As an IT professional, it's crucial to stay up-to-date with the latest security vulnerabilities and patches. Apple has recently released a fix for a zero-day vulnerability (CVE-2022-42827) that was being actively exploited by attackers to compromise iPhones. This out-of-bounds write issue in the iOS and iPadOS kernel can be exploited by a malicious application to execute arbitrary code with kernel privileges.
About CVE-2022-42827
CVE-2022-42827 is an out-of-bounds write issue in the iOS and iPadOS kernel that allows a malicious application to execute arbitrary code with kernel privileges. This vulnerability can be exploited by attackers to compromise iPhones.
Apple has fixed this vulnerability with improved bounds checking in iOS 16.1 and iPadOS 16, which are available for iPhone 8 and later, iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, and iPad mini 5th generation and later. The security updates also include fixes for 19 additional CVE-numbered security issues, such as a flaw in the Bluetooth component that could allow an app to record audio using a pair of connected AirPods, and many other code execution holes.
It's worth noting that Apple has released security updates for macOS Big Sur, Monterey, and Ventura (the latest version of the OS, with new security and privacy features) as well. Ventura's update is particularly sizeable, with fixes for 113 issues (40 of which are in the Vim text editor). Additionally, Safari, tvOS, and watchOS security updates have also been released.
As an IT professional, it's important to make sure all devices are updated with the latest security patches to protect against potential attacks. Apple has provided patches for these vulnerabilities, so be sure to update your devices as soon as possible. It's also recommended to regularly check for software updates and patches to ensure devices are always secure. Stay informed and take necessary precautions to keep your systems secure.
How to find devices with Apple devices exposed to CVE-2022-42827
With InvGate Asset Management, it’s very easy to see which assets need updating. Just open Insight, go to Explorer, and type in on the Search bar “Software name, is: iOS.” Now you have a list of all the devices where this particular operating system is installed. Then, add another filter to the Search bar to see all the outdated assets. In order to do that, add the following filter: “Reported version, is not:” and paste iOS’s patched version (iOS 16.1).
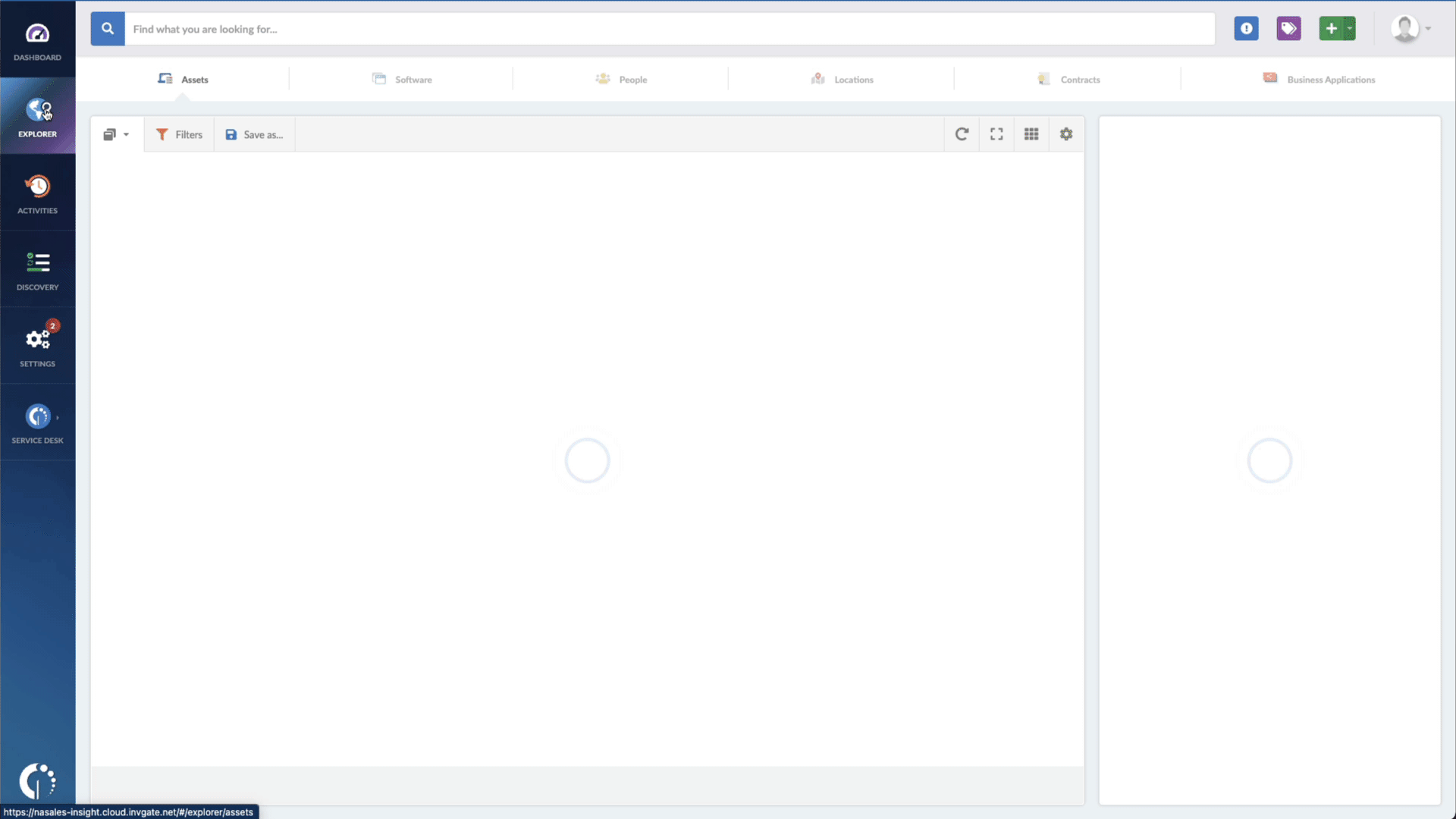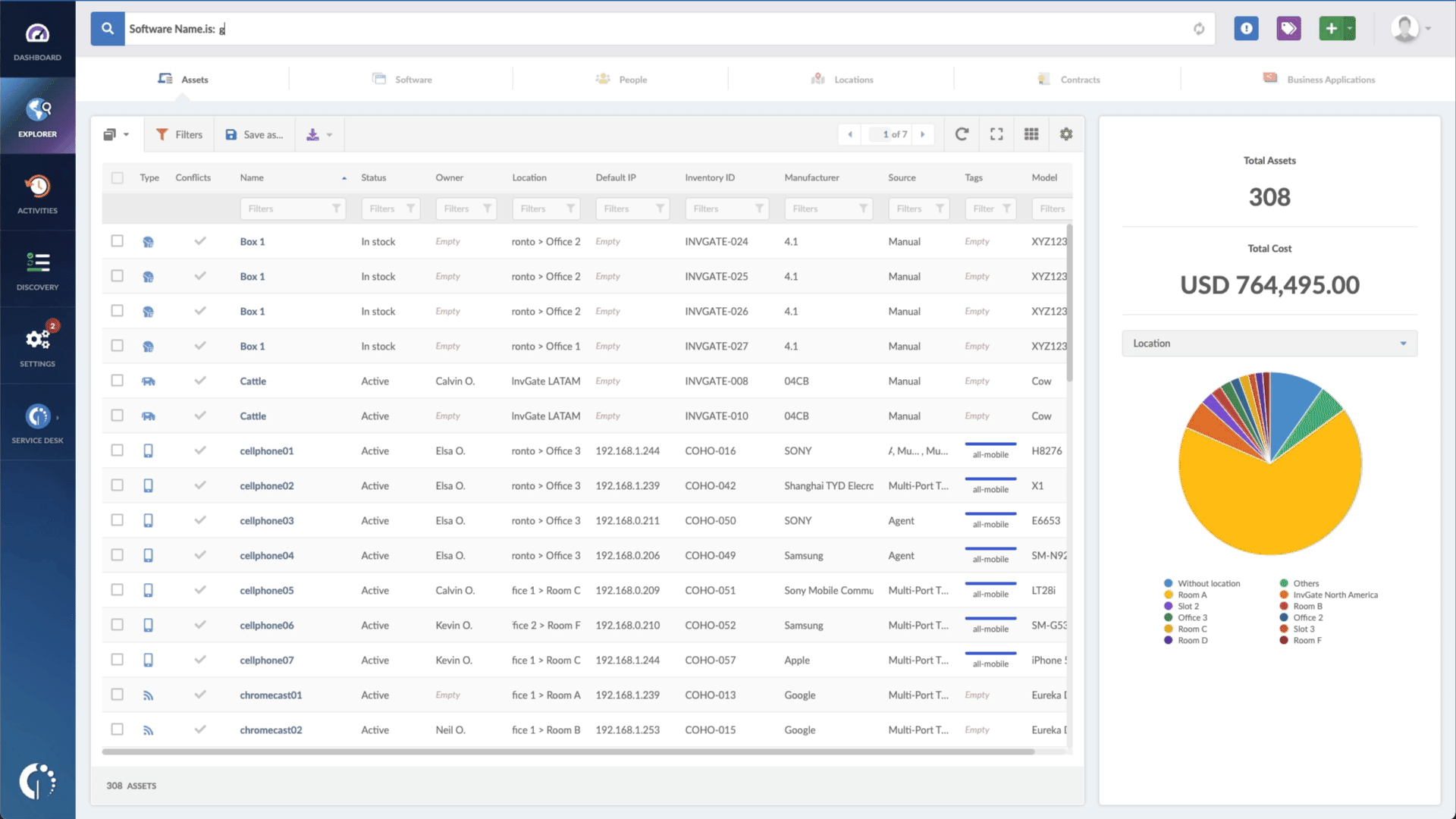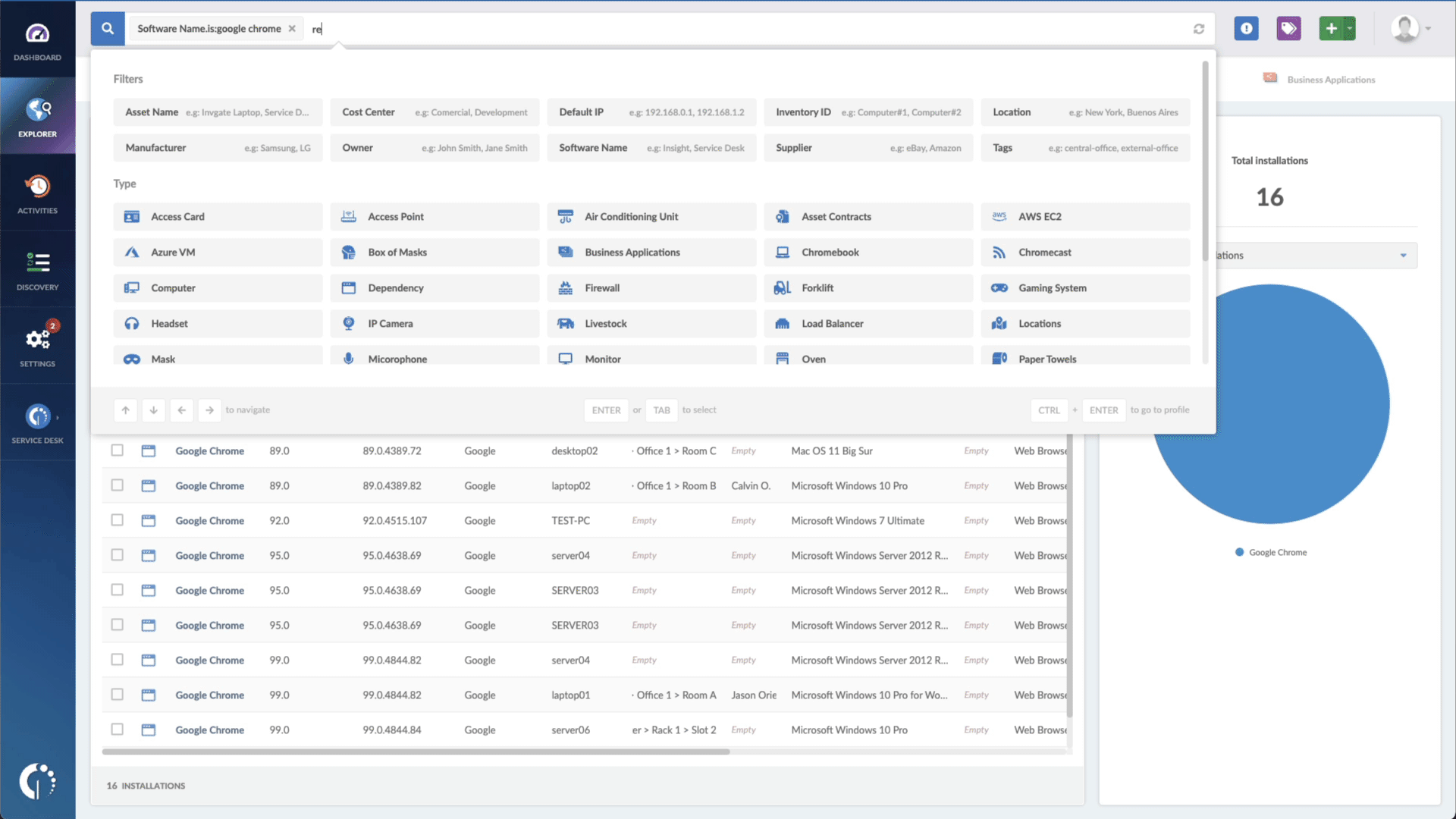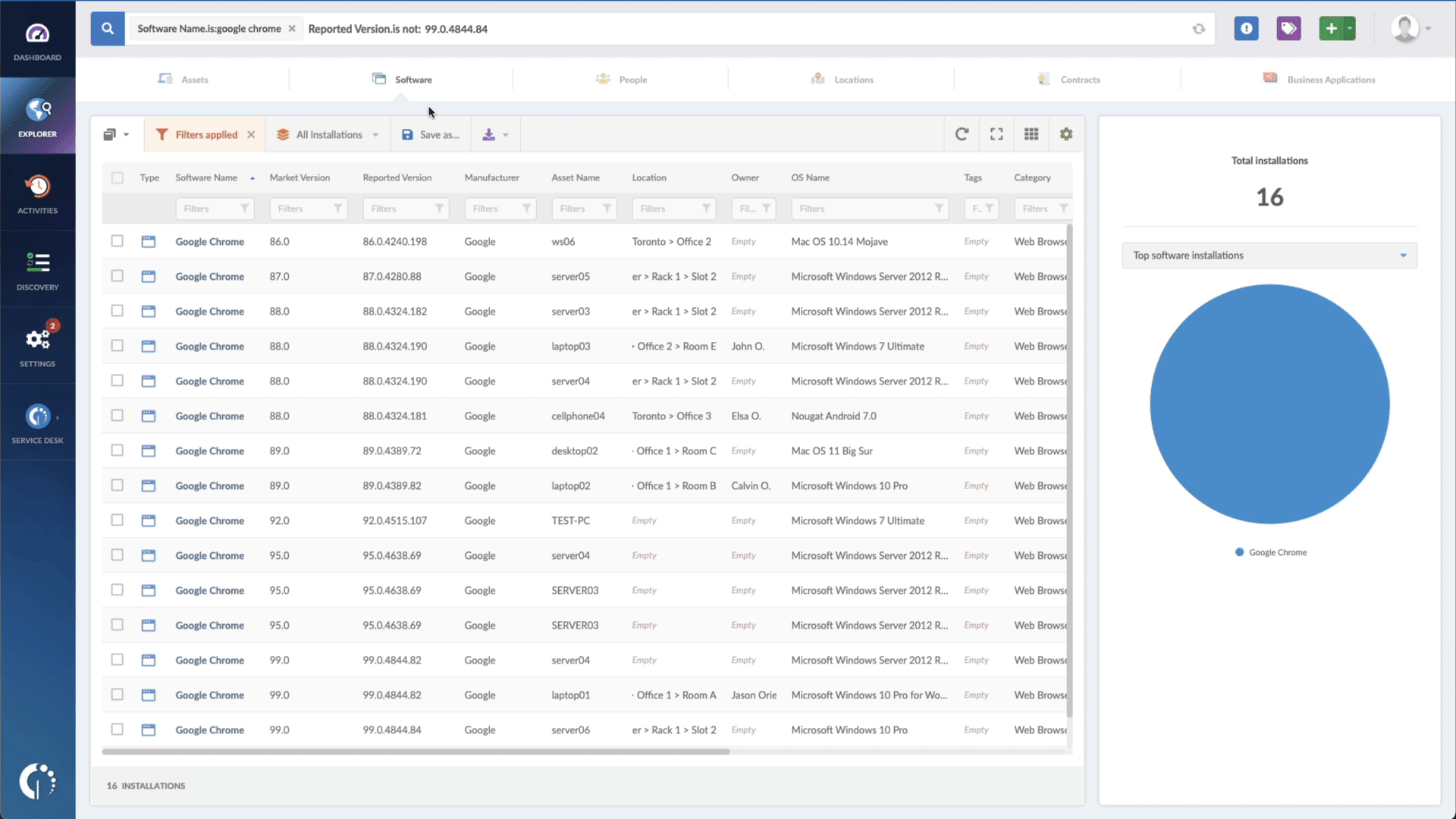
That’s it! With a few clicks, you created a list of devices that need to be updated as soon as possible. You can export it in CSV and give it to one of your agents to patch or create a ticket so they can be manually updated.
Don't let the next Chrome zero-day exploit catch you off guard, try InvGate Asset Management now, and forget about security issues once and for all!
















