As cyber threats continue to evolve, individuals and businesses must stay informed about the latest vulnerabilities. In December 2022, Fortinet issued a security advisory regarding CVE-2022-42475, a critical vulnerability that affects FortiOS, the operating system used by Fortinet's network security devices.
CVE-2022-42475 can potentially allow attackers to bypass security measures and gain unauthorized access to sensitive data, making it a significant cybersecurity threat. In this article, we'll provide an overview of CVE-2022-42475, its risks, and how InvGate Asset Management can help you mitigate the threat.
If you're concerned about the security of your Fortinet network devices and want to learn more about CVE-2022-42475, keep reading!
About CVE-2022-42475
CVE-2022-42475 is a heap-based buffer overflow vulnerability found in FortiOS SSL-VPN that received a CVSSv3 score of 9.3. FortiOS is a popular operating system used by Fortinet in its firewall products, and SSL-VPN is a type of virtual private network (VPN) that allows remote access to internal networks using the SSL/TLS protocol.
This vulnerability allows attackers to execute arbitrary code or cause a denial of service (DoS) condition.
The exploit works by sending a specially crafted SSL/TLS message to the SSL-VPN server. Once the server receives this message, it triggers a buffer overflow, which allows an attacker to execute arbitrary code on the target system. This type of attack can lead to data theft, system compromise, and other serious consequences.
CVE-2022-42475 affects several FortiOS versions, and Fortinet has released patches for this vulnerability. Organizations and users are strongly advised to update to the latest software version as soon as possible. Additionally, companies should review their security policies and ensure that all users know the importance of keeping their systems up to date with the latest security patches.
How to find devices exposed to CVE-2022-42475
You can quickly pinpoint devices that have been impacted by the CVE-2022-42475 vulnerability using InvGate Asset Management. The following are the steps to take:
- Open InvGate Asset Management and go to the Explorer tab.
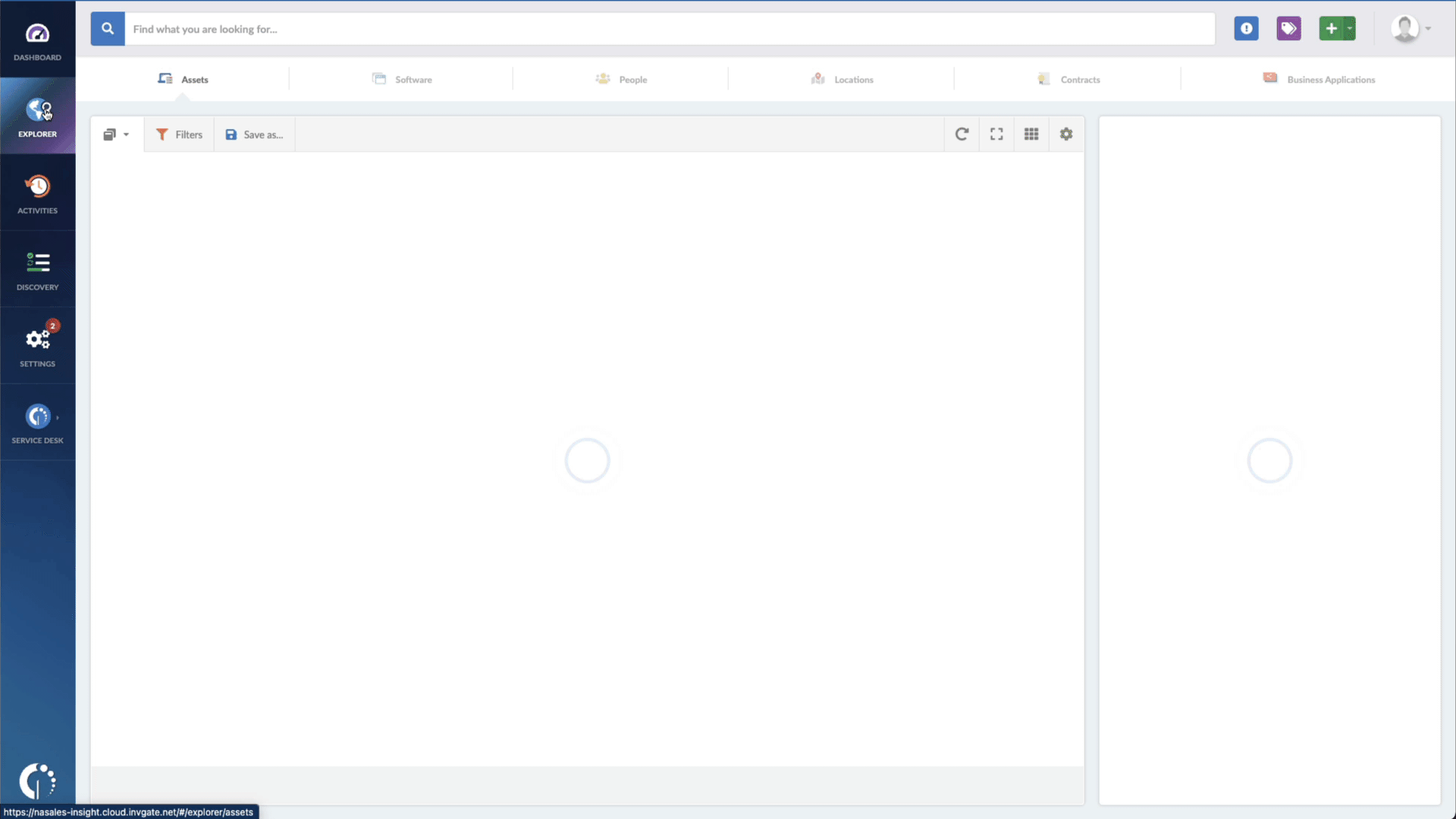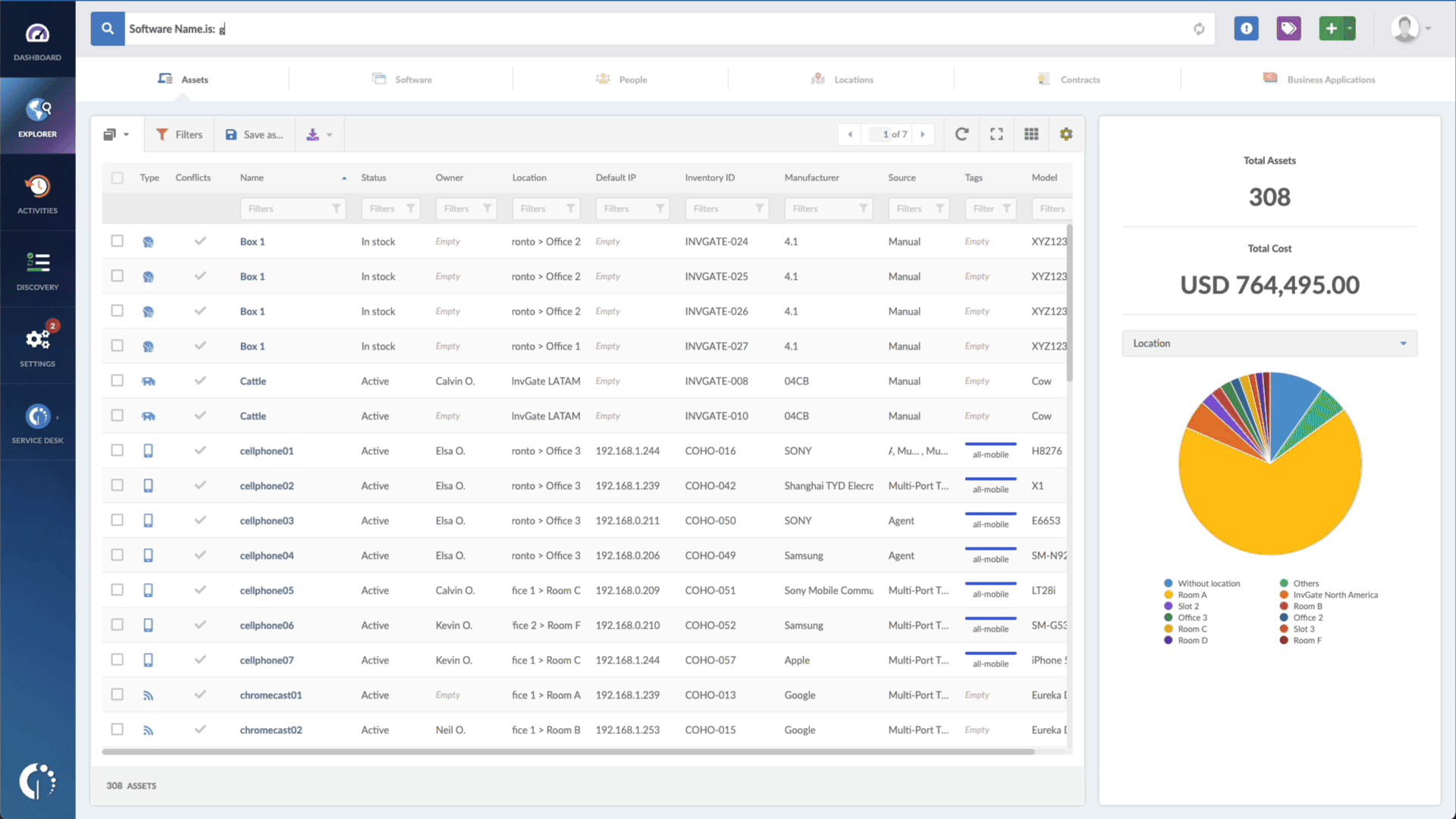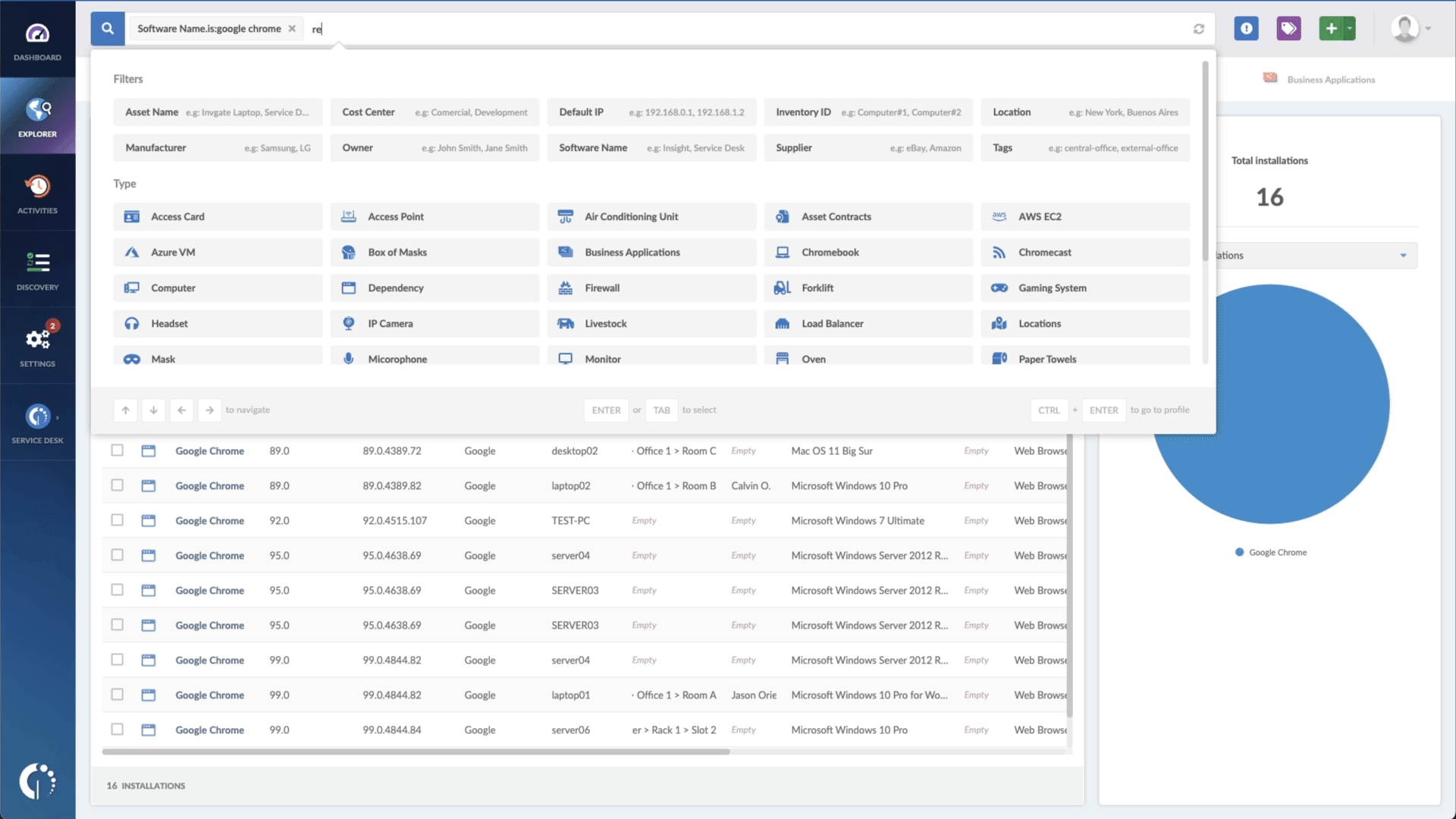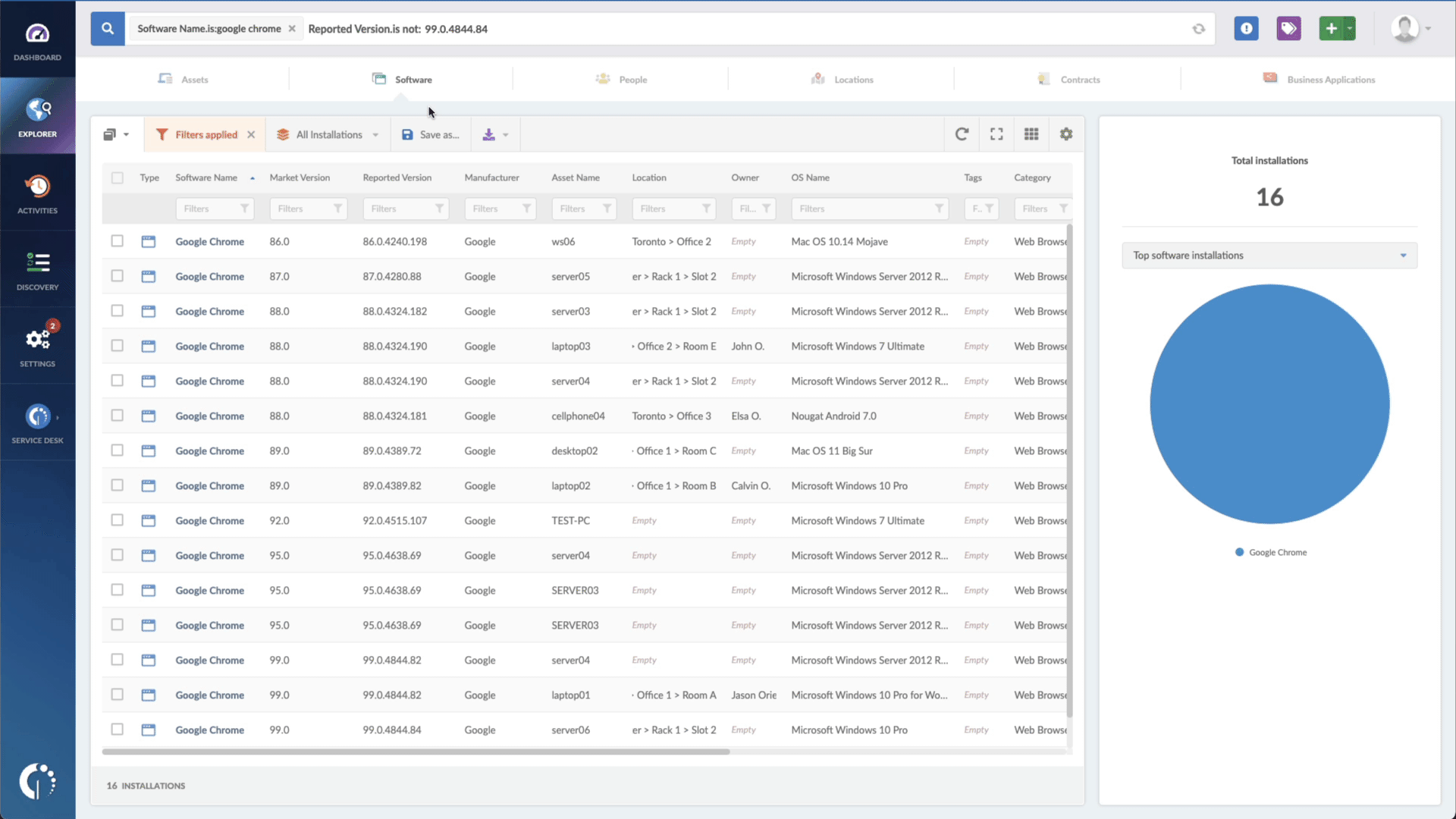
- Type in the Search bar “Software name, is:FortiOS” to filter all FortiOS devices.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Fortinet’s patched version.
According to Fortinet’s advisory, the affected versions of FortiOS and the relevant fixed versions are the following:
| Affected Version | Fixed Version |
| FortiOS version 7.2.0 through 7.2.2 | FortiOS version 7.2.3 or above |
| FortiOS version 7.0.0 through 7.0.8 | FortiOS version 7.0.9 or above |
| FortiOS version 6.4.0 through 6.4.10 | FortiOS version 6.4.11 or above |
| FortiOS version 6.2.0 through 6.2.11 | FortiOS version 6.2.12 or above |
| FortiOS version 6.0.0 through 6.0.15 | FortiOS version 6.0.16 or above |
| FortiOS version 5.6.0 through 5.6.14 | None listed |
| FortiOS version 5.4.0 through 5.4.13 | None listed |
| FortiOS version 5.2.0 through 5.2.15 | None listed |
| FortiOS version 5.0.0 through 5.0.14 | None listed |
| FortiOS-6K7K version 7.0.0 through 7.0.7 | FortiOS-6K7K version 7.0.8 or above |
| FortiOS-6K7K version 6.4.0 through 6.4.9 | FortiOS-6K7K version 6.4.10 or above |
| FortiOS-6K7K version 6.2.0 through 6.2.11 | FortiOS-6K7K version 6.2.12 or above |
| FortiOS-6K7K version 6.0.0 through 6.0.14 | FortiOS-6K7K version 6.0.15 or above |
| FortiProxy version 7.2.0 through 7.2.1 | FortiProxy version 7.2.2 or above |
| FortiProxy version 7.0.0 through 7.0.7 | FortiProxy version 7.0.8 or above |
| FortiProxy version 2.0.0 through 2.0.11 | FortiProxy version 2.0.12 or above |
| FortiProxy version 1.2.0 through 1.2.13 | FortiProxy version 2.0.12 or above |
| FortiProxy version 1.1.0 through 1.1.6 | FortiProxy version 2.0.12 or above |
| FortiProxy version 1.0.0 through 1.0.7 | FortiProxy version 2.0.12 or above |
The bottom line
The CVE-2022-42475 vulnerability poses a high risk to devices running certain versions of FortiOS. Attackers could exploit this vulnerability to gain unauthorized access to sensitive information, execute malicious code, or cause a denial-of-service condition. It is, therefore, crucial for organizations to apply the relevant patches promptly to mitigate the risk of a cyberattack.
InvGate Asset Management simplifies the patch management process by enabling organizations to identify vulnerable devices and manage the patch process effectively and swiftly.
To leverage the capabilities of InvGate Asset Management, request a 30-day free trial and search for vulnerable devices in your network! By using this solution, you can proactively manage your device inventory, reduce the risk of cyberattacks, and ensure business continuity. Sign up for the free trial to secure your systems from the CVE-2022-42475 vulnerability.