A critical security flaw was discovered in Git, the widely used version control system. This vulnerability, assigned the CVE-2022-41903 identifier, could enable attackers to execute malicious code on affected systems remotely. Given its severity, organizations must take immediate action to protect their systems by applying the necessary patch.
In this blog post, we’ll overview the CVE-2022-41903 vulnerability, including what it is, what it does, and how InvGate Asset Management can simplify Patch Management.
To ensure your organization is protected against vulnerabilities like CVE-2022-41903, read on and learn how to safeguard your systems!
About CVE-2022-41903
CVE-2022-41903 is a buffer overflow vulnerability in Git, a distributed revision control system.
The vulnerability exists in the `pretty.c::format_and_pad_commit()` function, which is responsible for formatting commit messages.
The vulnerability can be exploited by a remote attacker to execute arbitrary code on the victim's system by sending a specially crafted request to the Git server. The request will trigger the mentioned function, which will overflow the buffer and allow the attacker to execute arbitrary code.
If you do not patch CVE-2022-41903, you risk a remote attacker executing arbitrary code on your system, allowing it to steal your data, install malware, or take control of your system.
CVE-2022-41903 has been patched in the versions published on 2023-01-17, going back to v2.30.7. Users are advised to upgrade to the latest version of Git. For those who are unable to upgrade should disable `git archive` in untrusted repositories. If you expose `git archive` via `git daemon`, disable it by running `git config --global daemon. uploadArch false.`
How does CVE-2022-41903 work?
The vulnerability is triggered when a user runs a command that invokes the commit formatting machinery, such as `git log --format=...` It can also be triggered indirectly through `git archive` via the `export-subst` mechanism.
Is the vulnerability fixed?
Yes, Git has released patches for CVE-2022-41903. The affected versions of Git are 2.39 and older. The patched versions of Git are 2.40 and newer.
If you are using an affected version of Git, you should upgrade to the latest version as soon as possible.
How to find devices exposed to CVE-2022-41903
You can use InvGate Asset Management to find devices that are exposed to the CVE-2022-41903 vulnerability, follow these steps:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Git” to filter all the devices with Git.
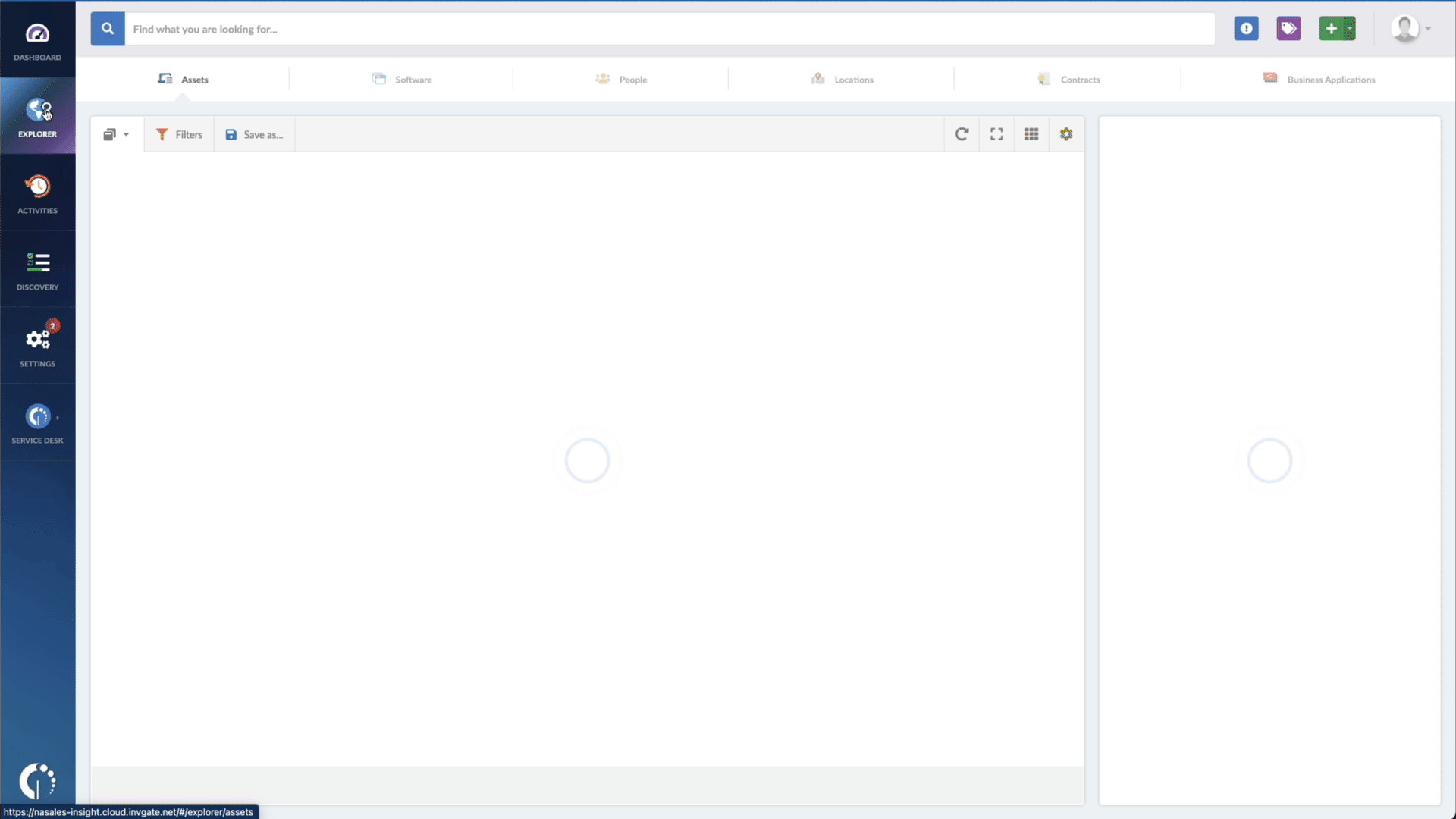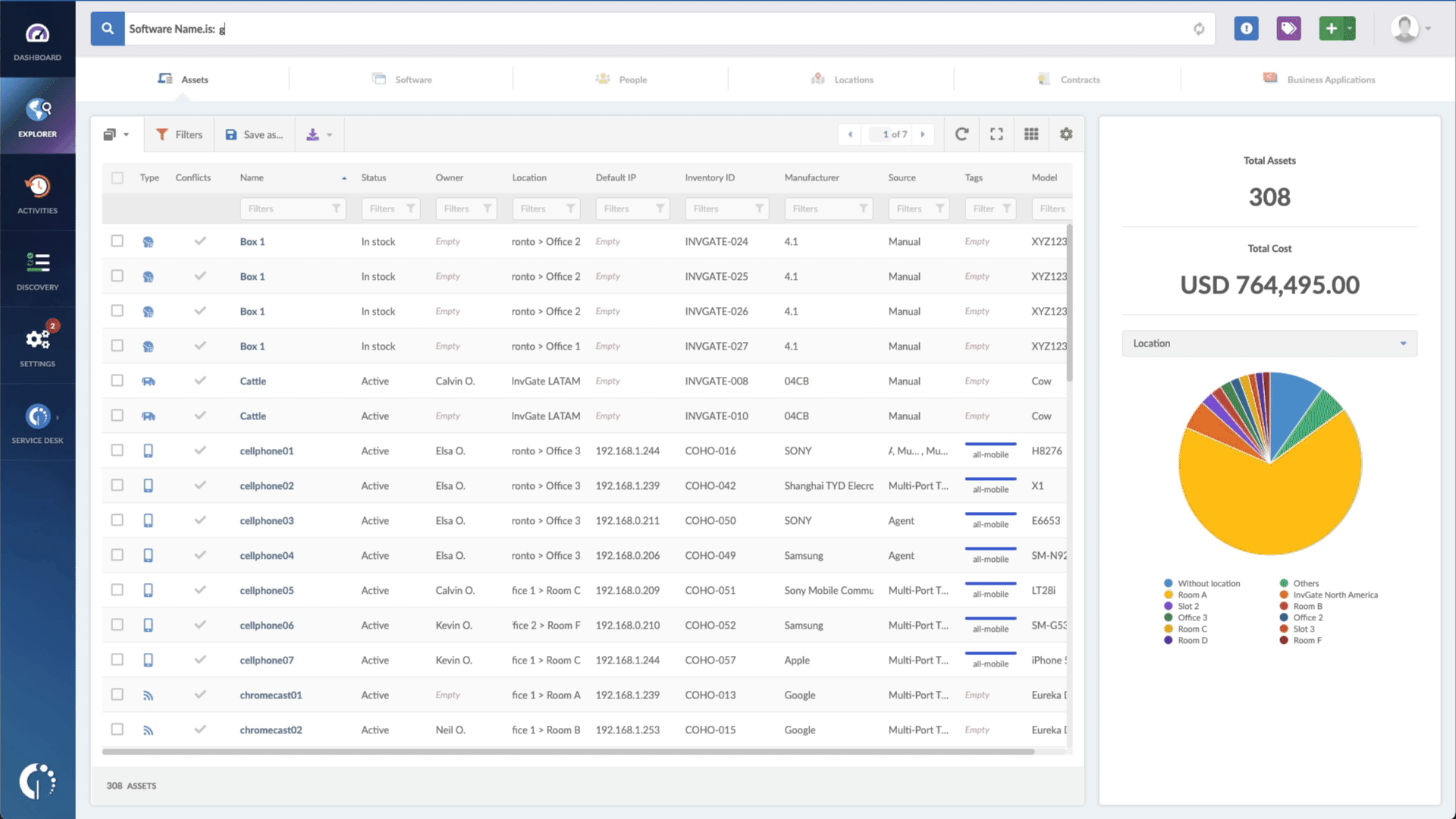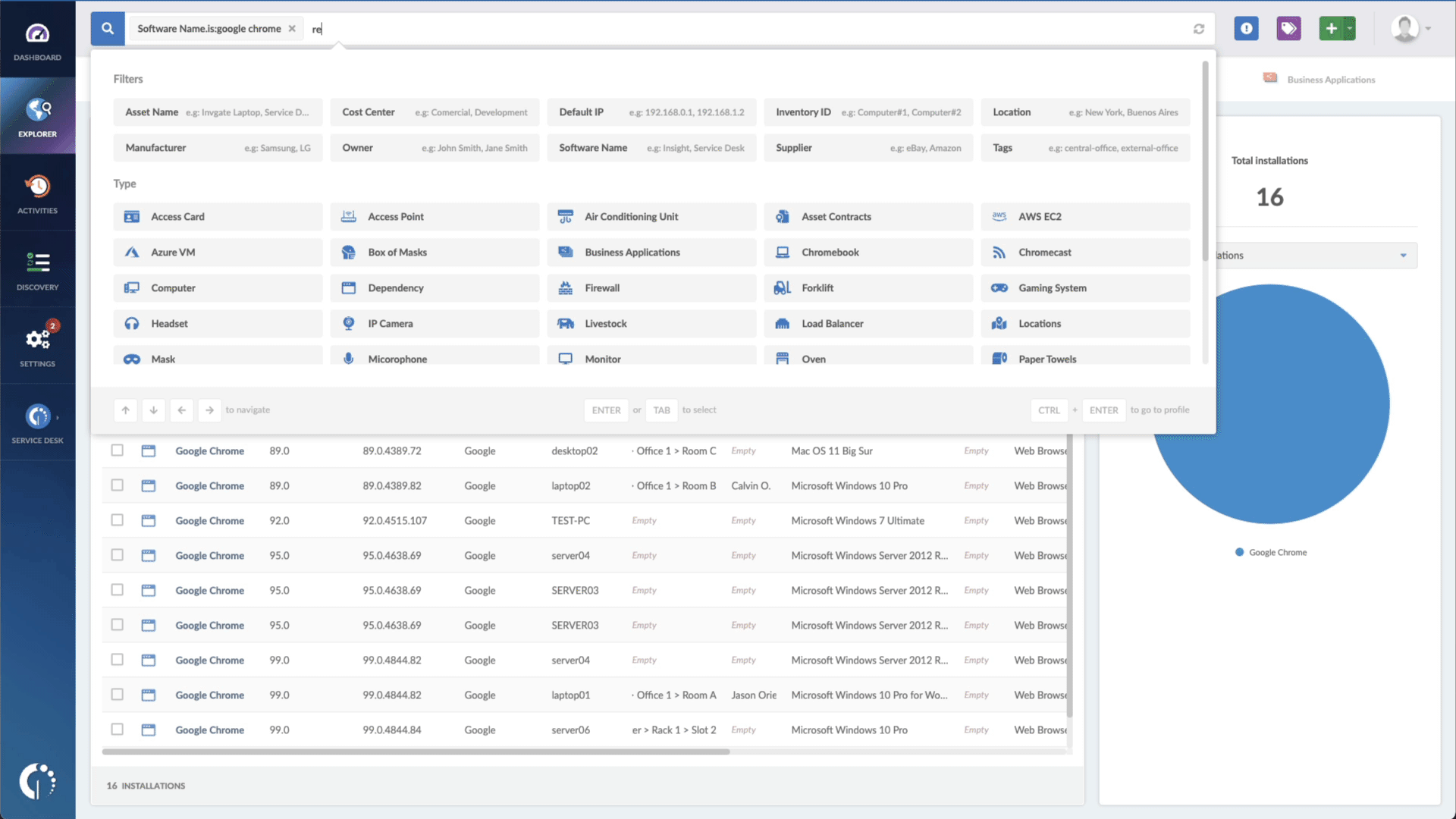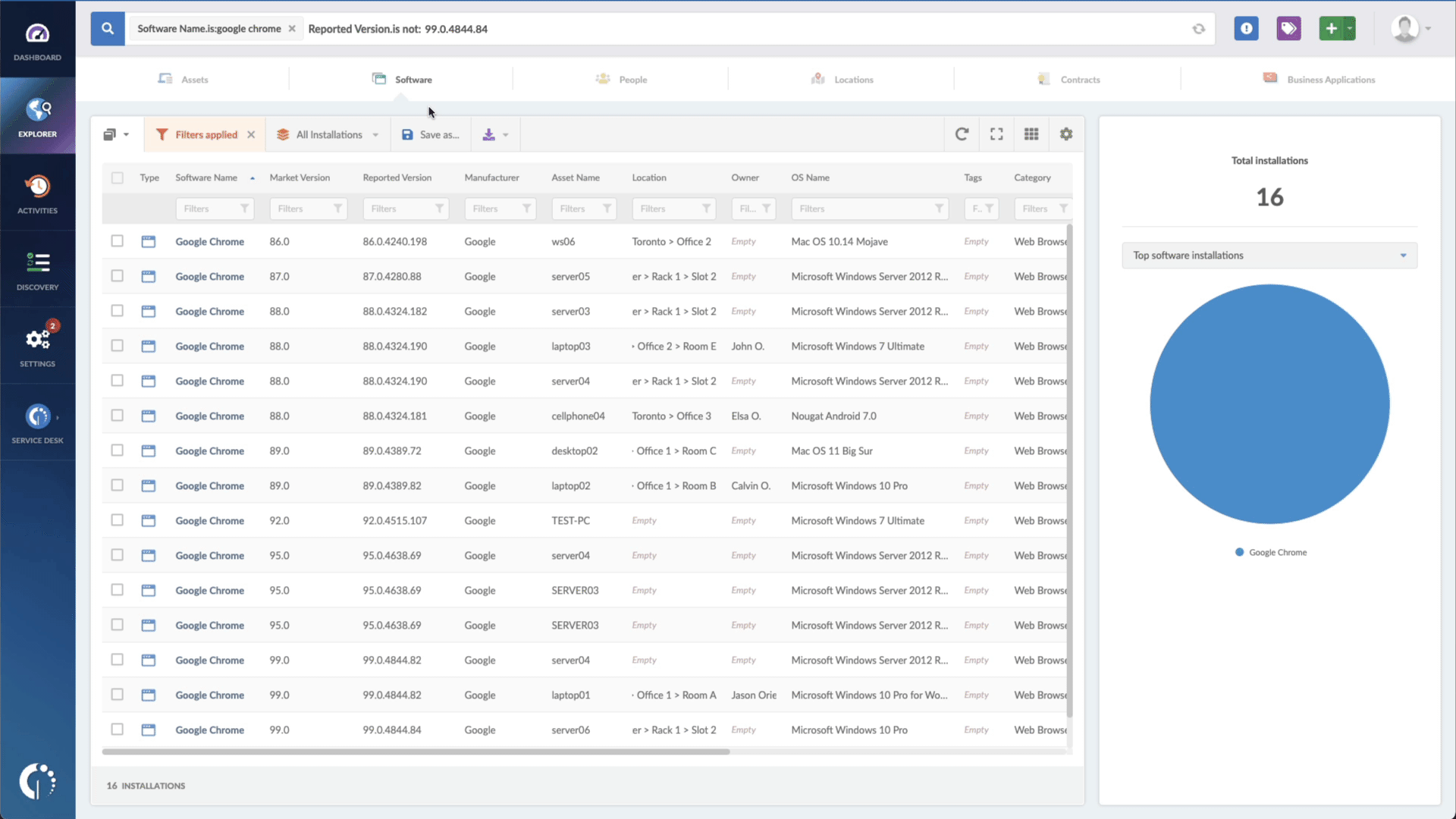
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Git’s patched version (2.40 and newer).
The bottom line
The Git Buffer Overflow Vulnerability (CVE-2022-41903) is a critical security flaw that could allow attackers to remotely execute code on affected systems, giving them complete control. The vulnerability was fixed in Git version 2.40, and it is crucial that users update their software to this version or later to protect themselves from it.
InvGate Asset Management can help simplify the process of updating software across an organization's network. With InvGate Asset Management, IT administrators can easily search for devices on their network that are running the affected version of Git and simplify Patch Management.
To see how InvGate Asset Management can help you protect against vulnerabilities like CVE-2022-41903, request a 30-day free trial today.