With cyber-attacks on the rise, it's more important than ever to be proactive in securing your devices against vulnerabilities. In August 2022, Apple announced a critical vulnerability affecting their operating systems, specifically iOS, iPadOS, and macOS, known as CVE-2022-32894.
This vulnerability allows attackers to execute arbitrary code with kernel privileges, potentially accessing sensitive information and compromising device security.
In this article, we'll provide an overview of CVE-2022-32894, including what it is, its associated risks, and how to identify and patch devices exposed to this vulnerability with the help of InvGate Asset Management.
If you're concerned about your device's security and want to learn more about CVE-2022-32894, keep reading! We'll provide all the information you need to safeguard your devices against potential attacks.
About CVE-2022-32894
CVE-2022-32894 is an out-of-bounds write vulnerability that affects Apple's operating systems, specifically iOS, iPadOS, and macOS. The vulnerability allows attackers to execute arbitrary code with kernel privileges, which means they can potentially take control of the entire system.
CVE-2022-32894 was addressed with improved bounds checking, and the issue is fixed in iOS 15.6.1, iPadOS 15.6.1, and macOS Monterey 12.5.1.
How to find devices exposed to CVE-2022-32894
InvGate Asset Management provides a rapid way to detect devices that have been impacted by the CVE-2022-32894 vulnerability. To utilize this feature, follow the instructions below:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:iOS” (or iPad, or macOS) to filter all Apple devices.
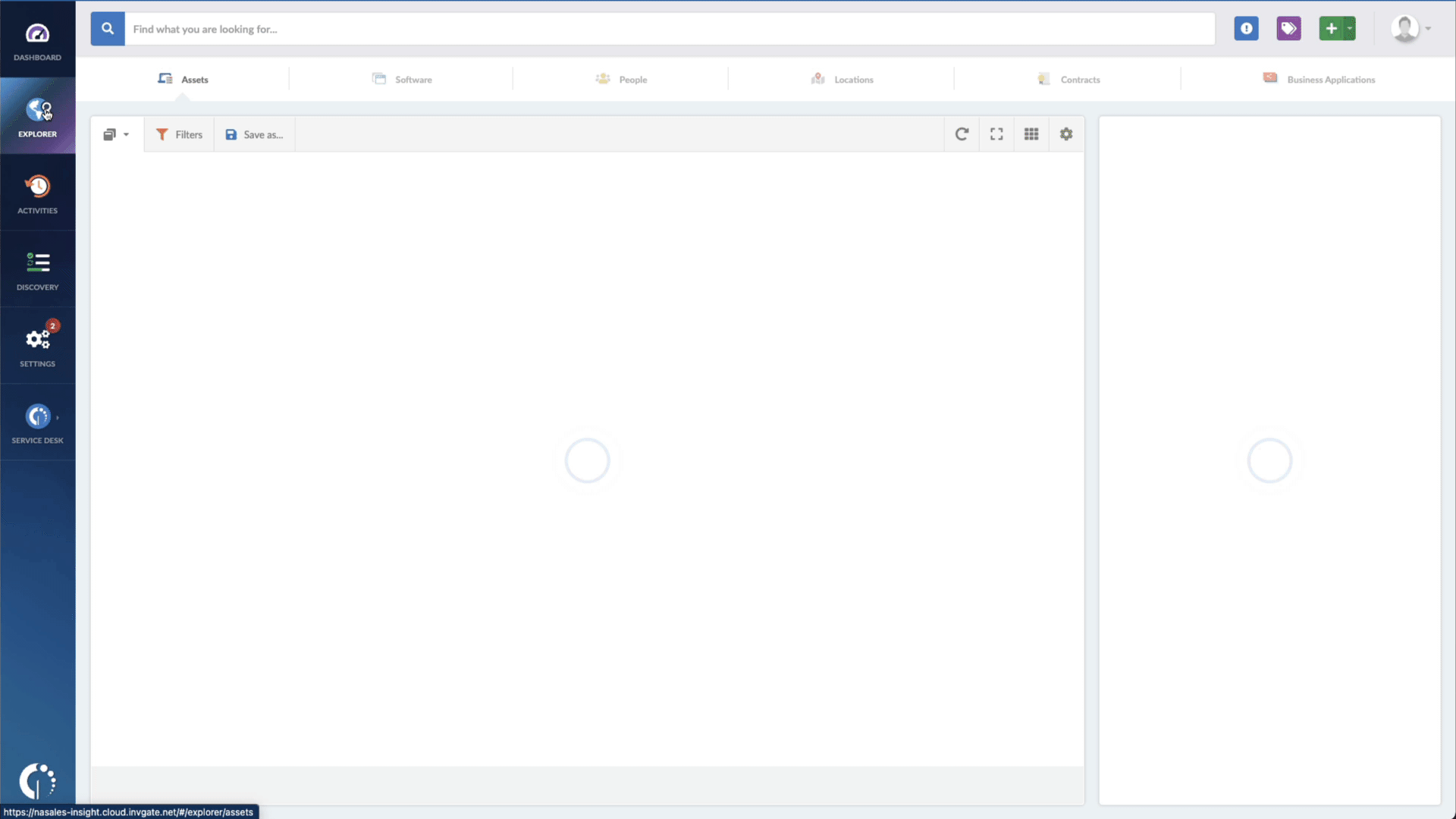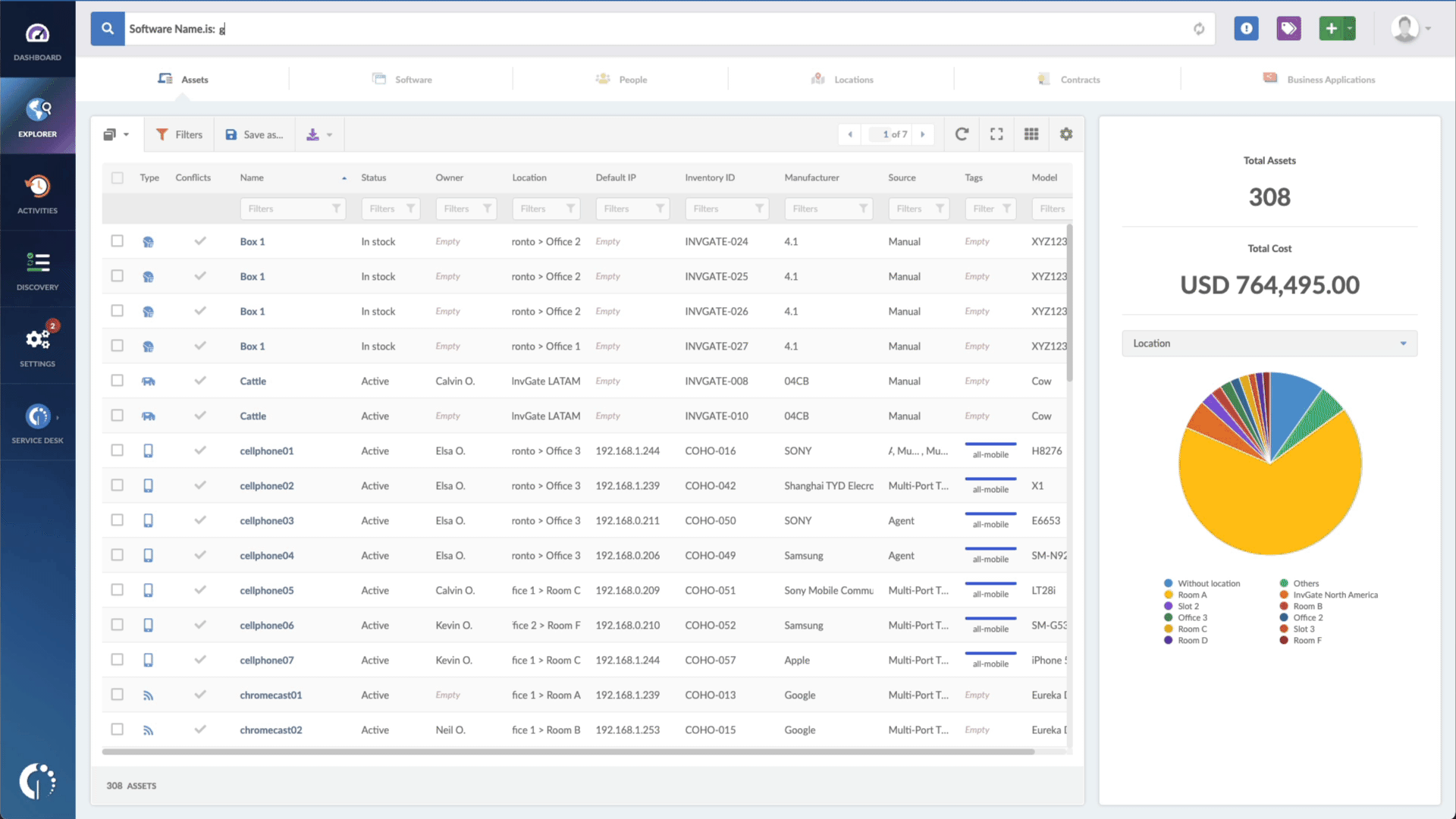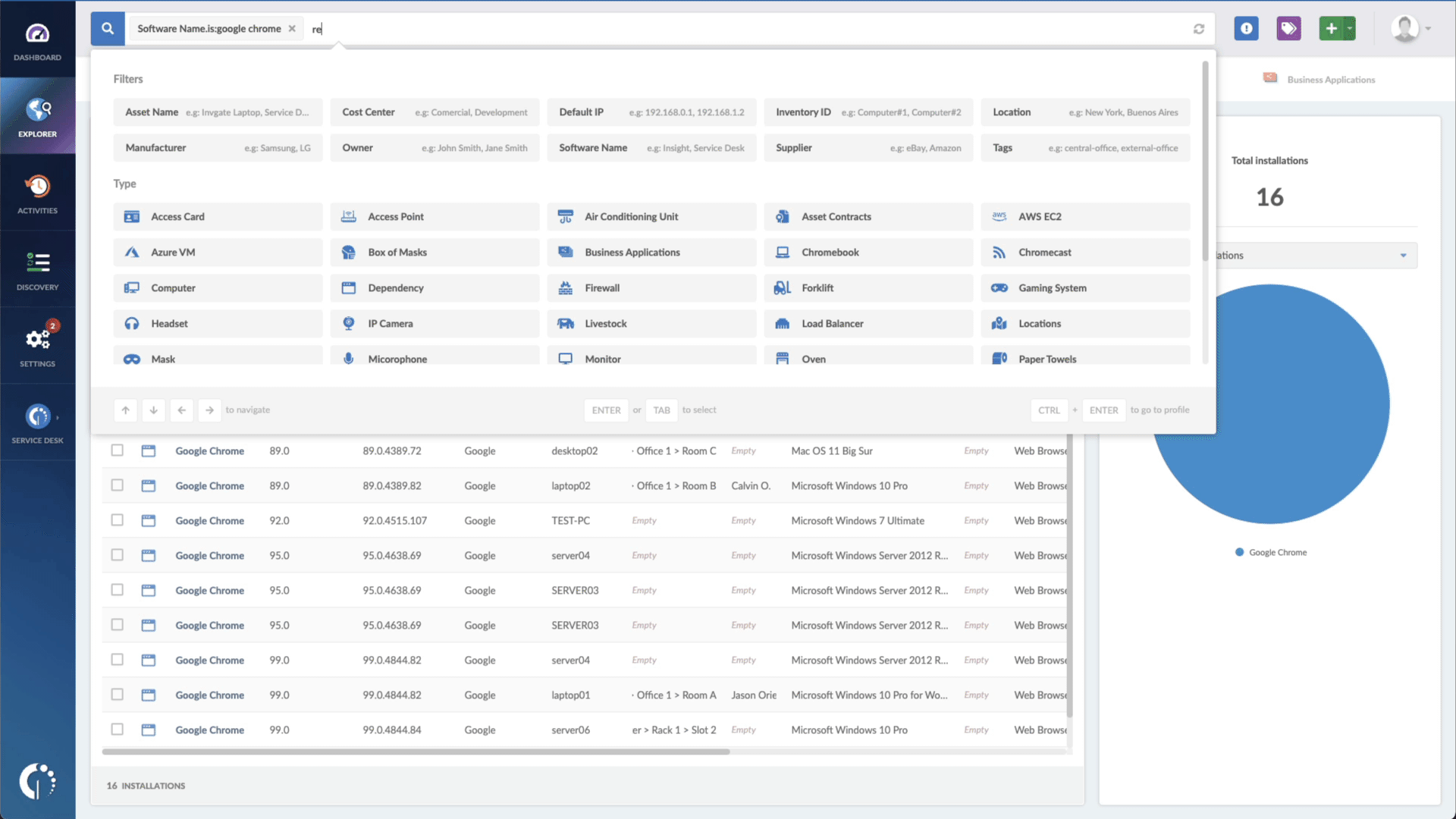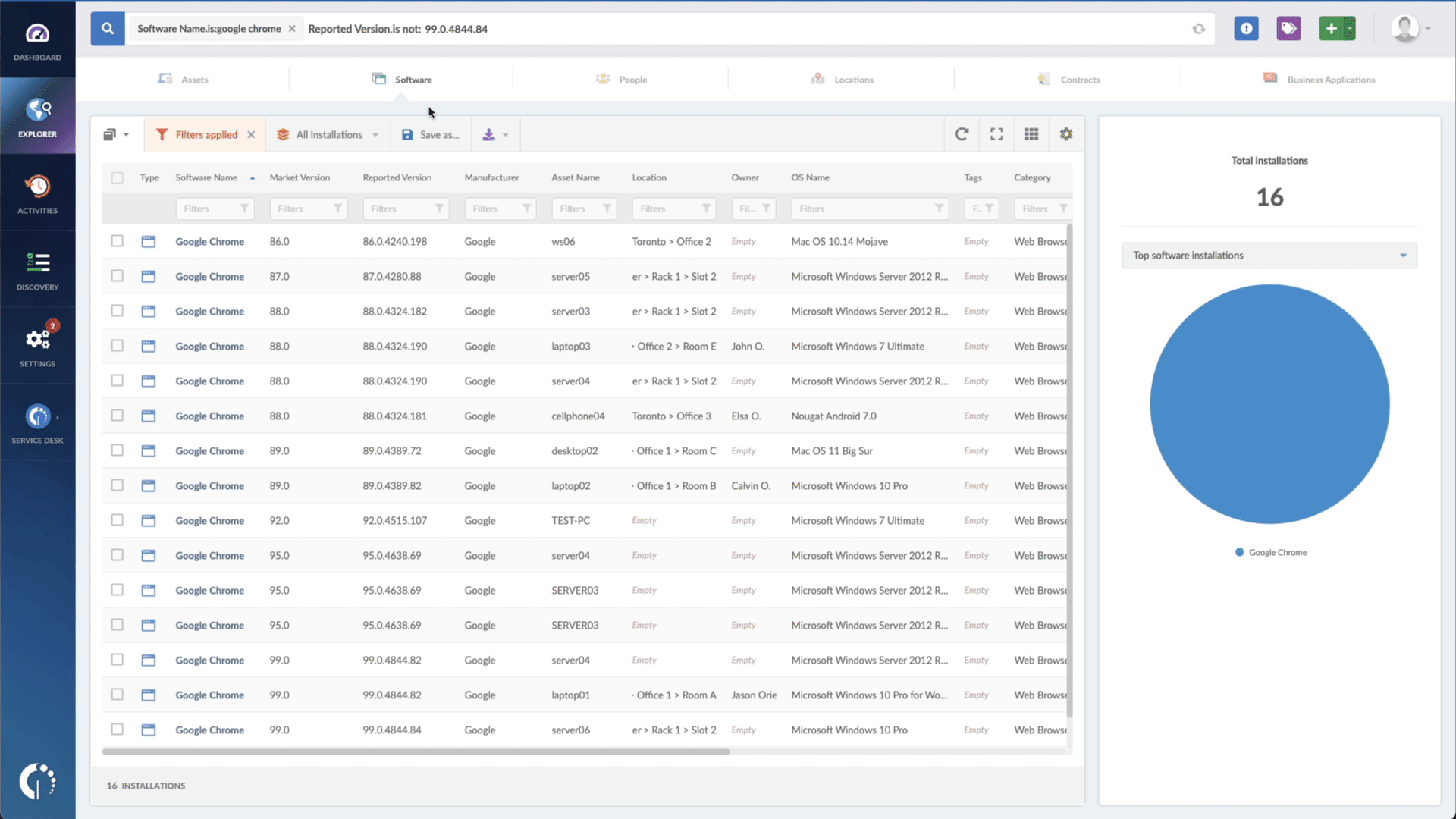
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Apple’s patched version (iOS 15.6.1, iPadOS 15.6, and macOS 12.5.1).
Other vulnerabilities
Aside from the CVE-2022-32894 vulnerability, there is another critical vulnerability that affects Apple's products, namely CVE-2022-32893. This vulnerability is an out-of-bounds write issue in WebKit, the browser engine that powers Safari and other iOS web browsers. Attackers can exploit this vulnerability by tricking users into visiting a website with maliciously crafted web content, allowing them to execute arbitrary code on the affected device.
The CVE-2022-32893 vulnerability is especially concerning because it can be exploited remotely without any user interaction.
Apple has acknowledged that this vulnerability may have been actively exploited by attackers, underscoring the critical need for users to patch their devices immediately. The latest versions that include the patch for CVE-2022-32893 are iOS 15.6.1, iPadOS 15.6.1, and macOS Monterey 12.5.1. Users who cannot update their devices should avoid visiting unfamiliar websites or clicking on links in suspicious emails to reduce their risk of falling prey to a potential attack.
The bottom line
The CVE-2022-32894 and CVE-2022-32893 vulnerabilities are critical security flaws that affect Apple's operating systems and browser engines. Attackers can exploit these vulnerabilities to remotely execute arbitrary code on affected devices, potentially accessing sensitive data, installing malware, and performing other malicious actions.
Apple has released security updates to address these vulnerabilities, and users should update their devices to the latest version of iOS, iPadOS, or macOS as soon as possible to protect themselves from potential attacks.
InvGate Asset Management offers an efficient solution for detecting devices impacted by these vulnerabilities. With InvGate Asset Management, users can easily identify devices that require patching, reducing the time and effort required for Patch Management. To take advantage of InvGate Asset Management's capabilities, request a 30-day free trial and search for the devices in your network. Don't wait for an attack to happen; take proactive steps to protect your devices and data today!