In today's digital age, cybersecurity threats are becoming increasingly sophisticated, leaving individuals and businesses vulnerable to attacks. On May 10th, 2022, Microsoft released a statement regarding a critical vulnerability, known as CVE-2022-26925, in the Windows Local Security Authority (LSA) subsystem.
This vulnerability poses a significant threat to system security, enabling attackers to bypass security measures and gain elevated privileges on the compromised system.
In this article, we'll provide an overview of CVE-2022-26925 and its associated risks. We'll also discuss how users can identify devices affected by the vulnerability with InvGate Asset Management and the importance of patching to ensure system security.
If you're concerned about your system's security and want to learn more about CVE-2022-26925, keep reading!
About CVE-2022-26925
CVE-2022-26925 is a security vulnerability in the Windows Local Security Authority (LSA) subsystem, which could allow attackers to bypass security measures and gain elevated privileges on a compromised system. The vulnerability has a CVSSv3 score of 5.9.
It was discovered in May 2022 and affects all Windows versions, including Windows 10 and Windows Server.
The vulnerability stems from how the Windows LSA subsystem handles application authentication requests. Specifically, the flaw exists in the way the LSA processes the authorization data in a Kerberos ticket. An attacker with network access to a target system could exploit the vulnerability by sending a specially crafted Kerberos ticket, which tricks the LSA into granting the attacker higher privileges than they are supposed to have.
An attacker who successfully exploits the vulnerability could potentially take control of the affected system, steal sensitive data, or execute malicious code.
The issue was addressed with the May 2022 Patch Tuesday updates. It is recommended that all users of Windows systems, including both home and enterprise environments, apply the patch as soon as possible to ensure they are protected against this critical security flaw.
How to find devices exposed to CVE-2022-26925
InvGate Asset Management enables you to promptly detect devices that the CVE-2022-26925 vulnerability has impacted. Below are the procedures you need to undertake:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Windows” to filter all Windows devices.
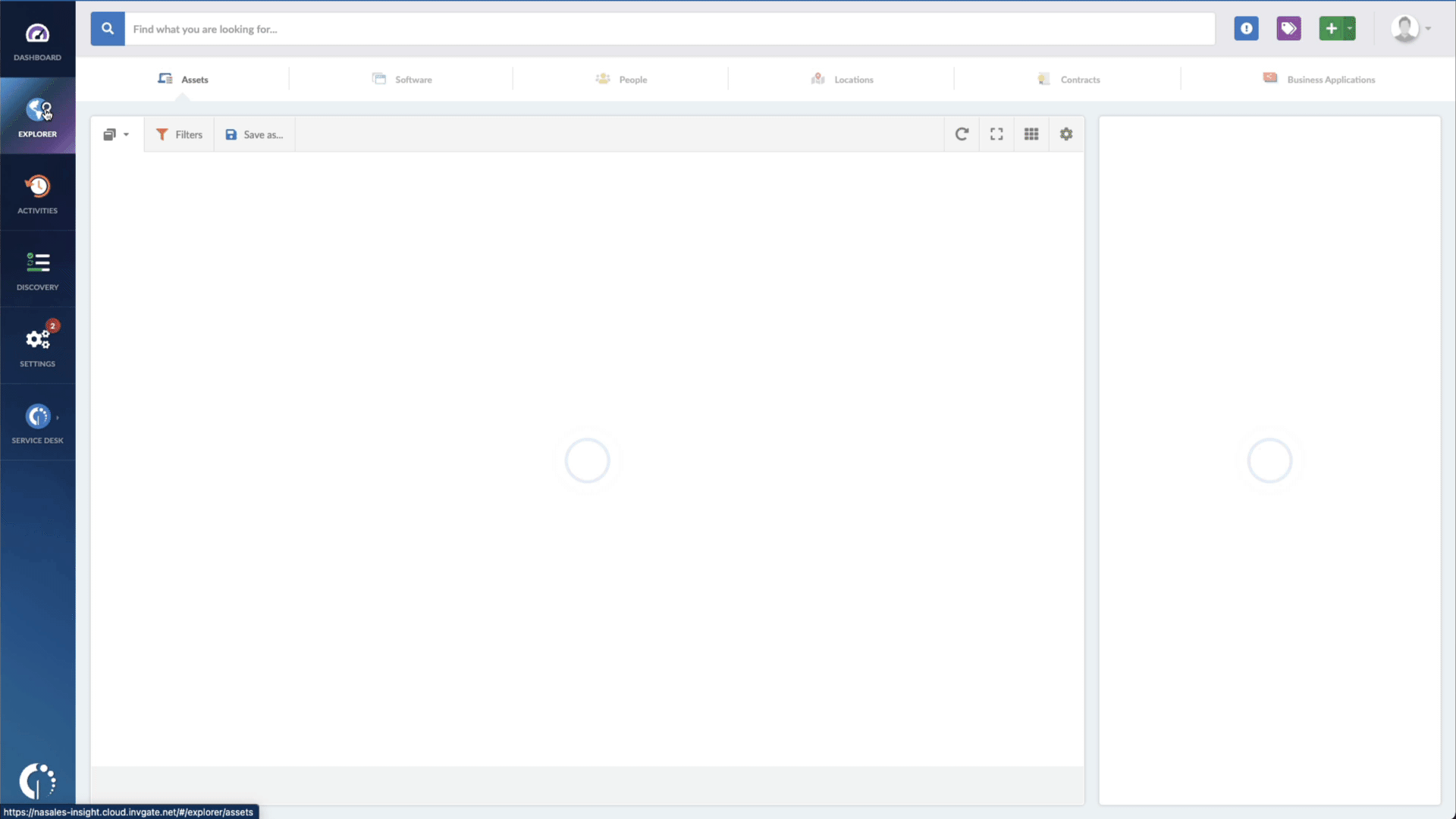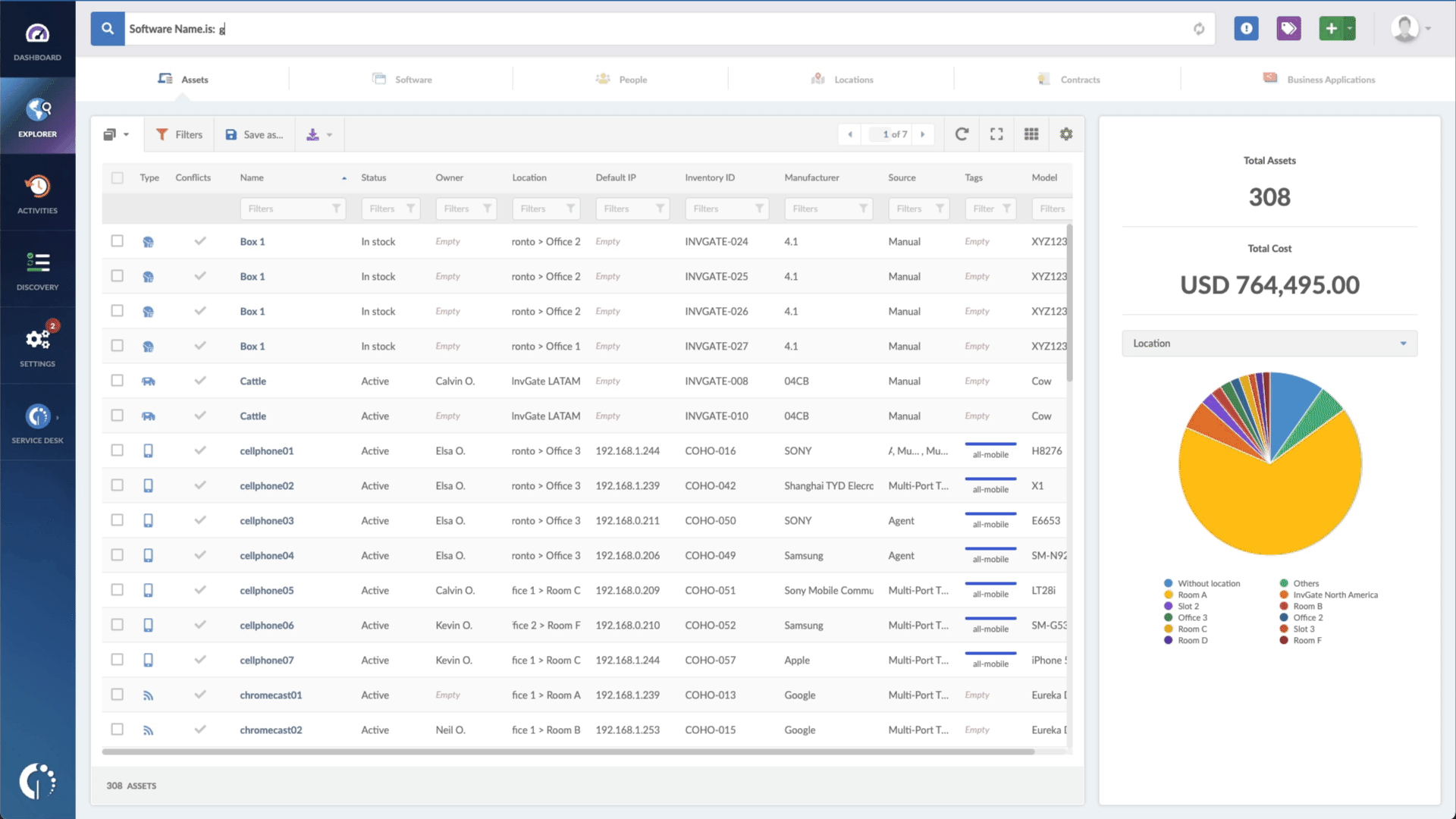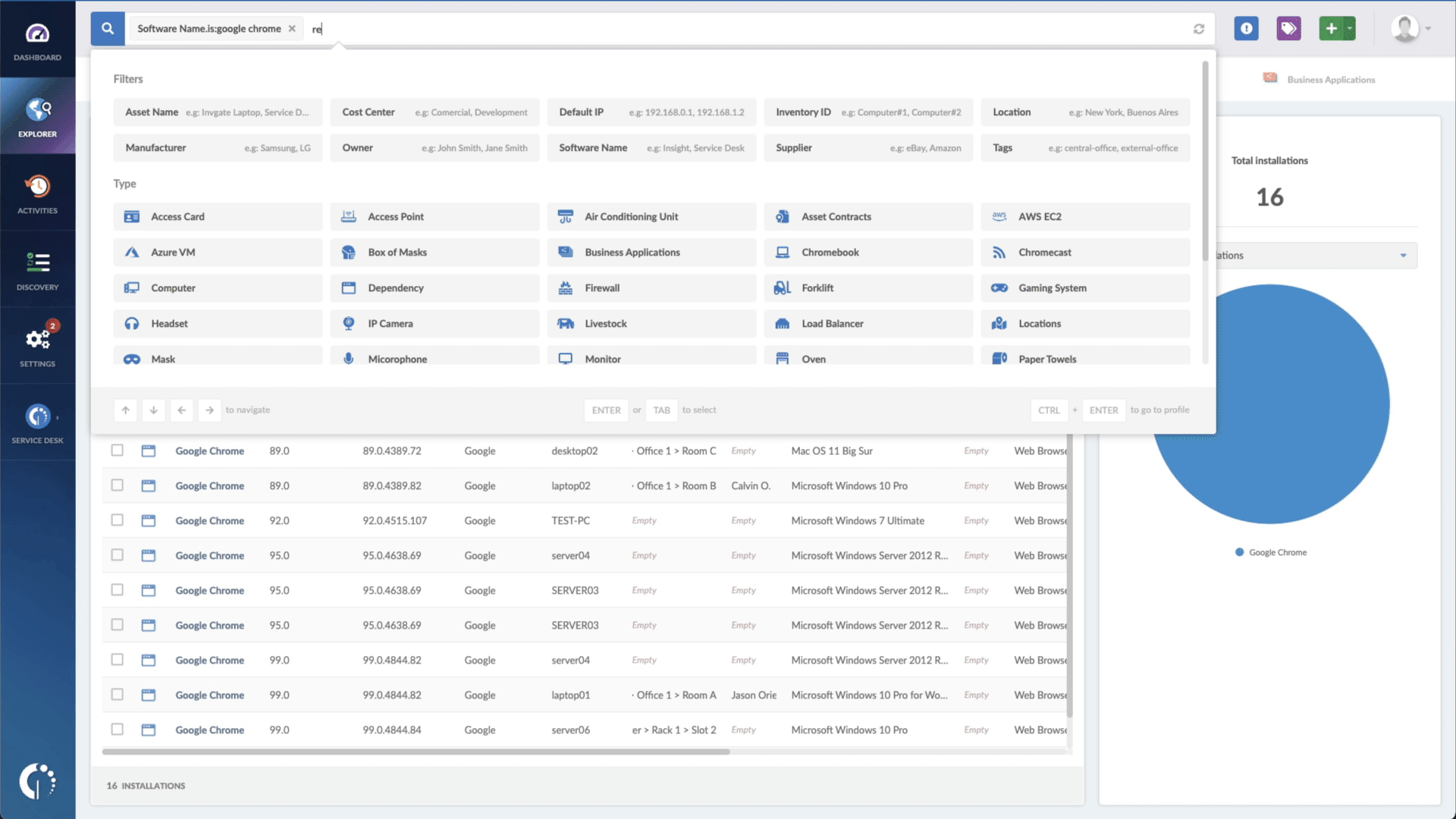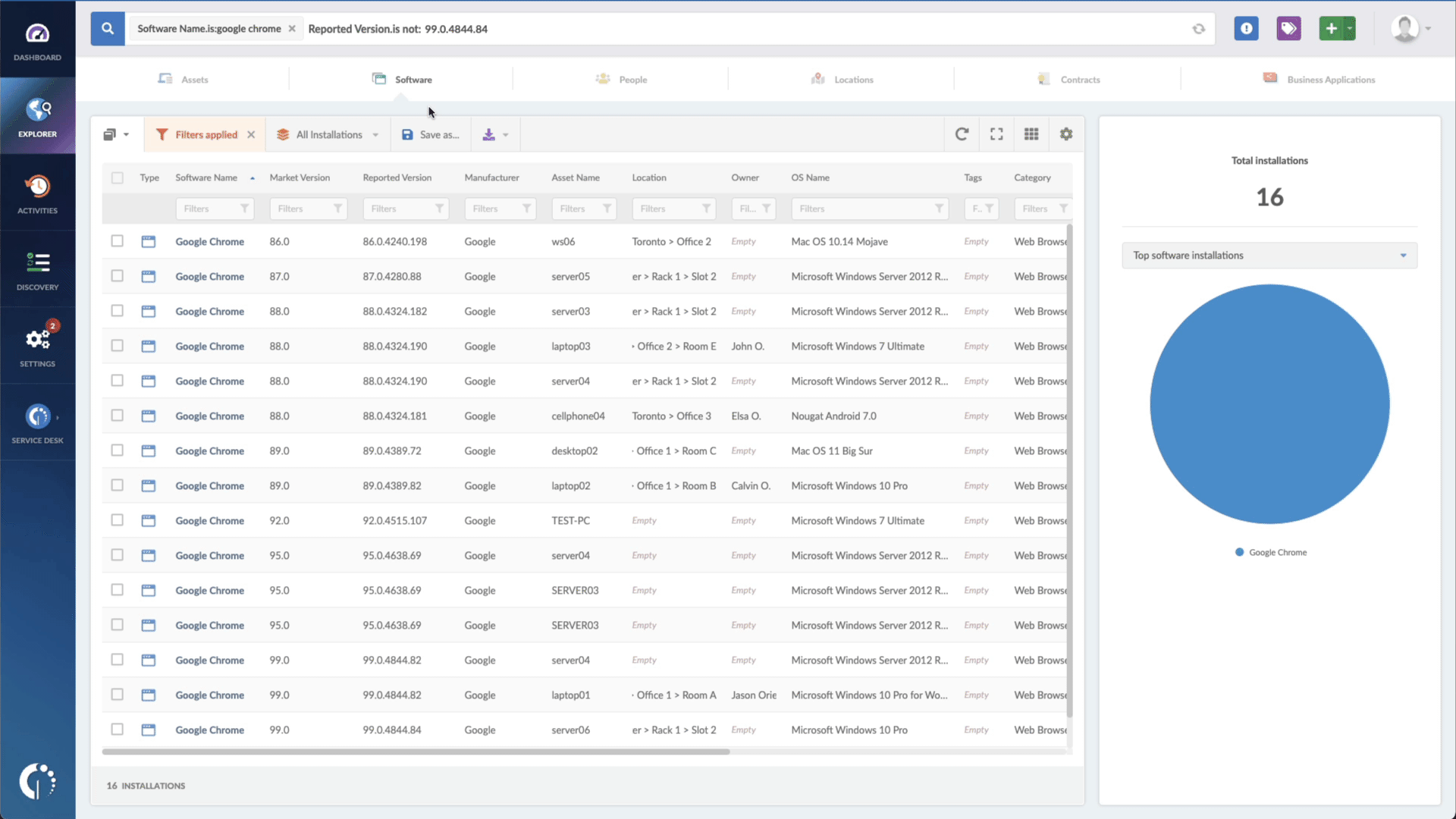
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your product, you’ll find the security update number on Microsoft’s webpage. For example, for Windows 10 for 32-bit Systems, it's KB5013963).
The bottom line
CVE-2022-26925 is a severe vulnerability that affects the Windows Local Security Authority subsystem, which could allow attackers to gain elevated privileges on compromised systems. The risk of this vulnerability is high, as it could result in attackers taking over a system, stealing sensitive data, or executing malicious code. It is crucial to apply the patch released by Microsoft as soon as possible to mitigate this vulnerability.
InvGate Asset Management simplifies patch management by enabling IT teams to identify devices impacted by the CVE-2022-26925 vulnerability quickly. With its advanced scanning capabilities, InvGate Asset Management makes it easy to locate vulnerable devices and take necessary actions to apply the patch. This saves time and resources and reduces the risk of the vulnerability being exploited.
To learn more about InvGate Asset Management and how it can help you streamline your patch management process, request a 30-day free trial and search for vulnerable devices in your network today!