LDAP or Lightweight Directory Access Protocol is one of the oldest and most popular protocols used to retrieve information from directory services, authenticate users, and build applications that don’t compare on security or speed. It’s one of the protocols to manage assets and data over a network and provides secure access to them.
So what is LDAP? How does it work? What are some of the best practices while using the LDAP protocol? Let’s have a look.
What is the LDAP protocol?
LDAP is one of the core protocols for developing internet applications. The protocol was designed to access and maintain directory services over the internet.
LDAP is an alternative to the Directory Access Protocol (DAP) created around 1993. The DAP was commonly used to access the X.500 directory services using the OSI stack, but this was found to be network and hardware intensive. The LDAP protocol was developed to be a lightweight version that required less network bandwidth and utilized the TCP/IP stack.
There are three versions of the LDAP protocol. The latest version is the LDAP V3, adding stronger authentication and data security by integrating the Simple Authentication and Security Layer. LDAPv3 also added extensibility to the protocol.
Most vendor directory services support LDAP, and it acts as just the language with which users can access information from the directory.
The protocol does not synchronize between the user (client) and server users. The LDAP protocol doesn’t specify when or in which order the server returns responses to the queries. And the client doesn’t have to wait for a response before sending another question.
What are the different types of data that can be accessed using LDAP?
An LDAP directory server follows a tree configuration. Each entry may have multiple attributes, each with its object identification.
The data stored can be:
- Descriptive (with multiple data points like: name, date, location, etc., to define an asset).
- Static (not a lot of change in this data, just small changes every once in a while. It can also be valuable business data that may be accessed and changed frequently).
The directory schema defines these contents, which explains how to store all data and the rules governing how it’s stored. It defines rules regarding attributes and object identifiers and compares against different feature values for specific attribute types.
Elements Stored in the Data Directory
The first element is the entry, which could be the user's name, a resource, and a block in the database. You can picture it like the names in your address book; each term and their phone number, house No, email ID, etc. Each entry refers to its unique identifier called the Distinguished Name or DN, which identifies the position of the entry in the tree.
The next element is the attribute. Attributes are attached to entries, and each may have more than one attribute. There are different types of attributes as defined in the schema, and all of these attribute types have an object identifier.
The next element is the object class. The object class is a collection of attributes and indicates the type of object. For example, you may define an object class for people, which can have attributes like age, gender, email ID, etc., or you can specify one for printers, which can have attributes like date of purchase, manufacturer name, etc. Every entry has an object class.
How does the LDAP process work?
The process is relatively straightforward; the client connects to the server through TCP and UDP port 389 or to port636 for LDAP over SSL/TLC. The client sends a query to the server, and the server sends a response back. Once it's over, the connection ends.
Before the client can perform server operations, they authenticate. In the most direct method, a BIND operation is performed, where the client sends its username and password to the server, and the server verifies it. But with v3, you can go for an implementation that uses SASL authentication.
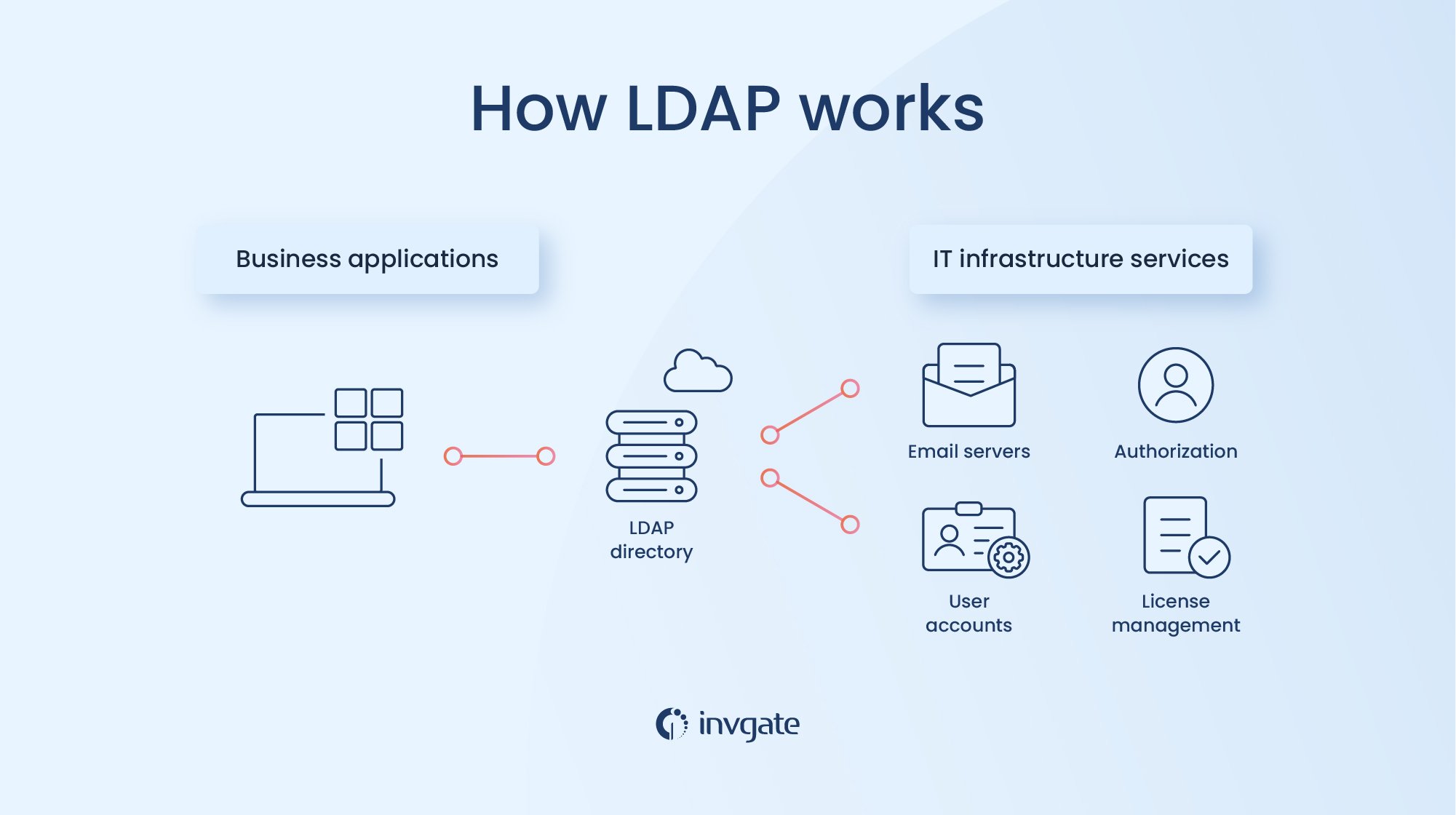
There are many operations that clients can perform using LDAP. We describe some of them below.
LDAP operations
- Add: The operation adds a new entry to the directory database. The server doesn’t allow duplicate entries. Instead sends a “name already exists” notification if you attempt to add a new entry with a name already in the directory.
- Bind: As discussed above, the BIND operation authenticates a client with the LDAP server.
- Delete: The delete request deletes an entry. But in most cases, this operation deletes only the entries without any subordinates.
- Search and compare: The operation does what the name suggests. You can set various parameters for this operation, such as where to search for and other filters.
- Modify: The modify operation changes existing entries. Besides these, some extended functions were not part of the original specification.
- StartTLS: With this tool, we start TLS security on the connection for data security.
- Abandon: Used to abandon a specific request sent to the server.
- Unbind: Unbind is not related to the BIND operations: it closes the connection. It lets the server know that the client is no longer interested and that it can reallocate its resources elsewhere.
What is the difference between Active Directory and LDAP?
Active Directory is a directory service from Microsoft for Windows domain networks. It stores information about various devices and other assets on the web, and administrators use this to manage permissions and access to network assets. The active directory stores information as objects and their attributes.
The active directory uses LDAP as one of the protocols and other protocols like DNS and Kerberos. Kerberos helps with authentication, and LDAP retrieves information. The directory service uses DNS for locating active directory domain controllers (the servers that run the active directory domain service).
LDAP is not limited to the active directory alone. We can use it with any other directory service from different vendors supporting it.
Best practices for using the LDAP protocol
The LDAP protocol sends all communication between the client, server, and third parties in plain text. Anyone can access all of this information. Encryption with TLS in LDAP will not be enough. So it's essential to enable encryption with TLS in LDAP, SSL will not be enough. The best solution is to set up LDAP servers, so they don’t accept operations before StartTLS.
It’s also vital to sanitize user inputs or LDAP queries before passing them onto the server. LDAP injection attacks are a known vulnerability, and attackers may be able to bypass authentication, access sensitive information, and even modify them.
It’s also important to follow other security principles, like never reusing identifiers, using a password manager, hashing the passwords, and never storing them in plain text.
Glossary of terms used with the LDAP protocol
Here are some of the other terms used in association with the protocol.
- DIT: A hierarchical structure to represent entries using their distinguished name.
- Alias: An entry in the DIT that refers to another entry.
- Dereferencing: Following an alias to find the entry.
- Directory server agent: It is an application that uses LDAP to access directory data by a client.
- RDN: RDN or Relative Distinguished Name refers to any attribute name and value pair. A DN is usually composed of one or more RDNs.
- SASL: SASL or Simple Authentication Security Layer integrates other authentication mechanisms such as Kerberos not directly built into the protocol.
Frequently Asked Questions
When can you use LDAP?
LDAP is commonly used to retrieve information from directory services and authenticate users before letting them access the stored information. It’s helpful in situations where you want high-speed searches on large databases containing small pieces of data. The protocol is optimized to be good at reading data in exchange for write speeds, so if you frequently update the data, LDAP may not be the best option.
What is the difference between LDAP and SSO?
LDAP is a protocol that stores and retrieves data quickly. The data gets stored as entries, attributes, and attribute values. The protocol manages access to network assets.
SSO or single sign-on is any system that allows users to access multiple systems with one single authentication.
LDAP helps with single sign-on, but that’s not its only purpose.
What is the difference between LDAP and Kerberos?
LDAP stores and locates information about various objects, such as people or network assets. It manages access to different assets in a network.
Kerberos is a protocol for authenticating clients and servers using a secret cryptographic key. Kerberos is often used as an authentication method instead of LDAP authentication while using the LDAP protocol.