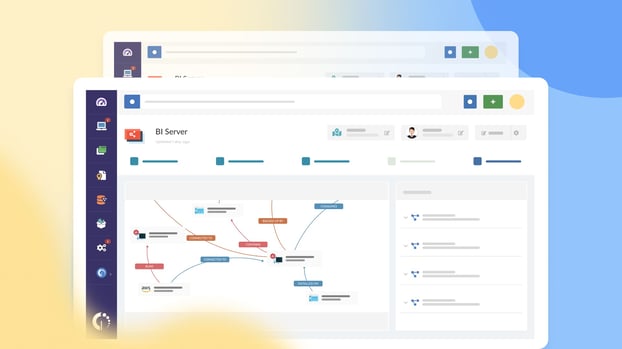
Configuration Management tools can be complex to understand and navigate, especially when you're in the process of selecting one that aligns with your organization's goals.
The market offers many options. So, how do you choose the right one? It all starts with solid research. Combined with our expertise in IT Asset Management (ITAM) and Configuration Management (CM), we’ve put together a list of the best CM tools for 2025.
In this blog post, we’ll break them down in detail, helping you find the one that best fits your needs and your team’s capabilities.
The 12 best Configuration Management tools for 2025
This list includes a mix of Configuration Management software, ITAM and ITSM platforms with CMDB features, and orchestration solutions — reflecting the different ways teams manage infrastructure today.
We also considered pricing and accessibility, balancing open-source, commercial, and hybrid tools to fit various needs and budgets. This is our list:
- InvGate Asset Management.
- Chef Infra.
- SysAid.
- Puppet.
- Ansible.
- Rudder.
- Kubernetes.
- Ninja One.
- CFengine.
- Auvik.
- Octopus Deploy.
- Salt.
| Tool | Best for | Deployment | Pricing | Fre trial |
| InvGate Asset Management | Asset + Configuration Management in one | Cloud & On-premise | Per node (from $0.21) | 30-day free trial |
| Chef Infra | IaC with compliance focus | Cloud & On-premise | $59–$189 per node/year | Yes (on request) |
| SysAid | ITSM + CMDB in one platform | Cloud & On-premise | Custom | Demo |
| Puppet Enterprise | Declarative automation at scale | Cloud, On-premise, Hybrid | Custom | Yes (10 nodes) |
| Ansible | Agentless automation and ease of use | Cloud & On-premise | Custom (enterprise); Free (open-source) | Yes |
| Rudder | Compliance-focused CM with patching | Cloud & On-premise | Custom | Yes |
| Kubernetes | Container orchestration with CM aspects | Cloud, On-premise, Hybrid | Free (infra costs apply) | - |
| NinjaOne | Endpoint config & monitoring for MSPs | Cloud | $1.50–$3.75 per device/month | 14-day free trial |
| CFEngine | Lightweight, scalable CM | Cloud & On-premise | Custom (Enterprise); Free (Community) | Yes |
| Auvik | Network config backup & visibility | Cloud | Custom | 14-day free trial |
| Octopus Deploy | Config + deployment orchestration | Cloud & On-premise | $360–$23,400/year | 30-day free trial |
| Salt | Real-time CM + remote execution | Cloud & On-premise | Custom (Enterprise); Free (Community) | Yes |
What are Configuration Management tools?
To understand what a Configuration Management tool is and what it does, you first need to understand Configuration Management. Simply put, CM is a process that involves managing and maintaining digital systems, hardware, or software to achieve the desired level of performance and functionality.
Configuration Management tools are software solutions that help you achieve this with several advantages, making the job easier, more effective, and more accurate.
How to choose a Configuration Management system
Beyond automating configurations, the ideal tool should offer robust monitoring, alerting, and reporting capabilities to keep teams informed and proactive. Usability also matters, since tools with intuitive interfaces and short learning curves can streamline workflows and encourage faster adoption.
It’s also important to look at features and integrations. Strong automation, customizable dashboards, and seamless compatibility with cloud providers (like AWS or Azure) and collaboration tools (like Jira or Slack) are essential.
Configuration Management vs. ITAM software
Some ITAM tools offer built-in Configuration Management features, making them a solid choice for organizations seeking an integrated solution. While they may lack the depth of dedicated CM tools, they combine asset tracking, Asset Lifecycle Management, and compliance in one platform.
If your priority is deep configuration control, go for a specialized CM tool. But if you're focused on asset visibility, cost tracking, and compliance, an ITAM solution with CM capabilities (like a CMDB) may be all you need.
#1. InvGate Asset Management
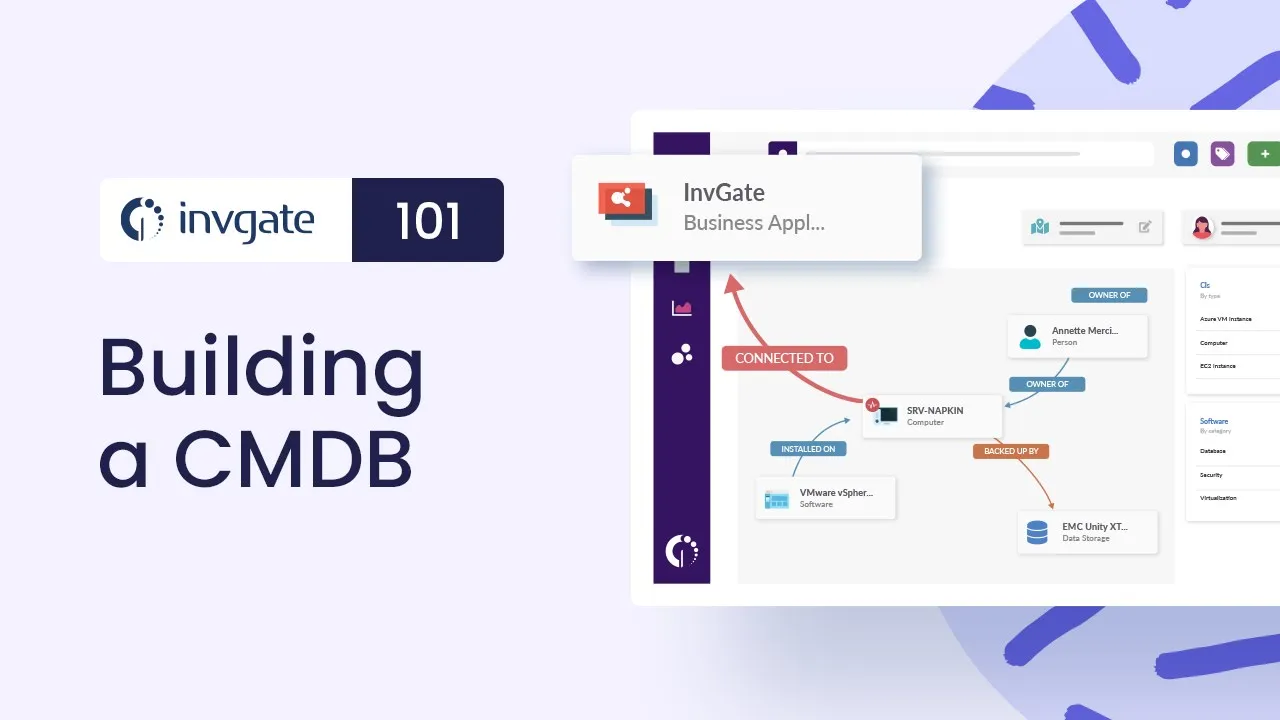
So, here’s the thing: while InvGate Asset Management is primarily an ITAM tool, it also provides key CM capabilities — especially when it comes to building and maintaining a Configuration Management Database (CMDB).
And that’s a great place to start your Configuration Management journey. You can start your free 30-day trial today!
The best part of choosing an ITAM tool as your Configuration Management software is that you get a complete set of capabilities to manage your IT infrastructure more effectively.
InvGate Asset Management features for Configuration Management
- Build a CMDB — Set up a CMDB by creating an asset inventory, defining Business Applications, and using CMDB visualizations to monitor your IT infrastructure in real-time.
- Track CI changes — Monitor Configuration Item lifecycles using agent-based and agentless discovery. Visual maps, audit trails, and asset health rules (green/yellow/red) help detect issues and reduce downtime.
- Automated asset discovery — Populate the CMDB using multiple methods, including network scanning, file import, API, and the InvGate Agent.
- Smart Tags and health rules — Automatically tag assets based on specific behaviors, conditions, or statuses to trigger alerts and actions.
- Visual relationship mapping — Understand interdependencies between assets, systems, and applications using dynamic, interactive maps.
- Integration with ITSM tools — Seamlessly connect with InvGate Service Management to link CIs with incidents, problems, changes, and service requests.
- Change tracking and historical data — Record and visualize configuration changes over time to support audits, impact assessments, and rollback strategies.
- Custom dashboards and reports — Build tailored views to monitor Business Applications, CI status, recent changes, and system health.
InvGate Asset Management software pros
- No-code and intuitive setup suitable for technical and non-technical users
- Agent-based and agentless discovery options
- Strong visual interface to monitor dependencies and changes
- Tight integration with ITSM processes (e.g., Change Management, Incident Management)
- Ideal for organizations looking for both Asset and Configuration Management in one tool
- Cloud and on-premise deployment options
InvGate Asset Management software cons
- Not a dedicated Configuration Management tool for CI/CD or infrastructure-as-code
- Some advanced CMDB visualizations may require asset tagging discipline
- Fewer third-party CM integrations compared to tools like Ansible or Puppet
InvGate Asset Management software reviews and comments
- Gartner Peer Insights: 4.7 out of 5 – IT Asset Management category
- G2: 4.6 out of 5 – Highly rated for ease of use and support
- Capterra: 4.7 out of 5
"We have had an overall very positive experience with InvGate. We implemented both Asset Management and Service Management a little over two years ago. The product is simple to setup and integrate with. Their support has been responsive, and the account managers are very attentive to our specific use cases and needs."
Gartner Peer Insights reviewer
InvGate Asset Management software pricing
Plans start at $0.21 per node/month (billed annually, from $1,250/year) for up to 500 nodes.
Larger environments pay $0.38 per node/month, and custom Enterprise plans are available. A 30-day free trial is offered with cloud and on-premise options.
#2: Chef Infra

Chef Infra is a Configuration Management tool developed by Chef Software, Inc. (now part of Progress Chef Software) and first released in 2009. It’s best known for its infrastructure-as-code approach to automating the configuration, deployment, and management of servers — whether on-premises, in the cloud, or hybrid environments.
What sets Chef Infra apart is its declarative model combined with Ruby-based DSL, and its strong compliance and auditing capabilities, making it ideal for large-scale enterprise environments with strict configuration policies.
Chef Infra features for Configuration Management
- Infrastructure as Code (IaC) — Define infrastructure configurations in code using a Ruby-based domain-specific language (DSL) for reusable and scalable automation.
- Policy-based configuration — Apply defined configurations consistently across environments using Chef’s policyfiles and cookbooks.
- Test-driven development — Integrates with InSpec and Test Kitchen for testing configurations before deployment.
- Automated compliance enforcement — Chef Infra integrates with Chef Compliance Phase to detect and remediate violations automatically.
- Agent-based execution — Chef runs on a pull model with an agent installed on each node, ensuring that each system remains independently updated.
- Multi-platform support — Manages Windows, Linux, macOS, and cloud-based infrastructure (AWS, Azure, GCP).
- Integration with DevOps tools — Seamlessly integrates with tools like GitHub, Jenkins, Terraform, and container ecosystems.
Chef Infra pros
- Highly scalable and reliable in complex, distributed environments
- Powerful policy enforcement with automated compliance features
- Strong integration ecosystem (including AWS, Azure, Google Cloud, Splunk, New Relic, etc.)
- Declarative approach allows for precise, repeatable configurations
- Available via cloud marketplaces (AWS and Azure) for simplified procurement
- Extensive documentation and enterprise support from Progress
Chef Infra cons
- Steep learning curve due to Ruby-based syntax and complexity of setup
- Initial configuration and cookbook creation can be time-consuming
- Resource-heavy for smaller teams or environments
- Declining popularity compared to simpler tools like Ansible
Chef Infra reviews and comments
Progress Chef software has a 4.2/5 stars in G2.
“I have used Chef in my previous company and have setup chef work station in my local, which was simple and it helps me to make some configuration changes without any downtime. It pulls configurations from the central server to the worker node.”
G2 reviewer
Chef Infra pricing
Chef offers cloud-based and self-managed pricing tiers based on the number of nodes and features included:
- Business Plan – $59 per node per year — For organizations that need automation and orchestration of infrastructure management tasks.
- Enterprise Plan – $189 per node per year — Designed for organizations scaling DevOps automation, orchestration, and auditing.
- Enterprise Plus – Custom pricing — Tailored for security-focused organizations with advanced compliance requirements.
#3: SysAid
 SysAid is an ITSM platform developed by SysAid Technologies Ltd., founded in 2002. While primarily known for its help desk and Service Management capabilities, SysAid includes a built-in CMDB and Configuration Management features, making it a strong option for organizations looking for an all-in-one ITSM+CM solution.
SysAid is an ITSM platform developed by SysAid Technologies Ltd., founded in 2002. While primarily known for its help desk and Service Management capabilities, SysAid includes a built-in CMDB and Configuration Management features, making it a strong option for organizations looking for an all-in-one ITSM+CM solution.
What sets it apart is its visual CI mapping, workflow automation, and asset discovery capabilities bundled in a single platform, along with a flexible licensing model.
SysAid features for Configuration Management
- CMDB with relationship mapping — Visualize how Configuration Items (CIs) are linked to services, users, and other assets.
- Automated asset discovery — Detects devices and systems in your network to populate the CMDB automatically.
- CI health indicators — CIs are color-coded (green/yellow/red) based on status or alerts, helping identify potential issues quickly.
- Root cause analysis — Built-in tools to help identify the source of incidents by mapping them to affected CIs.
- Change and incident linkage — Link changes, incidents, and problems directly to CIs for traceability and audit readiness.
- Service catalog and workflow integration — Configuration Management ties into automated workflows and the self-service portal.
SysAid pros
- Centralized ITSM and Configuration Management platform
- Visual dependency mapping of assets and services
- Strong automation engine for repetitive tasks
- Integrated CMDB simplifies audit and compliance workflows
- Flexible deployment: available both on-premise and in the cloud
- Broad feature set included in standard pricing tiers
SysAid cons
- User interface can feel outdated or unintuitive
- Mobile experience lacks some functionality
- CMDB customization may be limited compared to dedicated CM tools
- Performance can slow under high data loads or larger implementations
SysAid reviews and comments
- Gartner Peer Insights: 4.5 out of 5 stars
- G2: 4.5 out of 5 stars
- Capterra: 4.5 out of 5 stars
"Sysaid is a robust ITSM tool, offering a lot of features for ticketing, asset management and process automation. It is highly customizable and offers a wide range of integrations, intital setup and performan at scale can be performed."
Gartner Peer Insights reviewer
SysAid pricing
SysAid offers three main pricing tiers:
- Help Desk: Includes ticketing, self-service portal, service catalog, and basic asset management
- ITSM: Adds CMDB, workflow automation, integrations, and company management
- Enterprise: Offers unlimited automation rules, premium services, and advanced customization
Pricing is not publicly listed. SysAid offers live demos upon request.
#4: Puppet Enterprise
 Puppet Enterprise is a Configuration Management tool created by Puppet, Inc., founded in 2005. Known for its declarative language model and scalability, Puppet enables teams to automate infrastructure provisioning, enforce consistent system configurations, and maintain compliance across complex, hybrid environments.
Puppet Enterprise is a Configuration Management tool created by Puppet, Inc., founded in 2005. Known for its declarative language model and scalability, Puppet enables teams to automate infrastructure provisioning, enforce consistent system configurations, and maintain compliance across complex, hybrid environments.
What sets Puppet apart is its robust automation at scale, strong ecosystem of modules, and ability to continuously monitor and remediate configuration drift.
Puppet Enterprise features for Configuration Management
- Declarative configuration language — Define desired infrastructure states using Puppet DSL or Ruby.
- Configuration drift correction — Automatically detects and remediates deviations from the defined state.
- Node classification and environment segmentation — Manage configurations by group, environment, or role.
- Reusable modules and manifests — Organize code for scalable and maintainable infrastructure management.
- Integration with third-party tools — Connect with ServiceNow, Terraform, Red Hat Satellite, AWS, Azure, Splunk, and more.
- Compliance enforcement and reporting — Monitor system compliance through reports and dashboards.
Puppet Enterprise pros
- Highly scalable for enterprise and multi-cloud environments
- Strong community support and pre-built modules (via Puppet Forge)
- Efficient configuration enforcement and drift correction
- Works well in complex, heterogeneous environments
- Open-source and enterprise versions available
- Mature integrations with key DevOps and ITSM tools
- Deployment options include on-premise, cloud, or hybrid environments
Puppet Enterprise cons
- Steep learning curve, especially for those unfamiliar with its DSL
- Resource-intensive setup and infrastructure requirements
- Declining open-source community engagement in recent years
- User interface may feel dated or unintuitive to some users
Puppet Enterprise reviews and comments
- G2: 4.2 out of 5 stars
- Gartner Peer Insights: 4.0 out of 5 stars (Continuous Configuration Automation Tools)
- Capterra: 4.4 out of 5 stars
Puppet Enterprise pricing
Puppet offers two main versions:
- Open Source Puppet — Free version with core functionality and community support
- Puppet Enterprise — Paid version with advanced features, commercial support, and automation capabilities
Enterprise pricing is not publicly available. Prospective customers must request a custom quote based on node count and feature needs. Puppet Enterprise is also available through cloud marketplaces like AWS and Azure.
Puppet provides a free trial of its enterprise edition (10 nodes limit) and a demo upon request.
#5: Ansible
Ansible is an open-source IT automation and Configuration Management tool developed by Michael DeHaan and acquired by Red Hat in 2015. It is best known for its agentless architecture and human-readable YAML playbooks, which simplify infrastructure automation, orchestration, and application deployment.
What sets Ansible apart is its ease of use, minimal dependencies, and suitability for teams of all sizes looking to automate repetitive tasks without deep coding expertise.
Ansible features for Configuration Management
- Agentless architecture — Uses SSH or WinRM to connect to managed nodes without requiring agents.
- YAML-based playbooks — Declarative configuration files written in YAML make automation tasks easy to read and modify.
- Push and pull execution modes — Offers flexibility to push changes manually or pull them on a schedule.
- Modules for everything — Extensive module library to automate networking, security, cloud provisioning, and configuration tasks.
- Inventory Management — Supports dynamic inventories and multiple environment management.
- Ansible Tower (now part of Red Hat Ansible Automation Platform) — Provides a UI, RBAC, logging, and scheduling for enterprise users.
Ansible pros
- Simple to learn with low entry barrier
- Agentless approach reduces resource and maintenance overhead
- Highly extensible with hundreds of built-in modules
- Strong support for cloud providers (AWS, Azure, GCP) and hybrid environments
- Seamless integration with CI/CD pipelines and DevOps tools
- Large open-source community and frequent updates
Ansible cons
- Lacks built-in CMDB or advanced Configuration Item tracking
- GUI (Tower) is only available in the enterprise edition
- Limited real-time state validation (compared to pull-based tools like Puppet or Chef)
- Can get complex when scaling to large environments without Tower
- Some third-party integrations may require custom setup or additional scripting
Ansible reviews and comments
- G2: 4.6 out of 5 stars (Red Hat Ansible Automation Platform)
- Gartner Peer Insights: 4.6 out of 5 stars (under DevOps platforms)
- Capterra: 4.6 out of 5 stars
Ansible pricing
Ansible is available in two versions:
- Ansible Core (Open Source) — Free and community-supported
- Red Hat Ansible Automation Platform — Enterprise version with additional tools like Ansible Tower, Automation Hub, and certified content
Pricing for the enterprise version is not publicly listed. Organizations must contact Red Hat for a custom quote based on usage, nodes, and support needs.
Red Hat offers a free trial of the Ansible Automation Platform, as well as guided demos and documentation. Deployment is possible on-premise, in cloud environments, or hybrid setups.
#6: Rudder
 Rudder is an open-source Configuration Management and continuous compliance tool developed by Normation, a French software company, originally launched in 2011. Built on top of CFEngine, Rudder is known for combining configuration automation with compliance auditing, offering a centralized interface to manage large infrastructures.
Rudder is an open-source Configuration Management and continuous compliance tool developed by Normation, a French software company, originally launched in 2011. Built on top of CFEngine, Rudder is known for combining configuration automation with compliance auditing, offering a centralized interface to manage large infrastructures.
What makes Rudder stand out is its multi-OS Patch Management, real-time policy enforcement, and its ability to continue applying configurations even during network failures, ensuring high availability and system integrity.
Rudder features for Configuration Management
- Centralized policy enforcement — Define, apply, and monitor configuration policies across all nodes from a unified web interface.
- Agent-based execution — Lightweight agents continuously enforce policies and apply configurations even if disconnected from the main server.
- Multi-platform support — Compatible with Linux, Windows, AIX, Solaris, and more.
- Continuous compliance monitoring — Real-time auditing of configuration states with detailed reporting and logs.
- Patch Management system — Supports multi-OS patch deployment with visibility over campaign results.
- Custom rules and templating — Create reusable configuration templates for scalable deployments.
Rudder pros
- Strong focus on continuous compliance and security hardening
- Resilient agent behavior enables offline policy enforcement
- Built-in patch management for multiple OS environments
- Easy-to-use web UI with visual feedback and logs
- Open-source core with transparent pricing
- Active community and commercial support available
- Integration with IT tools like ServiceNow, Zabbix, ELK, Centreon, and Hashicorp Vault
Rudder cons
- Advanced configurations may require technical expertise
- Smaller community compared to Ansible or Puppet
- Visual configuration editor could be more intuitive
- UI responsiveness can vary with large environments
- Fewer modules or plugins compared to more mature ecosystems
Rudder reviews and comments
- G2: 4.3 out of 5 stars
“Rudder provides a very intuitive user interface with comprehensive data governance features. It adds emphasis on collaboration and integration with existing tools along with scalable performance."
G2 reviewer
Rudder pricing
Rudder offers two main paid editions, both based on custom annual per-node pricing:
- Rudder Enterprise — Includes Configuration Management, Patch & Vulnerability Management or policy compliance. Comes with 9 months of security patches and standard support.
- Rudder Corporate Security Suite — Full-featured version that includes everything in Rudder Enterprise, plus advanced security configuration, Patch & Vulnerability Management, and policy compliance. Offers unlimited premium support and dedicated customer success resources.
Both editions require you to contact the vendor for a quote. A free trial is also available upon request.
#7: Kubernetes
 Kubernetes (also known as K8s) is an open-source container orchestration platform originally developed by Google in 2014 and now maintained by the Cloud Native Computing Foundation (CNCF). It’s widely recognized for automating deployment, scaling, and management of containerized applications.
Kubernetes (also known as K8s) is an open-source container orchestration platform originally developed by Google in 2014 and now maintained by the Cloud Native Computing Foundation (CNCF). It’s widely recognized for automating deployment, scaling, and management of containerized applications.
While Kubernetes is not a traditional Configuration Management tool, it offers powerful declarative configuration and infrastructure automation, making it a valuable part of modern DevOps and cloud-native strategies.
Kubernetes features for Configuration Management
- Declarative configuration — Use YAML manifests to define desired states for applications, services, and infrastructure.
- State reconciliation — Continuously ensures the cluster state matches the defined configuration.
- Resource controllers — Automate updates, rollbacks, and monitoring of system changes across containers and pods.
- ConfigMaps and Secrets Management — Store and manage environment-specific configuration settings securely.
- Infrastructure as Code (IaC) compatibility — Easily integrates with tools like Helm, Kustomize, and Terraform.
- Built-in monitoring and health checks — Ensure nodes, services, and workloads remain operational and compliant.
Kubernetes software pros
- Extremely scalable and suited for microservices architecture
- Strong automation and self-healing capabilities
- Vendor-neutral and open-source with wide industry adoption
- Integrates seamlessly with CI/CD and DevOps pipelines
- Rich ecosystem (Helm, Istio, Prometheus, Argo CD, etc.)
- Declarative approach aligns with modern configuration best practices
- Deployment options include on-premise, public cloud, private cloud, and hybrid environments
Kubernetes software cons
- Not purpose-built for traditional CMDB or ITIL-based Configuration Management
- Steep learning curve for newcomers
- Complex setup and management (especially without managed services)
- Requires external tools for visualization, access management, and auditing
- Overkill for simple infrastructure or non-containerized environments
Kubernetes pricing
Kubernetes itself is 100% free and open source, but running it has associated infrastructure and operational costs:
- Self-hosted (on-premise or cloud VM): Free software, but you manage and maintain it
- Managed services (e.g., Google Kubernetes Engine, Amazon EKS, Azure AKS): Pay-per-use pricing based on cloud provider infrastructure and node usage
There’s no free trial or demo for Kubernetes itself, but managed services often offer free credits (e.g., Google Cloud’s $300 free credit for new users).
#8: NinjaOne
 NinjaOne (formerly known as NinjaRMM) is an Endpoint Management and remote monitoring platform developed by NinjaOne, Inc., founded in 2013.
NinjaOne (formerly known as NinjaRMM) is an Endpoint Management and remote monitoring platform developed by NinjaOne, Inc., founded in 2013.
While not a dedicated Configuration Management tool in the traditional ITIL sense, NinjaOne stands out for its agent-based automation, Patch Management, and remote configuration features, making it especially valuable for MSPs and IT teams managing distributed environments.
NinjaOne features for Configuration Management
- Automated Patch Management — Automatically deploys OS and third-party software patches across Windows, macOS, and Linux endpoints.
- Policy-based endpoint configuration — Standardizes device setup using automation rules and scripting.
- Real-time asset inventory — Offers full visibility into hardware, software, and system configurations.
- Remote access and scripting — Supports live command-line execution and custom scripts for on-demand configuration.
- Alerting and monitoring — Detects configuration drift, unauthorized changes, and system health issues.
- API and integrations — Enables integration with ticketing systems, documentation tools, and automation platforms.
NinjaOne pros
- Cloud-native with no infrastructure requirements
- Extremely user-friendly interface and fast deployment
- Strong automation capabilities for patching and endpoint setup
- Excellent support and onboarding services
- Ideal for small and mid-sized teams, as well as MSPs
- Broad integration options (e.g., ServiceNow, TeamViewer, Acronis, ConnectWise)
- Deployment options: 100% cloud-based, agent-based model
NinjaOne cons
- Pricing isn’t transparent and may be high for smaller organizations
- Reporting and dashboard customization can be limited
- Backup module may require external tools for full functionality
- More focused on endpoint management than traditional CMDB functions
NinjaOne reviews and comments
- Gartner: 4.9 out of 5 (in Endpoint Management Tools category)
- G2: 4.7 out of 5
- Capterra: 4.7 out of 5
“Ninja is the best RMM we have ever used, it's fast, very customizable, and the UI is easy to understand and modern. It has made managing systems mostly effortless and much more efficient than our previous system.”
Capterra reviewer
NinjaOne pricing
NinjaOne follows a per-device pricing model that scales with volume:
- Pricing starts as low as $1.50 per device/month for customers with 10,000+ endpoints.
- Smaller environments (e.g., 50 endpoints) may pay up to $3.75 per device/month.
- Pricing varies depending on region, product mix, and active promotions or commitments.
- There are no hidden fees — training, implementation, and support are free and unlimited.
To get exact pricing, organizations must request a custom quote. No public pricing calculator is available. A 14-day free trial is available upon request.
#9: CFEngine
 CFEngine is an open-source Configuration Management tool originally created in 1993 by Mark Burgess, and later commercialized by Northern.tech.
CFEngine is an open-source Configuration Management tool originally created in 1993 by Mark Burgess, and later commercialized by Northern.tech.
It’s known for being lightweight, scalable, and self-healing, with one of the smallest footprints in the market — capable of managing hundreds of thousands of nodes with minimal overhead.
CFEngine features for Configuration Management
- Declarative language — Uses a promise-based model to define desired system states.
- Self-healing automation — Agents continuously enforce configurations, even if disconnected from the network.
- Compliance and auditing — Includes built-in tools to track policy compliance and report on deviations.
- Cross-platform support — Compatible with most Linux/Unix systems and Windows.
- Scalability — Efficient enough to handle very large and distributed infrastructures.
- API access — Enables automation and integration with external tools or CI/CD pipelines.
CFEngine pros
- Extremely low resource usage, ideal for constrained environments
- Mature and stable, with decades of development behind it
- Ensures configuration consistency with autonomous agents
- Open-source Community Edition available
- Highly scalable — used in environments with over 1 million nodes
- Offers both GUI and CLI for flexibility
CFEngine cons
- Steeper learning curve due to its unique language and architecture
- Smaller user community compared to newer tools like Ansible or Puppet
- Limited out-of-the-box integrations
- Somewhat dated UI in the Enterprise edition
- May be overkill for small teams or simple environments
CFEngine pricing
CFEngine offers two editions:
- Community — Free and open source (licensed under GNU GPL).
- Enterprise — Includes all features under a single commercial license. Pricing is custom per-node and includes Mission Portal, reporting, compliance tools, and multi-platform support.
The Enterprise edition is offered under a custom per-node annual license. You must contact CFEngine for pricing details. A free trial is available for up to 25 hosts, with full feature access.
#10: Auvik
 Auvik is a cloud-based Network Monitoring and Management platform developed by Auvik Networks Inc., founded in 2011 in Canada. While it's not a traditional Configuration Management tool, Auvik stands out for its automated network discovery, documentation, and configuration backup capabilities.
Auvik is a cloud-based Network Monitoring and Management platform developed by Auvik Networks Inc., founded in 2011 in Canada. While it's not a traditional Configuration Management tool, Auvik stands out for its automated network discovery, documentation, and configuration backup capabilities.
It’s particularly valuable for organizations looking to maintain network infrastructure visibility and quickly respond to configuration drift or device failures.
Auvik features for Configuration Management
- Automated network discovery — Continuously maps and documents all network-connected devices.
- Configuration backup and restore — Automatically backs up configurations of supported network devices and allows fast restoration.
- Real-time network monitoring — Provides alerts and visibility into performance and device status.
- Policy-based alerting — Customizable thresholds and alerts for network events and changes.
- Multi-vendor support — Works with a wide variety of switches, firewalls, routers, and wireless controllers.
- Network topology visualization — Dynamic maps of your network with drill-down access to each node.
Auvik pros
- Cloud-based and easy to deploy with minimal setup
- Strong in network-specific configuration backup and visibility
- Highly visual interface and dynamic topology mapping
- Excellent for MSPs or distributed networks
- Supports a wide variety of network device vendors
- Integrates with tools like ConnectWise, Autotask, ServiceNow, Slack, and PagerDuty
Auvik cons
- Limited outside of network infrastructure (not for servers or endpoints)
- Some advanced features locked behind higher pricing tiers
- No agentless discovery—requires installation of collectors
- Lacks deep Configuration Management features for non-network devices
- Can be expensive for small teams
Auvik reviews and comments
- Gartner Peer Insights: 4.5 out of 5 stars
- G2: 4.5 out of 5 stars
- Capterra: 4.7 out of 5 stars
“Auvik helped me get insight into my network and what devices were connected. It took time to locate each and every device manually. Auvik makes things simple and easy.”
Gartner Peer Insights reviewer
Auvik pricing
Auvik follows a quote-based pricing model based on the number of core network infrastructure devices (e.g., switches, routers, firewalls, and controllers). Other devices like wireless access points, printers, and UPS units are monitored for free and do not count toward licensing.
Additional optional add-ons are available for deeper server and endpoint monitoring.
Auvik is offered exclusively as SaaS (software-as-a-service) — no perpetual license is available.
- Free trial: 14-day trial available — no credit card required, all features included.
- Volume discounts: Yes, available.
- Pricing: Must request a quote directly.
#11: Octopus Deploy
 Octopus Deploy is a Continuous Delivery automation tool developed by Octopus Deploy Pty Ltd., founded in 2012 in Australia. While not a traditional Configuration Management platform, it stands out for orchestrating infrastructure and application deployments across multiple environments.
Octopus Deploy is a Continuous Delivery automation tool developed by Octopus Deploy Pty Ltd., founded in 2012 in Australia. While not a traditional Configuration Management platform, it stands out for orchestrating infrastructure and application deployments across multiple environments.
It’s widely used in DevOps workflows to manage complex configurations, releases, and deployments through automated pipelines.
Octopus Deploy features for Configuration Management
- Environment-specific configuration variables — Manage values uniquely per environment to prevent configuration drift.
- Configuration version control — Keep detailed history of changes to enable traceability and rollback.
- Infrastructure as code support — Integrates with Terraform, Pulumi, and scripting languages for configuration tasks.
- Multi-environment deployment — Customize and manage settings across dev, QA, staging, and production environments.
- Automated runbooks — Execute repeatable configuration operations on-demand or on schedule.
- CI/CD integrations — Connects with Jenkins, GitHub Actions, Azure DevOps, Bitbucket, and more.
Octopus Deploy pros
- Centralized configuration and deployment management across environments
- Seamless integration with CI/CD and IaC tools
- Highly customizable workflows with granular access control
- Clear visual interface for tracking deployment pipelines
- Strong versioning and rollback capabilities
Octopus Deploy cons
- Not a CMDB or discovery tool — focused on deployment-related configuration
- Learning curve for teams unfamiliar with CI/CD or infrastructure-as-code practices
- Some enterprise-grade features gated behind higher-tier pricing
- Can be expensive for smaller organizations with limited nodes
Octopus Deploy reviews and comments
- Gartner Peer Insights: 4.6 out of 5
- Capterra: 4.8 out of 5
"My overall experience with Octopus Deploy has been exceptionally positive. The platform streamlines deployment automation while maintaining robust security controls. I value it-based access control, audit logging capabilities, and integration with existing security tooling."
Gartner Peer Insights reviewer
Octopus Deploy pricing
Octopus Deploy offers both cloud-hosted and self-managed plans, priced annually based on project limits and features.
- Cloud plans range from $360/year (Starter, 10 projects) to $23,400/year (Enterprise, 100 projects) with advanced automation, support, and deployment tools.
- Self-managed plans start at $360/year (Starter) and go up to $14,400/year (Enterprise), offering similar tiered features and support levels.
All plans include a 30-day free trial with no credit card required.
#12: Salt
 Salt, also known as SaltStack, is a powerful open-source Configuration Management and remote execution tool developed by Thomas S. Hatch in 2011, and later acquired by VMware in 2020. It's designed for speed and scalability, offering real-time configuration enforcement and orchestration across massive infrastructures.
Salt, also known as SaltStack, is a powerful open-source Configuration Management and remote execution tool developed by Thomas S. Hatch in 2011, and later acquired by VMware in 2020. It's designed for speed and scalability, offering real-time configuration enforcement and orchestration across massive infrastructures.
What sets Salt apart is its high-speed remote execution engine and flexible architecture — supporting both agent-based and agentless setups. It's a popular choice for DevOps and infrastructure teams managing large, complex environments.
Salt features for Configuration Management
- Remote execution engine — Execute commands across thousands of systems in parallel using Salt’s fast communication protocol (ZeroMQ or RAET).
- Declarative Configuration Management — Define system states using YAML-based “SLS” (Salt State) files for repeatable, automated infrastructure setup.
- Event-driven automation — Built-in event bus allows automatic reactions to system changes, making Salt suitable for real-time remediation and orchestration.
- Agent and agentless modes — Offers flexibility to manage systems with or without installing a Salt Minion (agent).
- Role-based configuration targeting — Target nodes by roles, grains (metadata), or custom filters for granular control.
- Integration with external tools — Integrates with Git, VMware, OpenStack, AWS, Azure, Jenkins, and more for hybrid cloud automation.
- Built-in compliance and security scanning — Use Salt’s security modules to run audits and enforce compliance policies.
Salt pros
- Extremely fast and scalable for large infrastructures
- Flexible setup (agent or agentless) to fit different environments
- Strong automation and remote execution capabilities
- Active open-source community with frequent updates
- Event-driven model supports real-time remediation
- Integrates well with cloud providers and DevOps pipelines
Salt software cons
- Steep learning curve for new users due to YAML syntax and modular design
- Documentation can be inconsistent or overwhelming for beginners
- GUI (SaltStack Enterprise) requires a paid license
- Some community users report challenges with upgrade paths or backward compatibility
- Event system setup can be complex in hybrid environments
Salt reviews and comments
- Gartner Peer Insights: 3.8 out of 5
“While Saltstack is a straightforward automation tool that interacts with agents to deploy applications or execute automation steps, the Saltstack Enterprise (SSE) Web portal falls short in terms of efficiency. Troubleshooting through its job logs can be challenging.”
Gartner Peer Insights reviewer
Salt pricing
Salt is available in two main editions:
- Salt Open (Community Edition) — Free and open-source under the Apache 2.0 license. It includes core features like remote execution, state management, and event-driven automation.
- SaltStack Enterprise (now VMware Aria Automation Config) — The commercial version provides advanced GUI management, role-based access control, analytics, and premium support. Pricing is not publicly available and requires a custom quote from VMware.
Free trial: VMware offers a free trial of SaltStack Config (part of Aria Automation) upon request.
Conclusion
Choosing the right Configuration Management tool depends on your team’s goals, infrastructure complexity, and preferred level of automation.
Whether you're looking for deep CI/CD integration, real-time change tracking, or a unified platform that combines asset and configuration data, the tools listed above cover a wide range of use cases.
Be sure to evaluate features, ease of use, and scalability before making your final decision — and don’t hesitate to take advantage of free trials to see what works best in your environment.