A critical vulnerability by the name of CVE-2021-43890 has emerged, posing a significant threat to Windows 10 systems. This security flaw in the Windows AppX Installer can lead to potential data breaches or take control of your system.
In this blog post, we’ll provide a comprehensive overview of CVE-2021-43890, its potential risks, the available fix, and how InvGate Asset Management simplifies the process of identifying vulnerable devices and Patch Management.
Don't miss out on this critical information! Continue reading to stay informed about CVE-2021-43890 and take proactive measures to protect your systems and sensitive data.
About CVE-2021-43890
CVE-2021-43890 is a spoofing vulnerability in the Windows AppX Installer, which is used to install AppX apps on Windows 10 systems. This vulnerability allows an attacker to trick a user into installing a malicious AppX app that appears to be from a trusted source.
CVE-2021-43890 has been exploited in the wild by the Emotet/TrickBot/Bazaloader family of malware.
How does CVE-2021-43890 work?
The vulnerability is caused by a failure in the Windows AppX Installer to validate the authenticity of AppX packages properly. This allows an attacker to create a malicious AppX package that appears to be from a trusted source, such as Microsoft. When the user installs the malicious AppX package, it will execute the attacker's code.
What are CVE-2021-43890 risks?
An attacker could trick you into installing a malicious AppX app that appears to be from a trusted source. This malicious app could then execute the attacker's code on your system, allowing them to steal your personal information, such as your passwords, credit card numbers, and other sensitive data. It could also damage or take control of your system.
Is CVE-2021-43890 fixed?
Yes, Microsoft has released a patch for CVE-2021-43890. To install it, users should install the latest security updates for Windows 10.
How to find devices exposed to CVE-2021-43890
With InvGate Asset Management, you can quickly detect devices that are impacted by the CVE-2021-43890 vulnerability. Follow these instructions to proceed with the identification process efficiently:
- Open InvGate Asset Management and go to the Explorer tab.
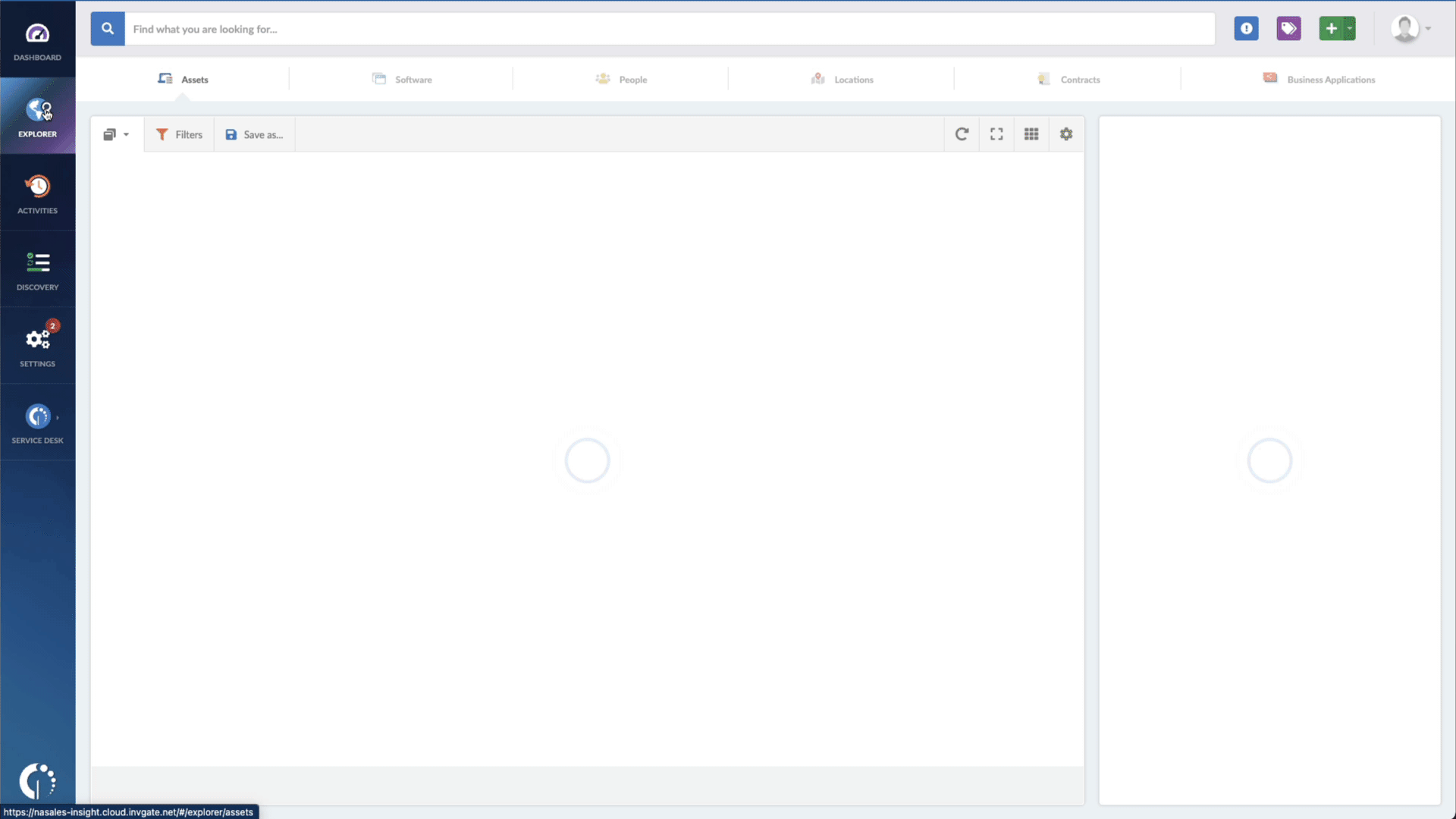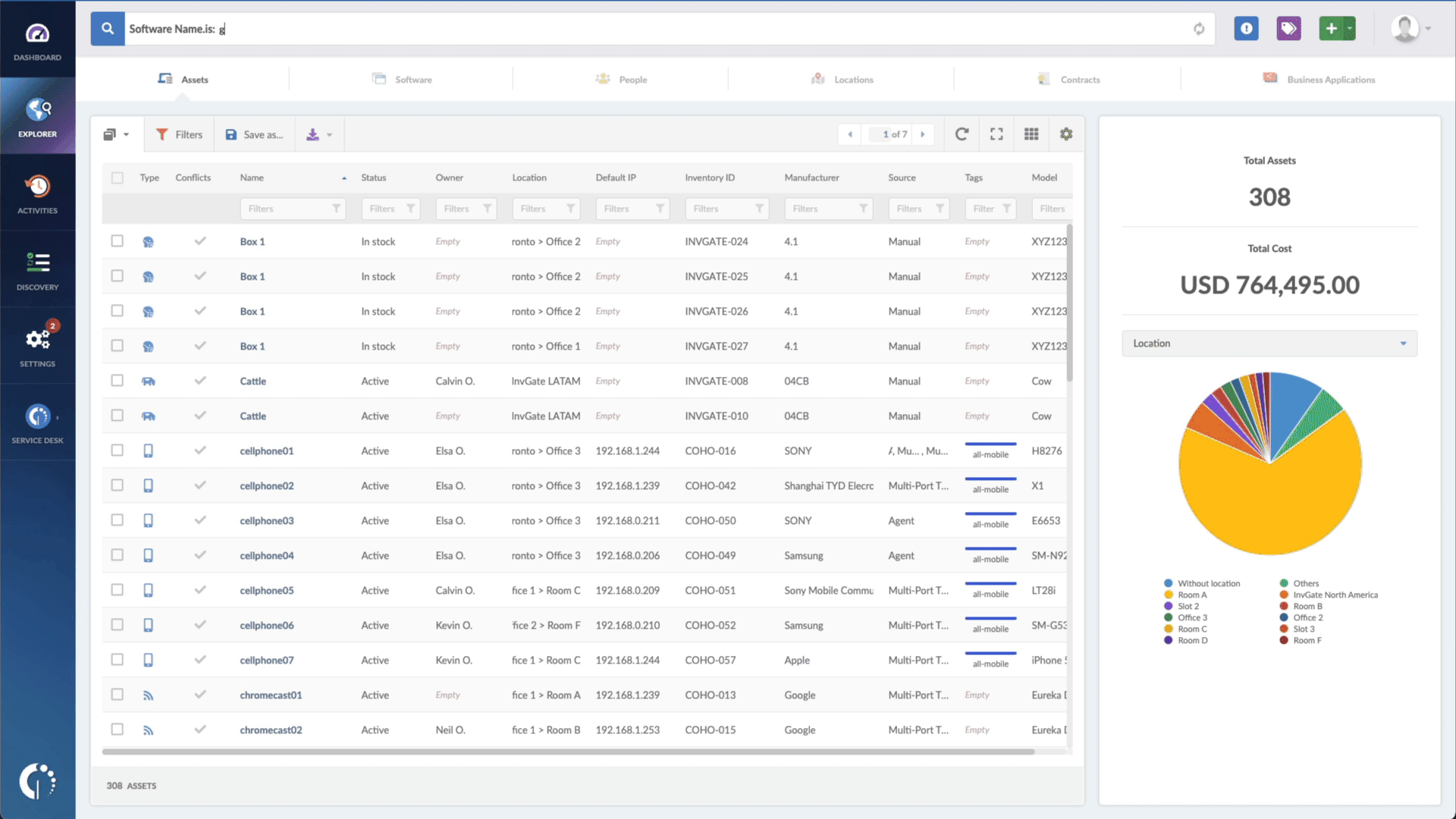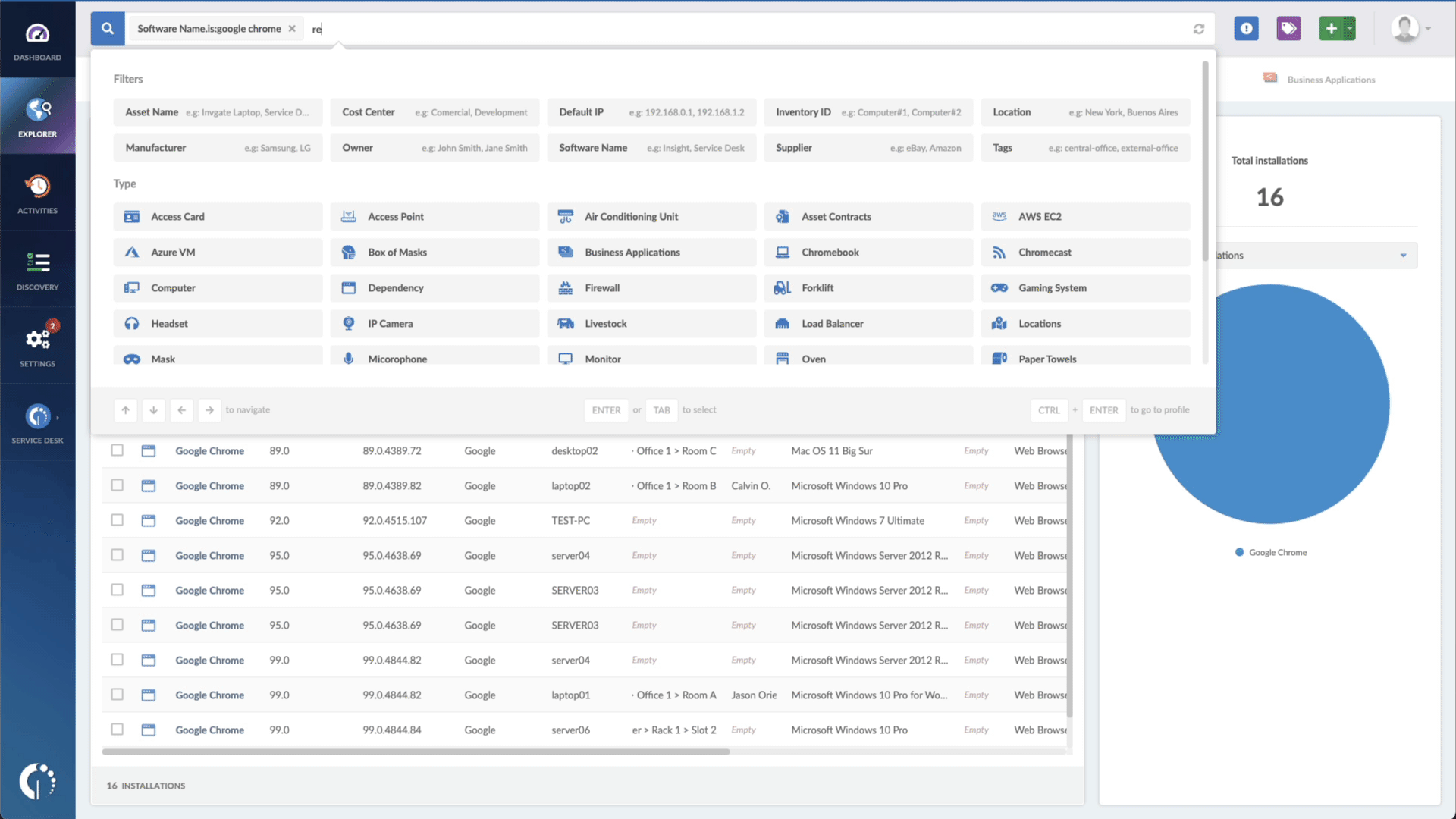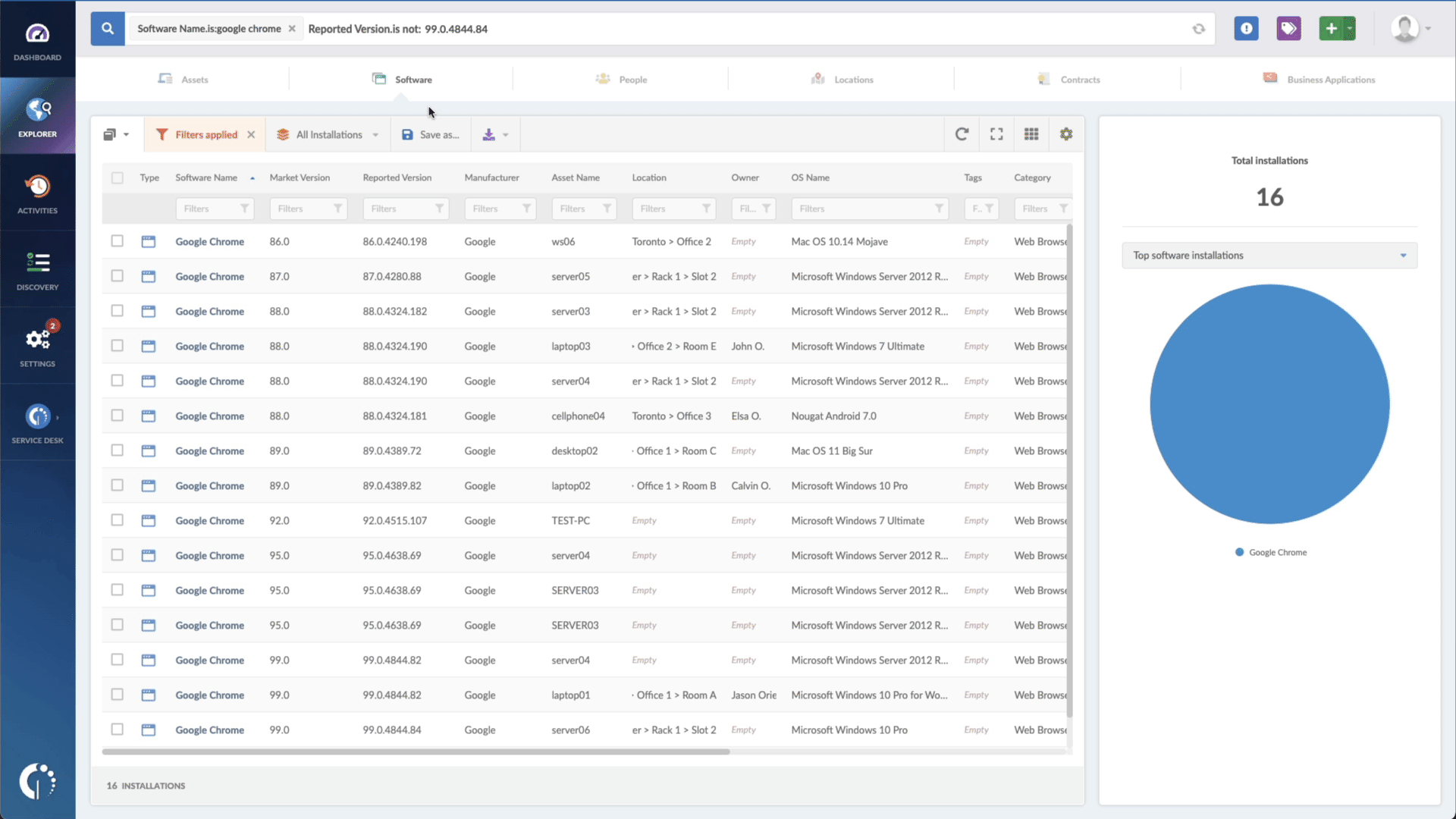
- Type in the Search bar “Software name, is:Microsoft Windows” to filter all Windows devices.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (Windows 10 version 22H2, released on October 18, 2022).
The bottom line
In summary, CVE-2021-43890 is a spoofing vulnerability in the Windows AppX Installer that can lead to potential data breaches or take control of your system. Microsoft has addressed this issue with a patch, which users should install by updating their Windows 10 systems.
InvGate Asset Management simplifies the process of identifying devices that still lack the security patch, making it easier for organizations to manage their patching efforts. Request a 30-day free trial and try it for yourself.
















