Cybersecurity threats are becoming increasingly frequent and sophisticated, and keeping systems up-to-date is crucial to staying protected. On July 12th, 2022, Microsoft issued a statement about a critical vulnerability in the Client Server Run-time Subsystem (CSRSS), known as CVE-2022-22047.
This vulnerability can allow attackers to gain unauthorized access to sensitive data, making it a significant threat to users' cybersecurity. In this article, we'll provide an overview of CVE-2022-22047, including how to identify potentially vulnerable devices with InvGate Asset Management and patch them. Read on to learn more and protect your systems from this critical vulnerability!
About CVE-2022-22047
CVE-2022-22047 is an elevation of privilege (EoP) vulnerability that affects the Windows Client Server Run-time Subsystem (CSRSS) component of the Windows operating system. CSRSS is a core component of Windows that manages graphical user interface (GUI) operations and console functions.
The vulnerability has a CVSSv3 score of 7.8 and is rated as Important. It allows attackers to elevate their privileges on the affected system and execute arbitrary code with SYSTEM privileges. In other words, the attacker gains complete control of the compromised system, allowing them to steal sensitive data, install malware, or even disrupt the system's normal functioning.
The vulnerability affects all versions of Windows, and the risk is especially high for systems running older versions of the operating system that Microsoft no longer supports.
Microsoft has released a security update to fix this vulnerability, and it is crucial that all affected systems are updated as soon as possible to protect against it.
How to find devices exposed to CVE-2022-22047
InvGate Asset Management provides a quick and efficient way to detect devices that the CVE-2022-22047 vulnerability may impact. To identify potentially vulnerable devices, follow these steps:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Windows” to filter all Windows devices.
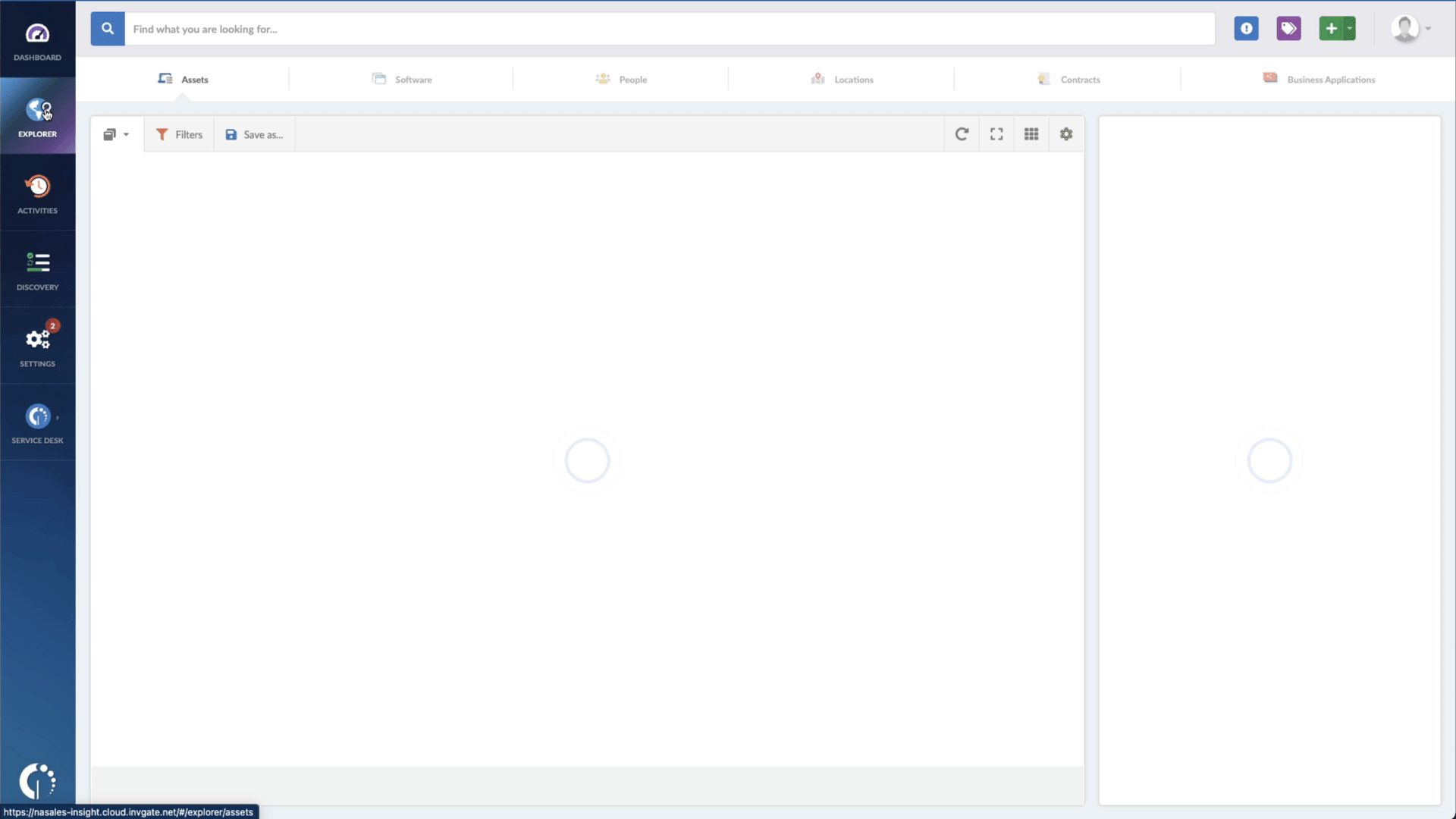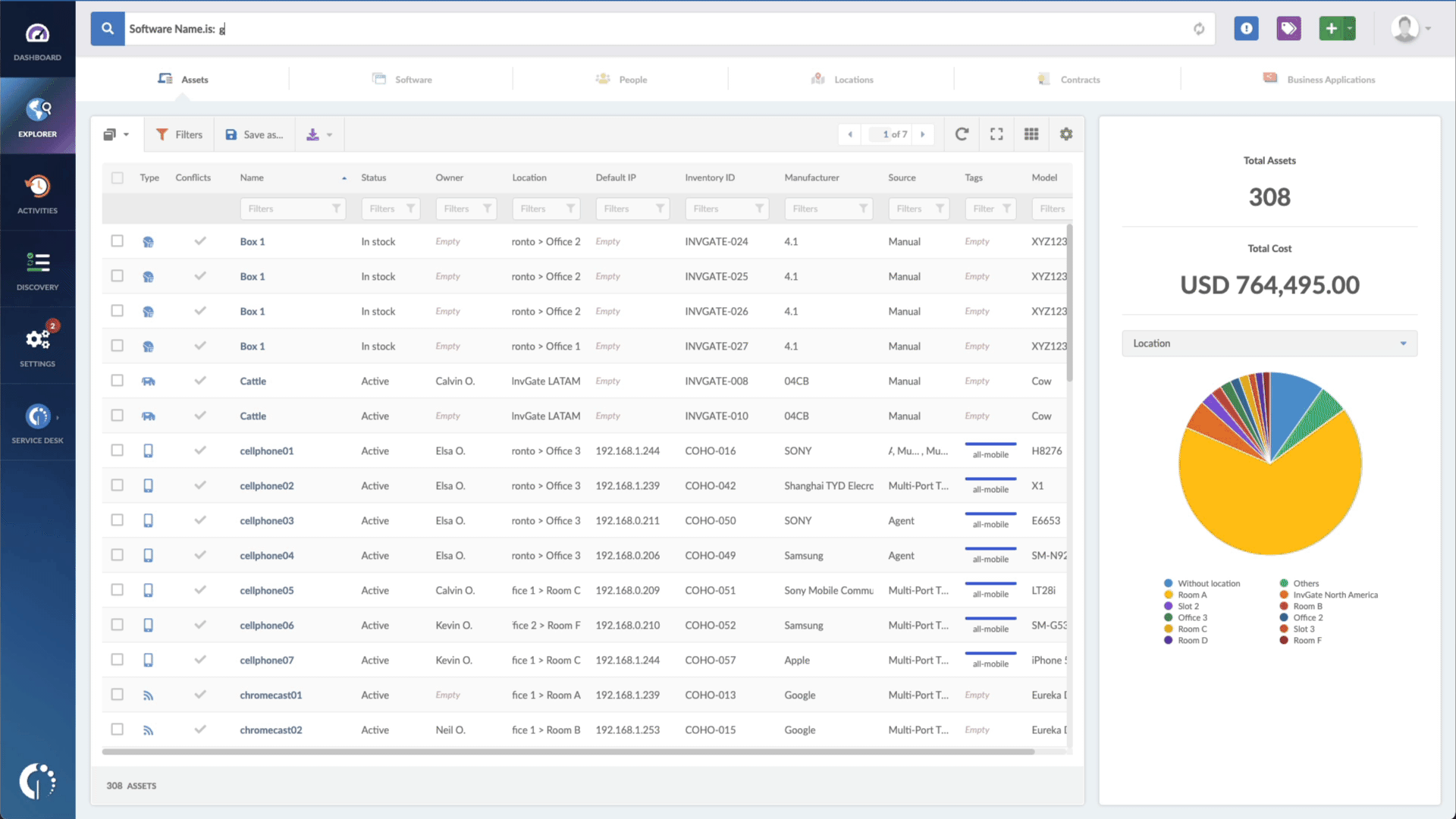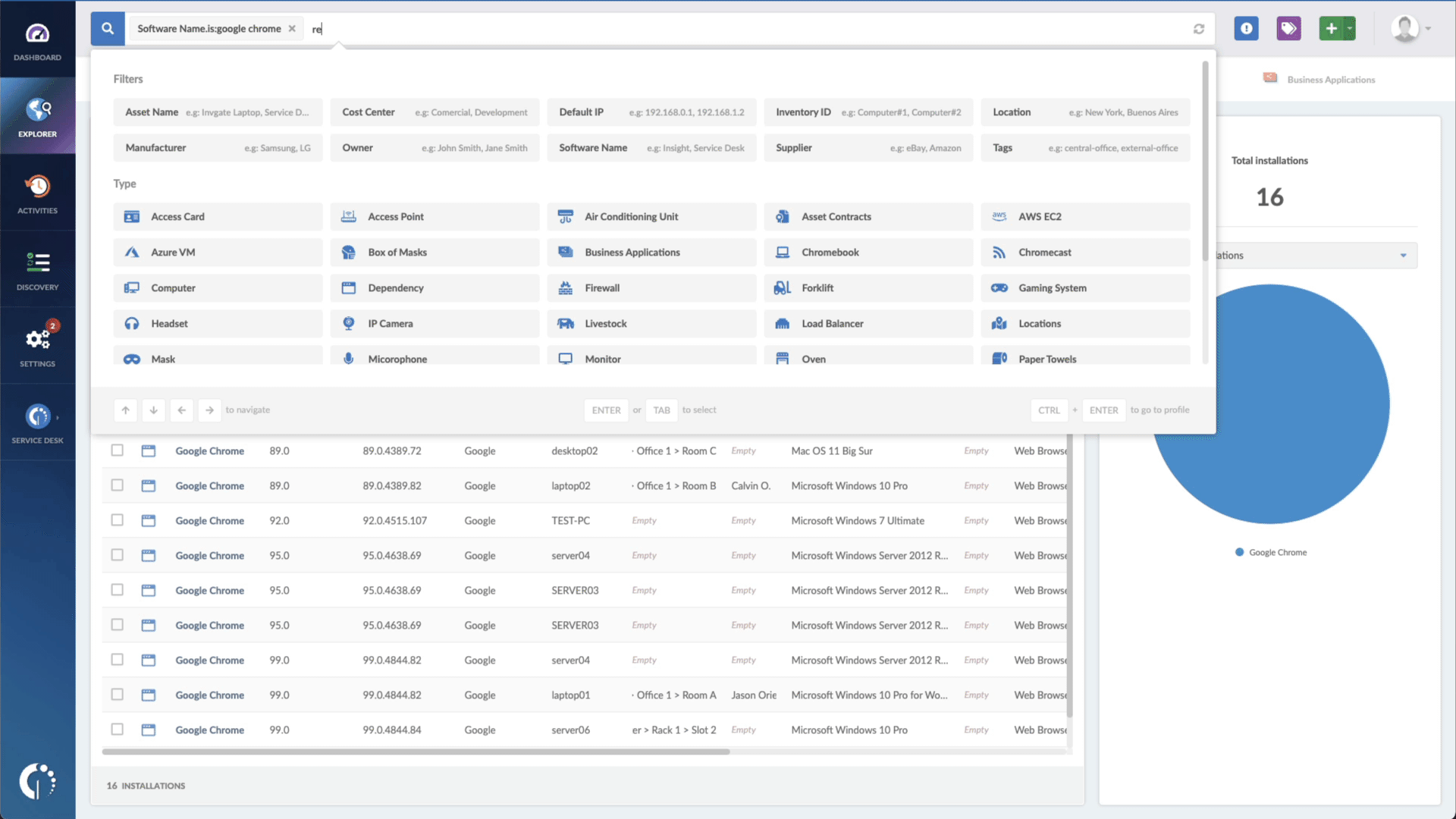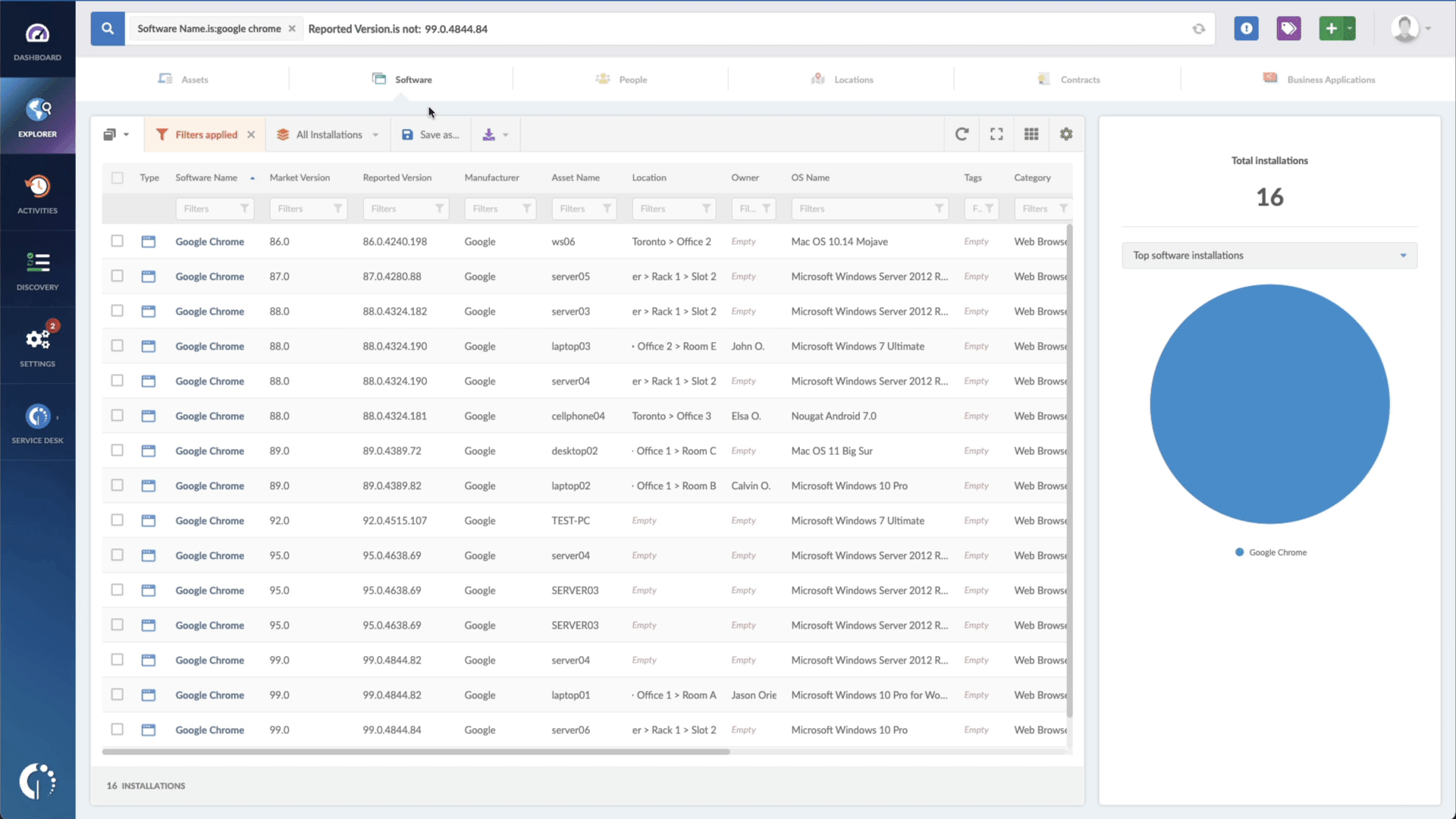
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your operating system, you’ll find the security update number on Microsoft’s webpage).
Other vulnerabilities
Apart from CVE-2022-22047, there are two other critical vulnerabilities that Windows users should be aware of:
Windows Server Service Tampering Vulnerability (CVE-2022-30216)
The CVE-2022-30216 vulnerability is caused by the Windows Server service's inability to properly handle user input, which can allow attackers to tamper with the service and execute arbitrary code.
It exists in newly implemented Server Services (srvsvc) released in the latest versions of Windows. Microsoft has already released a security update to fix this vulnerability, and users are strongly advised to apply the patch as soon as possible.
Windows Network File System Remote Code Execution Vulnerability (CVE-2022-22029)
The CVE-2022-22029 vulnerability is caused by the Windows Network File System (NFS) failing to properly handle certain requests, which can allow attackers to execute remote code on the affected system.
The affected software includes Windows Server 2008, 2012, 2016, 2019, and 2022. It is highly recommended that users apply the security update released by Microsoft to address this vulnerability without any delay.
The bottom line
In summary, CVE-2022-22047 is a critical vulnerability that can allow attackers to gain complete control of a system and compromise sensitive information. It affects all versions of Windows, but Microsoft has released a security update to fix the issue.
InvGate Asset Management can simplify patch management by identifying devices affected by this vulnerability. Don't wait for a security breach to happen! Request your 30-day free trial of InvGate Asset Management and scan your network to ensure all systems are up-to-date and secure.