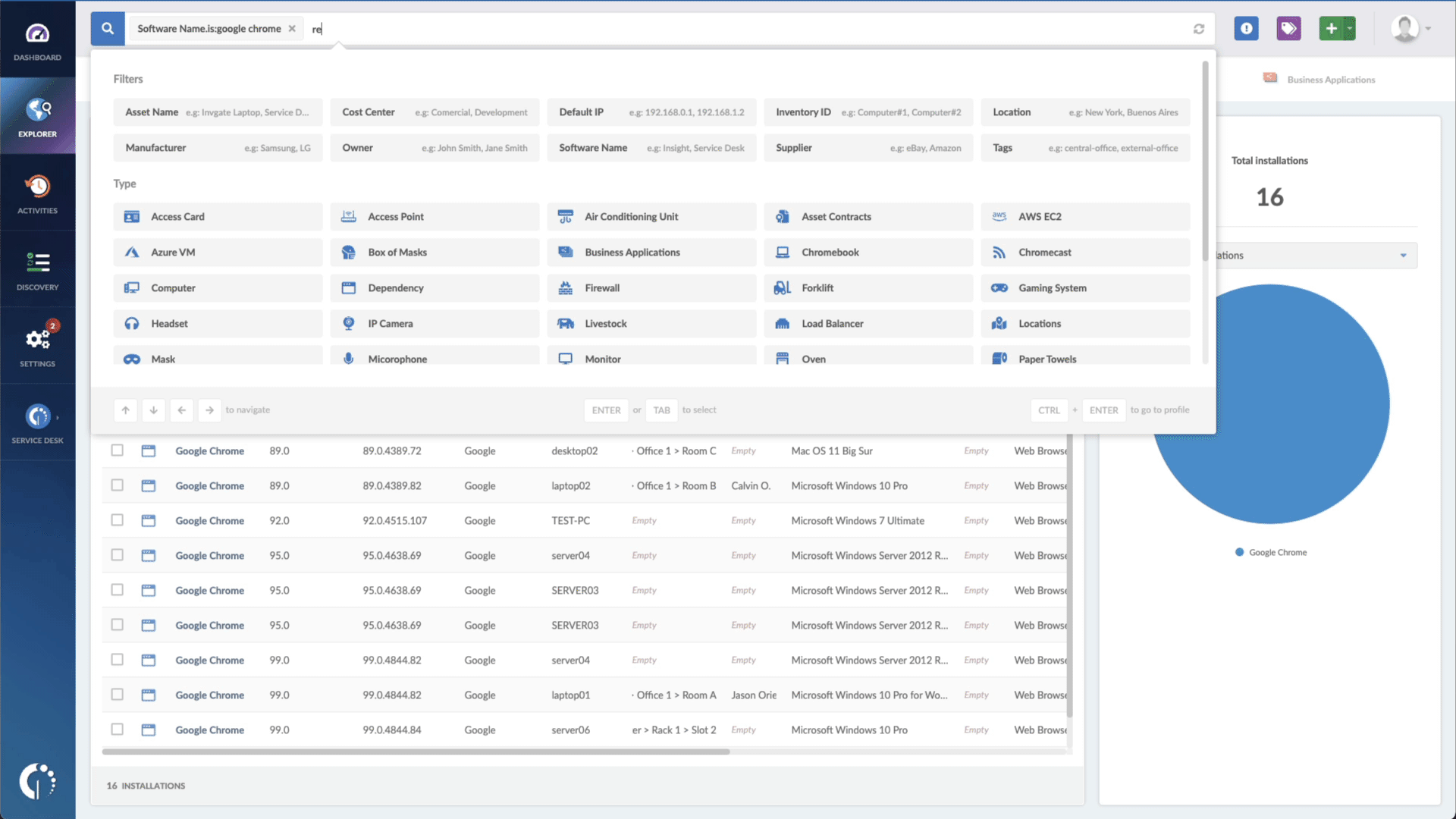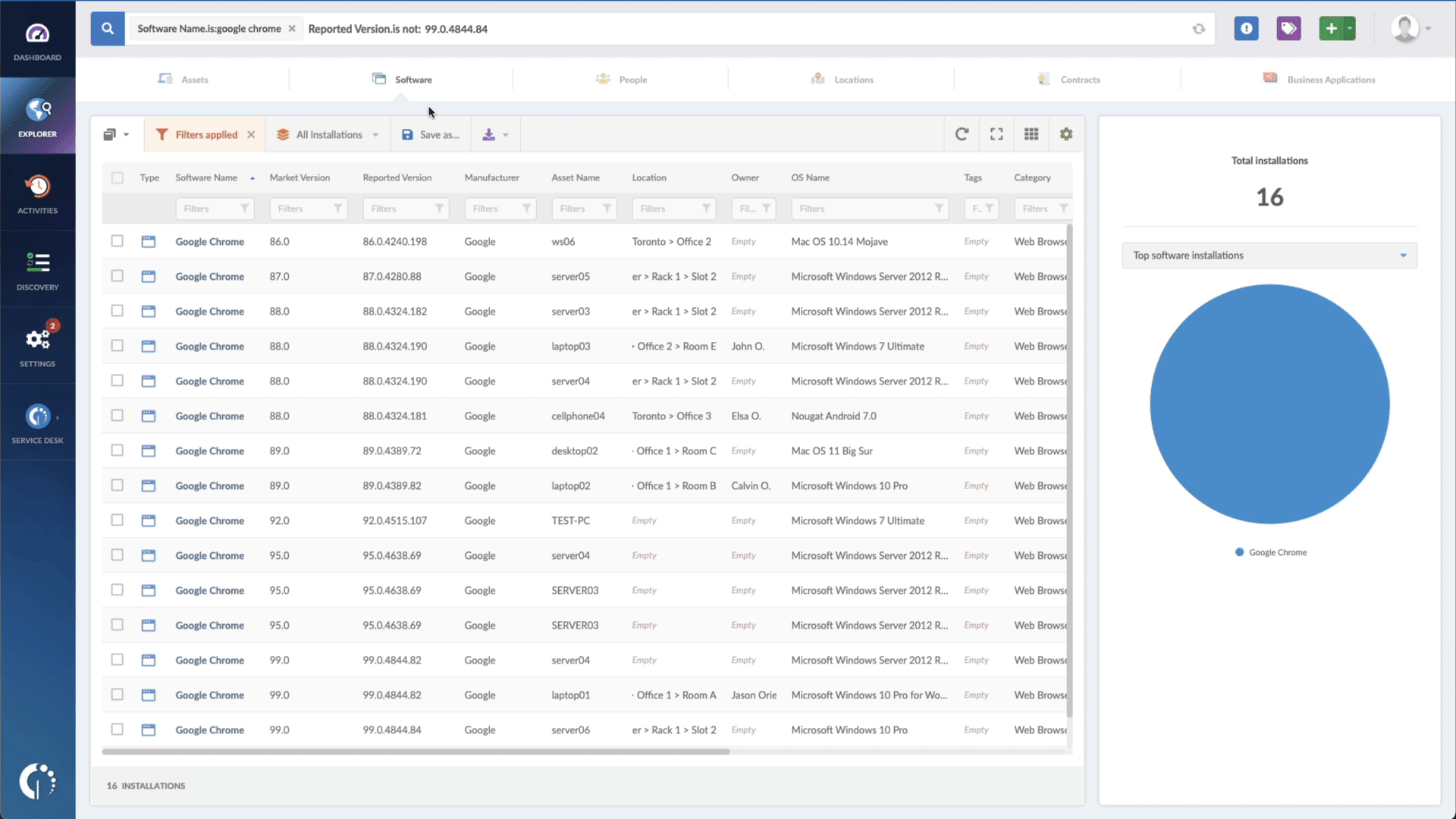
With InvGate Asset Management, it’s very easy to see which assets need updating. Just open Insight, go to Explorer, and type in on the Search bar “Software name, is: MacOS.” Now you have a list of all the devices where this particular operating system is installed. Then, add another filter to the Search bar to see all the outdated assets. In order to do that, add the following filter: “Reported version, is not:” and paste iOS’s patched version (iOS 12.5.7).
That’s it! With a few clicks, you created a list of devices that need to be updated as soon as possible. You can export it in CSV and give it to one of your agents to patch or create a ticket so they can be manually updated.
Don't let the next Chrome zero-day exploit catch you off guard, try InvGate Asset Management now, and forget about security issues once and for all!